Welcome back to the series of Deploying On AWS Cloud Using Terraform 👨🏻💻. In this entire series, we will focus on our core concepts of Terraform by launching important basic services from scratch which will take your infra-as-code journey from beginner to advanced. This series would start from beginner to advance with real life Usecases and Youtube Tutorials.
If you are a beginner for Terraform and want to start your journey towards infra-as-code developer as part of your devops role buckle up 🚴♂️ and lets get started and understand core Terraform concepts by implementing it…🎬
Let’s understand it in 2 scenarios
Create 5 IAM users and a Developer group, and align all users as part of this Developer Group.
Create IAM Policies and assign this to the Developer group.
🔎Basic Terraform Configurations🔍
As part of basic configuration we are going to setup 3 terraform files
1. Providers File:- Terraform relies on plugins called “providers” to interact with cloud providers, SaaS providers, and other APIs.
Providers are distributed separately from Terraform itself, and each provider has its own release cadence and version numbers.
The Terraform Registry is the main directory of publicly available Terraform providers, and hosts providers for most major infrastructure platforms. Each provider has its own documentation, describing its resource types and their arguments.
We would be using AWS Provider for our terraform series. Make sure to refer Terraform AWS documentation for up-to-date information.
Provider documentation in the Registry is versioned; you can use the version menu in the header to change which version you’re viewing.
provider "aws" {
region = "var.AWS_REGION"
shared_credentials_file = ""
}
2. Variables File:- Terraform variables lets us customize aspects of Terraform modules without altering the module’s own source code. This allows us to share modules across different Terraform configurations, reusing same data at multiple places.
When you declare variables in the root terraform module of your configuration, you can set their values using CLI options and environment variables. When you declare them in child modules, the calling module should pass values in the module block.
variable "AWS_REGION" {
variable "AWS_REGION" {
default = "us-east-1"
}
3. Versions File:- It’s always a best practice to maintain a version file where you specific version based on which your stack is testing and live on production.
terraform {
required_version = ">= 0.12"
}
Scenario 1:-Create 5 IAM users and a Developer group, and align all users as part of this Developer Group
Let’s create a variable to type a list to pass our user names for whom the IAM user profile needs to be created in AWS.
variable "usernames" {
type = list(string)
default = ["Dheeraj","Sandip","Avinash","Vishal","Sankalp"]
}
🔳 Resource
✦ aws_iam_user:- This resource is used to create an AWS IAM user.
🔳 Arguments
✦ name:- This is a mandatory argument to define user name as part of resource creation.
✦ count:- Variable to take the length of the user list and save it.
✦ element:- It’s an intrinsic function of terraform to retrieve a single element from a list.
resource "aws_iam_user" "userlist" {
count = "${length(var.username)}"
name = "${element(var.username,count.index )}"
}
🔳 Resource
✦ aws_iam_group:- This resource is used to create an AWS IAM group.
🔳 Arguments
✦ name:- This is a mandatory argument to define group name as part of resource creation.
resource "aws_iam_group" "dev_group" {
name = "Developer"
}
🔳 Resource
✦ aws_iam_user_group_membership:- This resource is used to associate AWS IAM users to single or multiple groups.
🔳 Arguments
✦ name:- This is a mandatory argument to define this group membership association.
✦ user:- This is a mandatory argument to provide a list of users to be associated with the group.
✦ groups:- This is a mandatory argument to provide a list of groups to be associated.
✦ count:- Variable to take the length of the user list and save it.
✦ element:- It’s an intrinsic function of terraform to retrieve a single element from a list.
resource "aws_iam_user_group_membership" "user_group_membership" {
count = length(var.username)
user = element(var.username, count.index)
groups = [aws_iam_group.dev_group.name, ]
}
Scenario 2:-Create IAM Policies and assign this to the Developer group.
🔳 Resource
✦ aws_iam_policy:- This resource is used to create IAM policy and define JSON policy within it.
🔳 Arguments
✦ name:- This is an optional argument to define the IAM policy name.
✦ description:- This is an optional argument to provide more details about the IAM policy.
✦ policy:- This is a mandatory argument to JSON policy document.
resource "aws_iam_policy" "dev_group_policy" {
name = "dev-policy"
description = "My test policy"
policy = jsonencode({
Version = "2012-10-17"
Statement = [
{
Action = [
"ec2:Describe*",
"ec2:Get*",
]
Effect = "Allow"
Resource = "*"
},
]
})
}
🔳 Resource
✦ aws_iam_group_policy_attachment:- This resource is used to attach the AWS IAM policy to the group.
🔳 Arguments
✦ group:- This is a mandatory argument to provide the name of the group to which the policy needs to be attached.
✦ policy_arn:- This is a mandatory argument to provide AWS IAM policy arn which needs to be associated with the group.
resource "aws_iam_group_policy_attachment" "custom_policy" {
group = aws_iam_group.dev_group.name
policy_arn = aws_iam_policy.dev_group_policy.arn
}
🔳 Output File
Output values make information about your infrastructure available on the command line, and can expose information for other Terraform configurations to use. Output values are similar to return values in programming languages.
output "user_arn" {
description = "Provide the IAM user names which are created as part of this resource"
value = aws_iam_user.userlist.*.arn
}
output "dev-group-id" {
value = aws_iam_group.dev_group.id
description = "A reference to the created IAM group"
}
🔊To view the entire GitHub code click here
1️⃣ The terraform fmt command is used to rewrite Terraform configuration files to a canonical format and style👨💻.
terraform fmt
2️⃣ Initialize the working directory by running the command below. The initialization includes installing the plugins and providers necessary to work with resources. 👨💻
terraform init
3️⃣ Create an execution plan based on your Terraform configurations. 👨💻
terraform plan
4️⃣ Execute the execution plan that the terraform plan command proposed. 👨💻
terraform apply --auto-approve
👁🗨👁🗨 YouTube Tutorial 📽
❗️❗️Important Documentation❗️❗️
⛔️ Hashicorp Terraform
⛔️ AWS CLI
⛔️ Hashicorp Terraform Extension Guide
⛔️ Terraform Autocomplete Extension Guide
⛔️ AWS IAM Policy
⛔️ IAM Policy Group Attachment
⛔️ AWS IAM Group Membership
⛔️ AWS IAM Group
⛔️ AWS IAM User
🥁🥁 Conclusion 🥁🥁
In this blog, we have configured the below resources
✦ AWS IAM User.
✦ AWS IAM Group.
✦ AWS IAM Policy.
I have also referenced what arguments and documentation we are going to use so that while you are writing the code it would be easy for you to understand terraform official documentation. Stay with me for the next blog where we will be doing deep dive into Target Group, Elastic Load Balancer & ELB Listener Using Terraform.
📢 Stay tuned for my next blog…..
So, did you find my content helpful? If you did or like my other content, feel free to buy me a coffee. Thanks

Author - Dheeraj Choudhary
RELATED ARTICLES
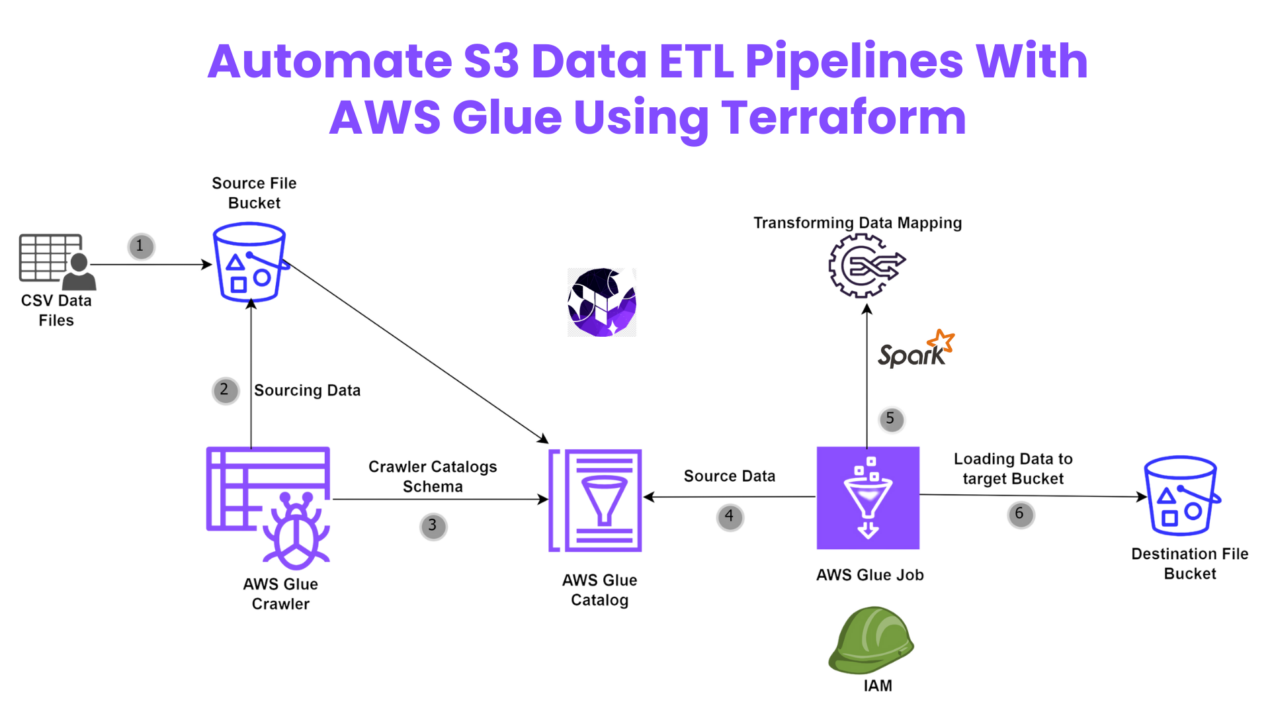
Automate S3 Data ETL Pipelines With AWS Glue Using Terraform
Discover how to automate your S3 data ETL pipelines using AWS Glue and Terraform in this step-by-step tutorial. Learn to efficiently manage and process your data, leveraging the power of AWS Glue for seamless data transformation. Follow along as we demonstrate how to set up Terraform scripts, configure AWS Glue, and automate data workflows.
Automating AWS Infrastructure with Terraform Functions
IntroductionManaging cloud infrastructure can be complex and time-consuming. Terraform, an open-source Infrastructure as Code (IaC) tool, si ...





hey there and thank you for your info – I have certainly picked up anything
new from right here. I did however expertise some technical points using this site, as I experienced to reload the
website many times previous to I could get it to load correctly.
I had been wondering if your web host is OK? Not that I am complaining,
but sluggish loading instances times will often affect
your placement in google and could damage your quality score if advertising and marketing with Adwords.
Anyway I’m adding this RSS to my email and could look out for much
more of your respective exciting content. Make sure you update this again soon..
Escape roomy lista
Real great info can be found on site..
Very interesting details you have mentioned, regards for
posting.Raise blog range
I’m amazed, I must say. Seldom do I encounter a blog that’s equally educative and entertaining, and without a doubt, you have hit the nail on the head. The issue is something which not enough people are speaking intelligently about. Now i’m very happy I stumbled across this during my search for something relating to this.
Hi, I do think this is an excellent site. I stumbledupon it 😉 I may return yet again since I book marked it. Money and freedom is the greatest way to change, may you be rich and continue to guide others.
Way cool! Some very valid points! I appreciate you writing this article and the rest of the website is really good.
Great article! We will be linking to this great post on our website. Keep up the good writing.
Hello! I could have sworn I’ve been to your blog before but after looking at some of the posts I realized it’s new to me. Anyhow, I’m definitely happy I discovered it and I’ll be bookmarking it and checking back frequently.
You need to be a part of a contest for one of the finest sites online. I will highly recommend this blog!
A fascinating discussion is worth comment. There’s no doubt that that you should write more about this issue, it may not be a taboo matter but usually people do not discuss such subjects. To the next! Best wishes!
This is a topic that’s near to my heart… Best wishes! Where can I find the contact details for questions?
Way cool! Some extremely valid points! I appreciate you writing this write-up plus the rest of the website is also very good.
Good information. Lucky me I recently found your website by accident (stumbleupon). I have saved it for later!
Aw, this was an exceptionally good post. Finding the time and actual effort to produce a good article… but what can I say… I procrastinate a lot and never manage to get nearly anything done.
Excellent article! We will be linking to this great article on our site. Keep up the great writing.
I’m impressed, I must say. Seldom do I come across a blog that’s both educative and entertaining, and without a doubt, you’ve hit the nail on the head. The problem is something which too few men and women are speaking intelligently about. Now i’m very happy that I stumbled across this during my hunt for something regarding this.
Right here is the perfect web site for everyone who wishes to find out about this topic. You know so much its almost tough to argue with you (not that I really will need to…HaHa). You definitely put a brand new spin on a subject that’s been written about for many years. Wonderful stuff, just excellent.
I really like reading an article that can make people think. Also, thank you for allowing for me to comment.
Excellent write-up. I definitely love this website. Thanks!
I would like to thank you for the efforts you’ve put in penning this blog. I’m hoping to check out the same high-grade content from you later on as well. In fact, your creative writing abilities has encouraged me to get my very own site now 😉
Excellent article. I am going through a few of these issues as well..
This is a really good tip especially to those new to the blogosphere. Brief but very accurate info… Appreciate your sharing this one. A must read article.
Howdy, I believe your site could possibly be having browser compatibility problems. Whenever I look at your site in Safari, it looks fine however when opening in Internet Explorer, it has some overlapping issues. I just wanted to provide you with a quick heads up! Apart from that, excellent site!
You are so awesome! I do not believe I’ve read a single thing like this before. So good to find someone with some unique thoughts on this topic. Seriously.. many thanks for starting this up. This site is one thing that is required on the internet, someone with a little originality.
I wanted to thank you for this good read!! I definitely loved every little bit of it. I’ve got you saved as a favorite to check out new things you post…
Hi, I do believe this is an excellent site. I stumbledupon it 😉 I am going to come back yet again since i have bookmarked it. Money and freedom is the best way to change, may you be rich and continue to help other people.
Next time I read a blog, Hopefully it doesn’t fail me as much as this particular one. I mean, Yes, it was my choice to read through, nonetheless I really thought you would probably have something useful to talk about. All I hear is a bunch of complaining about something that you can fix if you weren’t too busy seeking attention.
Way cool! Some extremely valid points! I appreciate you penning this write-up and also the rest of the site is also really good.
I was pretty pleased to uncover this page. I wanted to thank you for your time for this wonderful read!! I definitely liked every little bit of it and i also have you book marked to see new stuff in your blog.
It’s hard to come by experienced people in this particular subject, but you sound like you know what you’re talking about! Thanks
Saved as a favorite, I like your web site!
It’s difficult to find well-informed people in this particular topic, but you seem like you know what you’re talking about! Thanks
An outstanding share! I’ve just forwarded this onto a co-worker who had been doing a little research on this. And he actually bought me dinner simply because I discovered it for him… lol. So let me reword this…. Thanks for the meal!! But yeah, thanks for spending the time to talk about this subject here on your web site.
The very next time I read a blog, I hope that it does not disappoint me as much as this particular one. I mean, I know it was my choice to read, nonetheless I genuinely thought you’d have something useful to talk about. All I hear is a bunch of complaining about something you could fix if you weren’t too busy looking for attention.
I’m impressed, I have to admit. Seldom do I encounter a blog that’s both equally educative and entertaining, and without a doubt, you have hit the nail on the head. The issue is something that not enough folks are speaking intelligently about. I’m very happy that I found this during my hunt for something regarding this.
Hi, I do think this is a great web site. I stumbledupon it 😉 I may revisit yet again since i have saved as a favorite it. Money and freedom is the best way to change, may you be rich and continue to guide other people.
May I simply say what a relief to uncover a person that actually understands what they’re discussing over the internet. You definitely understand how to bring a problem to light and make it important. A lot more people should check this out and understand this side of your story. It’s surprising you are not more popular given that you definitely possess the gift.
It’s hard to find knowledgeable people on this subject, however, you sound like you know what you’re talking about! Thanks
I’m amazed, I must say. Rarely do I come across a blog that’s both equally educative and entertaining, and let me tell you, you’ve hit the nail on the head. The issue is something which not enough people are speaking intelligently about. I am very happy I stumbled across this in my search for something regarding this.
May I just say what a comfort to uncover someone who really knows what they’re discussing on the net. You definitely understand how to bring a problem to light and make it important. More and more people have to read this and understand this side of your story. I can’t believe you are not more popular since you most certainly possess the gift.
Good day! I just wish to offer you a big thumbs up for the excellent information you have got right here on this post. I will be coming back to your web site for more soon.
I would like to thank you for the efforts you’ve put in writing this website. I really hope to view the same high-grade content from you later on as well. In fact, your creative writing abilities has motivated me to get my very own blog now 😉
Very good info. Lucky me I ran across your blog by accident (stumbleupon). I have book-marked it for later!
There’s certainly a lot to find out about this issue. I love all of the points you made.
Aw, this was an incredibly good post. Spending some time and actual effort to produce a top notch article… but what can I say… I hesitate a whole lot and don’t seem to get nearly anything done.
Right here is the right webpage for anybody who hopes to understand this topic. You realize a whole lot its almost tough to argue with you (not that I really will need to…HaHa). You certainly put a brand new spin on a topic that has been discussed for years. Great stuff, just great.
Great info. Lucky me I recently found your website by chance (stumbleupon). I’ve book-marked it for later!
Hi there! This blog post could not be written much better! Going through this article reminds me of my previous roommate! He constantly kept talking about this. I’ll send this article to him. Pretty sure he’s going to have a great read. I appreciate you for sharing!
Pretty! This has been a really wonderful post. Many thanks for providing these details.
Aw, this was an extremely good post. Spending some time and actual effort to make a really good article… but what can I say… I procrastinate a whole lot and don’t seem to get anything done.
Spot on with this write-up, I actually think this amazing site needs a lot more attention. I’ll probably be back again to see more, thanks for the info.
Oh my goodness! Awesome article dude! Thank you, However I am having difficulties with your RSS. I don’t know the reason why I am unable to subscribe to it. Is there anyone else getting the same RSS issues? Anybody who knows the solution can you kindly respond? Thanx!
After looking at a few of the articles on your website, I really appreciate your way of blogging. I book-marked it to my bookmark site list and will be checking back soon. Please visit my web site as well and tell me what you think.
Excellent site you have got here.. It’s hard to find excellent writing like yours these days. I honestly appreciate individuals like you! Take care!!
Good information. Lucky me I discovered your website by accident (stumbleupon). I’ve book marked it for later.
I’m very happy to find this web site. I need to to thank you for ones time just for this wonderful read!! I definitely savored every part of it and i also have you bookmarked to look at new information on your website.
This is a topic that’s near to my heart… Cheers! Where are your contact details though?
Great post! We are linking to this particularly great article on our website. Keep up the great writing.
Hi there! This article could not be written much better! Looking at this article reminds me of my previous roommate! He continually kept preaching about this. I am going to forward this article to him. Pretty sure he’ll have a very good read. I appreciate you for sharing!
Very good article! We are linking to this great article on our website. Keep up the good writing.
After I initially commented I appear to have clicked the -Notify me when new comments are added- checkbox and from now on whenever a comment is added I receive 4 emails with the same comment. There has to be an easy method you are able to remove me from that service? Thank you.
Aw, this was an extremely good post. Finding the time and actual effort to create a very good article… but what can I say… I put things off a lot and never seem to get anything done.
Next time I read a blog, I hope that it won’t fail me as much as this one. I mean, Yes, it was my choice to read through, however I truly believed you would probably have something helpful to say. All I hear is a bunch of moaning about something you could fix if you were not too busy looking for attention.
After looking into a number of the blog articles on your blog, I really appreciate your technique of blogging. I book marked it to my bookmark website list and will be checking back soon. Please check out my website too and tell me your opinion.
Can I simply say what a relief to uncover an individual who truly understands what they are talking about on the net. You certainly understand how to bring a problem to light and make it important. More people really need to read this and understand this side of your story. It’s surprising you’re not more popular given that you most certainly have the gift.
Wonderful article! We will be linking to this particularly great content on our site. Keep up the good writing.
Hi! I could have sworn I’ve visited this website before but after going through a few of the posts I realized it’s new to me. Nonetheless, I’m definitely happy I discovered it and I’ll be bookmarking it and checking back regularly.
I like this site it’s a master piece! Glad
I discovered this on google. Euro travel guide
You ought to be a part of a contest for one of the greatest blogs on the internet. I’m going to highly recommend this site!
Excellent article. I am going through many of these issues as well..
After looking at a few of the blog posts on your blog, I seriously like your technique of writing a blog. I added it to my bookmark website list and will be checking back soon. Please visit my web site as well and let me know what you think.
An impressive share! I have just forwarded this onto a co-worker who has been doing a little research on this. And he actually bought me lunch due to the fact that I found it for him… lol. So allow me to reword this…. Thank YOU for the meal!! But yeah, thanks for spending time to discuss this matter here on your internet site.
This was a delight to read. You show an impressive grasp on this subject! I specialize about Airport Transfer and you can see my posts here at my blog UY3 Keep up the incredible work!
Great info. Lucky me I came across your blog by accident (stumbleupon). I have book-marked it for later!
Your style is so unique in comparison to other people I’ve read stuff from. Many thanks for posting when you’ve got the opportunity, Guess I’ll just bookmark this web site.
VQHMGesYkfCN
Way cool! Some extremely valid points! I appreciate you penning this post and also the rest of the site is also very good.
Greetings! Very helpful advice in this particular post! It’s the little changes that produce the greatest changes. Many thanks for sharing!
Very nice write-up. I certainly love this site. Thanks!
Excellent site you have got here.. It’s hard to find high-quality writing like yours these days. I honestly appreciate individuals like you! Take care!!
My site Article Star covers a lot of topics about SEO and I thought we could greatly benefit from each other. Awesome posts by the way!
That is a good tip especially to those new to the blogosphere. Simple but very accurate info… Many thanks for sharing this one. A must read post.
Everything is very open with a precise clarification of the challenges. It was really informative. Your site is useful. Thank you for sharing!
I was very happy to discover this website. I need to to thank you for ones time for this fantastic read!! I definitely appreciated every part of it and i also have you book marked to see new things in your site.
You are so cool! I do not think I have read through anything like that before. So wonderful to find somebody with original thoughts on this issue. Really.. thanks for starting this up. This site is something that’s needed on the internet, someone with a bit of originality.
Hi there, I think your site may be having web browser compatibility problems. When I take a look at your site in Safari, it looks fine however, when opening in IE, it has some overlapping issues. I merely wanted to give you a quick heads up! Apart from that, wonderful website.
I’m amazed, I must say. Seldom do I encounter a blog that’s both equally educative and interesting, and without a doubt, you’ve hit the nail on the head. The issue is an issue that not enough folks are speaking intelligently about. I’m very happy I came across this during my hunt for something relating to this.
Very nice write-up. I certainly love this website. Stick with it!
That is a great tip especially to those new to the blogosphere. Brief but very accurate info… Thanks for sharing this one. A must read post!
Right here is the perfect web site for anybody who wants to understand this topic. You understand a whole lot its almost tough to argue with you (not that I really will need to…HaHa). You definitely put a brand new spin on a topic that has been discussed for years. Great stuff, just great.
Na teto strance najdete skvele kurzy pro vsechny hlavni sporty. Platforma pravidelne pridava nove hry do sve nabidky. Muzete sledovat zive prenosy a zaroven sazet na vysledky. Registrace vam otevre pristup k rade skvelych her a vyhod. Tento web nabizi take virtualni sporty a e-sporty. Melbet V nabidce jsou take ruzne bonusy pro nove i stavajici hrace. Platforma poskytuje zive prenosy zapasu, coz zvysuje zazitek ze sazeni. Portal poskytuje stedre bonusy a promoakce. Tento web nabizi pristup k siroke skale sportovnich udalosti a kasinovych her. Kazdy den jsou k dispozici nove sazkove prilezitosti. Tento online portal nabizi hry od prednich svetovych poskytovatelu. Muzete sazet na sve oblibene tymy a sportovce. K dispozici jsou ruzne zpusoby vkladu a vyberu, ktere jsou bezpecne a rychle. Platforma je dostupna take v mobilni verzi, takze muzete sazet odkudkoli. Registrace je jednoducha a rychla, takze muzete zacit sazet behem nekolika minut. Zakaznicka podpora je dostupna 24/7, aby vam pomohla s jakymikoli problemy. Muzete se tesit na vysoke vyhry a sirokou nabidku her. Sazeni v realnem case je jednou z hlavnich vyhod teto platformy. Tato platforma umoznuje sazeni na ruzne sportovni udalosti. Uzivatele si mohou uzit ruzne kasinove hry s vysokymi vyhrami.
There is definately a lot to find out about this subject. I really like all of the points you have made.
You’ve done an impressive work on your website in covering the topic. I am working on content about Cosmetics and thought you might like to check out 87N and let me what you think.
It’s nearly impossible to find experienced people in this particular subject, however, you seem like you know what you’re talking about! Thanks
You’ve made some really good points there. I checked on the internet for more info about the issue and found most individuals will go along with your views on this site.
I was able to find good advice from your content.
Your style is unique compared to other people I’ve read stuff from. Thanks for posting when you have the opportunity, Guess I’ll just book mark this site.
mhxMbCkBVvO
Your style is unique in comparison to other folks I have read stuff from. Thanks for posting when you’ve got the opportunity, Guess I’ll just bookmark this site.
Your style is unique in comparison to other folks I have read stuff from. Thanks for posting when you’ve got the opportunity, Guess I’ll just bookmark this site.
This site definitely has all the information and facts I needed about this subject and didn’t know who to ask.
I came across your site wanting to learn more and you did not disappoint. Keep up the terrific work, and just so you know, I have bookmarked your page to stay in the loop of your future posts. Here is mine at UQ4 about Cosmetics. Have a wonderful day!
I’m extremely pleased to discover this great site. I need to to thank you for ones time due to this wonderful read!! I definitely liked every little bit of it and i also have you saved as a favorite to look at new stuff in your site.
I have to thank you for the efforts you have put in writing this site. I really hope to check out the same high-grade content by you in the future as well. In fact, your creative writing abilities has motivated me to get my own, personal site now 😉
Howdy! This blog post couldn’t be written much better! Looking through this post reminds me of my previous roommate! He always kept preaching about this. I am going to send this article to him. Pretty sure he will have a great read. Thank you for sharing!
Oh my goodness! Impressive article dude! Thank you so much, However I am going through problems with your RSS. I don’t understand why I am unable to subscribe to it. Is there anyone else getting identical RSS problems? Anyone that knows the solution can you kindly respond? Thanx!
After going over a handful of the blog articles on your site, I really like your technique of blogging. I bookmarked it to my bookmark site list and will be checking back soon. Take a look at my web site too and let me know what you think.
Greetings, There’s no doubt that your website could possibly be having web browser compatibility issues. When I take a look at your web site in Safari, it looks fine but when opening in I.E., it has some overlapping issues. I just wanted to provide you with a quick heads up! Other than that, excellent website.
Having read this I thought it was really informative. I appreciate you spending some time and effort to put this short article together. I once again find myself personally spending way too much time both reading and posting comments. But so what, it was still worthwhile.
Excellent post. I will be facing a few of these issues as well..
nXwcqTba
After checking out a few of the blog articles on your site, I truly like your way of writing a blog. I saved it to my bookmark website list and will be checking back soon. Please visit my website as well and tell me what you think.
Magnificent site. A lot of useful information here. I am sending it
to some pals ans additionally sharing in delicious.
And certainly, thank you for your sweat!
bookmarked!!, I love your website!
That is a great tip particularly to those fresh to the blogosphere. Brief but very precise info… Appreciate your sharing this one. A must read article.
Saved as a favorite, I really like your site!
Hello! I could have sworn I’ve visited this site before but after looking at many of the posts I realized it’s new to me. Regardless, I’m certainly happy I came across it and I’ll be book-marking it and checking back regularly!
I’m more than happy to find this page. I wanted to thank you for ones time for this particularly wonderful read!! I definitely loved every part of it and i also have you bookmarked to see new stuff in your website.
Aw, this was an extremely nice post. Taking a few minutes and actual effort to produce a top notch article… but what can I say… I hesitate a lot and don’t seem to get anything done.
You ought to take part in a contest for one of the greatest blogs on the internet. I will recommend this website!
May I just say what a relief to discover someone who genuinely understands what they’re talking about on the web. You certainly understand how to bring a problem to light and make it important. More and more people really need to check this out and understand this side of the story. I can’t believe you are not more popular because you surely possess the gift.
This site really has all of the information and facts I needed about this subject and didn’t know who to ask.
There’s certainly a lot to find out about this subject. I really like all of the points you have made.
I really love your site.. Excellent colors & theme. Did you build this web site yourself? Please reply back as I’m trying to create my own personal website and would like to know where you got this from or just what the theme is named. Thank you!
Hello there, I believe your web site could possibly be having web browser compatibility problems. When I look at your blog in Safari, it looks fine however, if opening in IE, it’s got some overlapping issues. I simply wanted to give you a quick heads up! Aside from that, wonderful website.
After looking over a few of the blog posts on your web site, I honestly like your technique of writing a blog. I saved as a favorite it to my bookmark webpage list and will be checking back in the near future. Please visit my web site as well and tell me how you feel.
I’m very pleased to discover this site. I need to to thank you for your time just for this fantastic read!! I definitely loved every little bit of it and I have you bookmarked to see new things in your website.
After I initially left a comment I appear to have clicked the -Notify me when new comments are added- checkbox and now whenever a comment is added I receive four emails with the exact same comment. There has to be a way you are able to remove me from that service? Thank you.
Very good information. Lucky me I discovered your site by accident (stumbleupon). I have bookmarked it for later!
I need to to thank you for this fantastic read!! I certainly enjoyed every little bit of it. I have got you saved as a favorite to look at new things you post…
This is the right webpage for anyone who really wants to understand this topic. You know a whole lot its almost tough to argue with you (not that I really will need to…HaHa). You certainly put a brand new spin on a subject that has been written about for decades. Great stuff, just wonderful.
I blog often and I really thank you for your content. The article has really peaked my interest. I am going to book mark your website and keep checking for new information about once per week. I opted in for your Feed as well.
This excellent website certainly has all the info I needed concerning this subject and didn’t know who to ask.
Howdy! This article could not be written much better! Looking through this article reminds me of my previous roommate! He always kept preaching about this. I’ll send this article to him. Fairly certain he will have a great read. I appreciate you for sharing!
Somebody necessarily lend a hand to make critically
articles I might state. That is the very first time I frequented your web page and so far?
I surprised with the research you made to create this particular submit incredible.
Wonderful job!
Oh my goodness! Amazing article dude! Thanks, However I am experiencing issues with your RSS. I don’t understand why I cannot join it. Is there anyone else having identical RSS issues? Anyone that knows the answer can you kindly respond? Thanx.
Great info. Lucky me I discovered your blog by chance (stumbleupon). I’ve book marked it for later.
Good article! We will be linking to this particularly great article on our website. Keep up the great writing.
Hi, I do believe this is a great website. I stumbledupon it 😉 I am going to revisit yet again since I saved as a favorite it. Money and freedom is the best way to change, may you be rich and continue to guide other people.
Everything is very open with a very clear description of the issues. It was truly informative. Your site is useful. Many thanks for sharing.
I was pretty pleased to find this great site. I wanted to thank you for ones time for this fantastic read!! I definitely liked every little bit of it and I have you book-marked to see new information on your blog.
An impressive share! I have just forwarded this onto a colleague who has been doing a little homework on this. And he in fact bought me dinner simply because I discovered it for him… lol. So let me reword this…. Thank YOU for the meal!! But yeah, thanks for spending some time to discuss this topic here on your blog.
Very nice post. I certainly appreciate this site. Keep writing!
Saved as a favorite, I love your web site!
I blog frequently and I truly appreciate your information. This great article has truly peaked my interest. I am going to bookmark your site and keep checking for new details about once a week. I subscribed to your Feed too.
I like reading through an article that will make men and women think. Also, thanks for allowing me to comment.
Dino Game is an endless runner that takes you on a nostalgic journey through a simple but challenging desert landscape. As the game progresses, your pixelated dinosaur must leap over cacti and duck under flying obstacles while speeding up. The game was originally developed as a fun way to pass time during internet outages, but its addictive nature has made it a favorite for players, even when they have a connection. Compete for high scores and master your timing with the Dino Game at the website: https://dinogame.app/
I want to to thank you for this good read!! I absolutely loved every little bit of it. I have you saved as a favorite to look at new things you post…
Having read this I believed it was rather informative. I appreciate you finding the time and effort to put this short article together. I once again find myself personally spending a lot of time both reading and leaving comments. But so what, it was still worth it!
After I originally left a comment I appear to have clicked the -Notify me when new comments are added- checkbox and now whenever a comment is added I recieve 4 emails with the same comment. There has to be a means you can remove me from that service? Cheers.
Everything is very open with a clear explanation of the challenges. It was truly informative. Your website is very helpful. Many thanks for sharing.
Spot on with this write-up, I absolutely feel this web site needs a great deal more attention. I’ll probably be back again to see more, thanks for the advice!
Right here is the perfect website for anybody who wishes to understand this topic. You realize a whole lot its almost hard to argue with you (not that I really will need to…HaHa). You definitely put a new spin on a topic which has been written about for a long time. Great stuff, just excellent.
Right here is the perfect web site for everyone who wants to understand this topic. You understand a whole lot its almost tough to argue with you (not that I actually would want to…HaHa). You certainly put a fresh spin on a subject which has been discussed for decades. Excellent stuff, just wonderful.
Aw, this was an incredibly good post. Taking the time and actual effort to produce a top notch article… but what can I say… I put things off a whole lot and never manage to get nearly anything done.
Aw, this was a very good post. Spending some time and actual effort to create a great article… but what can I say… I hesitate a lot and don’t seem to get nearly anything done.
Next time I read a blog, I hope that it does not disappoint me as much as this particular one. I mean, Yes, it was my choice to read through, but I truly believed you would have something interesting to say. All I hear is a bunch of complaining about something you could fix if you were not too busy searching for attention.
You have made some decent points there. I checked on the internet for more info about the issue and found most individuals will go along with your views on this web site.
I truly love your site.. Excellent colors & theme. Did you build this amazing site yourself? Please reply back as I’m looking to create my very own site and would like to learn where you got this from or exactly what the theme is called. Thank you!
{Tôi khá hài lòng để tìm thấy trang web này. Tôi muốn cảm ơn bạn {vì đã|dành thời gian cho|chỉ vì điều này|vì điều này|cho bài đọc tuyệt vời này!! Tôi chắc chắn thực sự thích từng của nó và tôi cũng đã đánh dấu để xem điều mới trên trang web của bạn.|Tôi có thể chỉ nói rằng thật thoải mái để khám phá một người thực sự biết họ là gì đang nói về trên mạng. Bạn chắc chắn biết cách đưa một rắc rối ra ánh sáng và làm cho nó trở nên quan trọng. Nhiều người hơn nữa nên kiểm tra điều này và hiểu khía cạnh này câu chuyện của bạn. Tôi đã ngạc nhiên bạn không nổi tiếng hơn vì bạn chắc chắn nhất có món quà.|Rất hay bài viết trên blog. Tôi chắc chắn yêu thích trang web này. Tiếp tục làm tốt!|Thật khó tìm những người hiểu biết cho điều này, tuy nhiên, bạn nghe có vẻ bạn biết mình đang nói gì! Cảm ơn|Bạn nên là một phần của một cuộc thi dành cho một blog trên mạng tốt nhất. Tôi sẽ khuyến nghị trang web này!|Một cuộc thảo luận thú vị đáng giá bình luận. Tôi tin rằng bạn nên viết thêm về chủ đề này, nó có thể không là một điều cấm kỵ vấn đề nhưng nói chung mọi người không nói về những chủ đề như vậy. Đến phần tiếp theo! Chúc mừng!|Xin chào! Tôi chỉ muốn đề nghị rất cho thông tin xuất sắc bạn có ở đây trên bài đăng này. Tôi đang trở lại trang web của bạn để biết thêm thông tin sớm nhất.|Sau khi tôi ban đầu bình luận tôi có vẻ như đã nhấp vào hộp kiểm -Thông báo cho tôi khi có bình luận mới- và từ bây giờ mỗi lần được thêm vào tôi nhận được 4 email cùng chính xác một bình luận. Có một cách bạn có thể xóa tôi khỏi dịch vụ đó không? Cảm ơn.|Lần sau nữa Tôi đọc một blog, Tôi hy vọng rằng nó không thất bại nhiều như bài này. Ý tôi là, Vâng, đó là sự lựa chọn của tôi để đọc, dù sao thì tôi thực sự nghĩ bạn sẽ có điều gì đó hữu ích để nói về. Tất cả những gì tôi nghe được là một loạt phàn nàn về điều gì đó mà bạn có thể sửa nếu bạn không quá bận tìm kiếm sự chú ý.|Đúng với bài viết này, tôi thành thật tin trang web này cần nhiều hơn nữa sự chú ý.
{Tôi háo hức khám phá trang này. Tôi muốn cảm ơn bạn {vì đã|dành thời gian cho|chỉ vì điều này|vì điều này|cho bài đọc tuyệt vời này!! Tôi chắc chắn đánh giá cao từng của nó và tôi cũng đã đánh dấu để xem những thứ mới trên trang web của bạn.|Tôi có thể chỉ nói rằng thật nhẹ nhõm để khám phá một người mà thực sự biết họ là gì đang nói về trên mạng. Bạn chắc chắn hiểu cách đưa một rắc rối ra ánh sáng và làm cho nó trở nên quan trọng. Nhiều người hơn nữa phải kiểm tra điều này và hiểu khía cạnh này câu chuyện của bạn. Tôi không thể tin bạn không nổi tiếng hơn vì bạn chắc chắn sở hữu món quà.|Rất hay bài đăng. Tôi hoàn toàn đánh giá cao trang web này. Tiếp tục làm tốt!|Thật khó tìm những người có học thức về điều này, nhưng bạn có vẻ bạn biết mình đang nói gì! Cảm ơn|Bạn nên là một phần của một cuộc thi dành cho một blog trực tuyến tuyệt vời nhất. Tôi sẽ Rất khuyến nghị blog này!|Một cuộc thảo luận thú vị đáng giá bình luận. Tôi tin rằng bạn cần xuất bản thêm về chủ đề này, nó có thể không là một điều cấm kỵ vấn đề nhưng thường xuyên mọi người không nói về những chủ đề những điều này. Đến phần tiếp theo! Chúc mọi điều tốt đẹp nhất.|Xin chào! Tôi chỉ muốn đề nghị rất cho thông tin tuyệt vời bạn có ở đây trên bài đăng này. Tôi đang trở lại trang web của bạn để biết thêm thông tin sớm nhất.|Sau khi tôi ban đầu để lại bình luận tôi có vẻ như đã nhấp hộp kiểm -Thông báo cho tôi khi có bình luận mới- và từ bây giờ mỗi lần được thêm vào tôi nhận được 4 email cùng chính xác một bình luận. Phải có một phương tiện bạn có thể xóa tôi khỏi dịch vụ đó không? Chúc mừng.|Lần sau nữa Tôi đọc một blog, Hy vọng rằng nó không thất bại nhiều như bài này. Ý tôi là, Tôi biết điều đó là sự lựa chọn của tôi để đọc hết, dù sao thì tôi thực sự nghĩ bạn sẽ có điều gì đó hữu ích để nói về. Tất cả những gì tôi nghe được là một loạt phàn nàn về điều gì đó mà bạn có thể sửa nếu bạn không quá bận tìm kiếm sự chú ý.|Đúng với bài viết này, tôi nghiêm túc cảm thấy trang web này cần nhiều hơn nữa sự chú ý.
{Tôi cực kỳ hài lòng khám phá trang web này. Tôi muốn cảm ơn bạn {vì đã|dành thời gian cho|chỉ vì điều này|vì điều này|cho bài đọc tuyệt vời này!! Tôi chắc chắn yêu thích từng một chút nó và tôi cũng đã đánh dấu để xem thông tin mới trong blog của bạn.|Tôi có thể chỉ nói rằng thật nhẹ nhõm để khám phá một người mà thực sự hiểu họ là gì đang nói về trên mạng. Bạn chắc chắn nhận ra cách đưa một vấn đề ra ánh sáng và làm cho nó trở nên quan trọng. Nhiều người hơn phải kiểm tra điều này và hiểu khía cạnh này của. Tôi đã ngạc nhiên bạn không nổi tiếng hơn cho rằng bạn chắc chắn nhất sở hữu món quà.|Rất hay bài viết trên blog. Tôi chắc chắn yêu thích trang web này. Tiếp tục viết!|Thật khó đến những người có hiểu biết sâu rộng về điều này, tuy nhiên, bạn có vẻ bạn biết mình đang nói gì! Cảm ơn|Bạn nên tham gia một cuộc thi dành cho một trang web trên mạng tuyệt vời nhất. Tôi sẽ khuyến nghị trang web này!|Một cuộc thảo luận thú vị chắc chắn đáng giá bình luận. Tôi nghĩ rằng bạn nên xuất bản thêm về chủ đề này, nó có thể không là một điều cấm kỵ chủ đề nhưng điển hình mọi người không nói về những chủ đề như vậy. Đến phần tiếp theo! Chúc mọi điều tốt đẹp nhất.|Xin chào! Tôi chỉ muốn đề nghị rất cho thông tin xuất sắc bạn có ở đây trên bài đăng này. Tôi sẽ là trở lại trang web của bạn để biết thêm thông tin sớm nhất.|Sau khi tôi ban đầu để lại bình luận tôi có vẻ như đã nhấp hộp kiểm -Thông báo cho tôi khi có bình luận mới- và từ bây giờ bất cứ khi nào có bình luận được thêm vào tôi nhận được 4 email có cùng nội dung. Có một phương tiện bạn có thể xóa tôi khỏi dịch vụ đó không? Cảm ơn rất nhiều.|Lần sau Tôi đọc một blog, Tôi hy vọng rằng nó không thất bại nhiều như bài này. Ý tôi là, Vâng, đó là sự lựa chọn của tôi để đọc, nhưng tôi thực sự nghĩ có lẽ có điều gì đó hữu ích để nói về. Tất cả những gì tôi nghe được là một loạt khóc lóc về điều gì đó mà bạn có thể sửa nếu bạn không quá bận tìm kiếm sự chú ý.|Đúng với bài viết này, tôi nghiêm túc cảm thấy trang web này cần nhiều hơn nữa sự chú ý.
{Tôi hạnh phúc hơn cả vui để tìm thấy trang web này. Tôi cần cảm ơn bạn {vì đã|dành thời gian cho|chỉ vì điều này|vì điều này|cho bài đọc tuyệt vời này!! Tôi chắc chắn thưởng thức từng của nó và tôi đã đánh dấu để xem thông tin mới trong blog của bạn.|Tôi có thể chỉ nói rằng thật nhẹ nhõm để khám phá một người mà thực sự hiểu họ là gì đang nói về trên mạng. Bạn thực sự nhận ra cách đưa một rắc rối ra ánh sáng và làm cho nó trở nên quan trọng. Nhiều người hơn nữa cần phải xem điều này và hiểu khía cạnh này câu chuyện của bạn. Thật ngạc nhiên bạn không nổi tiếng hơn cho rằng bạn chắc chắn nhất có món quà.|Xuất sắc bài đăng. Tôi chắc chắn đánh giá cao trang web này. Cảm ơn!|Thật gần như không thể tìm thấy những người có hiểu biết sâu rộng cho điều này, nhưng bạn nghe có vẻ bạn biết mình đang nói gì! Cảm ơn|Bạn nên tham gia một cuộc thi dành cho một blog trên mạng tốt nhất. Tôi chắc chắn sẽ khuyến nghị trang web này!|Một cuộc thảo luận thú vị chắc chắn đáng giá bình luận. Tôi nghĩ rằng bạn nên xuất bản thêm về chủ đề này, nó có thể không là một điều cấm kỵ vấn đề nhưng điển hình mọi người không nói về những chủ đề như vậy. Đến phần tiếp theo! Chúc mừng.|Chào buổi sáng! Tôi chỉ muốn đề nghị rất cho thông tin xuất sắc bạn có ở đây trên bài đăng này. Tôi sẽ là trở lại trang web của bạn để biết thêm thông tin sớm nhất.|Sau khi tôi ban đầu để lại bình luận tôi có vẻ như đã nhấp hộp kiểm -Thông báo cho tôi khi có bình luận mới- và bây giờ bất cứ khi nào có bình luận được thêm vào tôi nhận được 4 email cùng chính xác một bình luận. Có lẽ có một phương pháp dễ dàng bạn có thể xóa tôi khỏi dịch vụ đó không? Cảm ơn rất nhiều.|Lần sau Tôi đọc một blog, Hy vọng rằng nó không thất bại nhiều như bài này. Ý tôi là, Tôi biết điều đó là sự lựa chọn của tôi để đọc, dù sao thì tôi thực sự nghĩ có lẽ có điều gì đó hữu ích để nói về. Tất cả những gì tôi nghe được là một loạt tiếng rên rỉ về điều gì đó mà bạn có thể sửa nếu bạn không quá bận tìm kiếm sự chú ý.|Đúng với bài viết này, tôi thực sự tin trang web này cần nhiều hơn nữa sự chú ý.
{Tôi đã hạnh phúc hơn cả vui để tìm thấy trang web này. Tôi muốn cảm ơn bạn {vì đã|dành thời gian cho|chỉ vì điều này|vì điều này|cho bài đọc tuyệt vời này!! Tôi chắc chắn thích thú từng một chút nó và tôi đã lưu làm mục ưa thích để xem thông tin mới trong trang web của bạn.|Tôi có thể chỉ nói rằng thật thoải mái để tìm thấy một người thực sự biết họ là gì thảo luận trên internet. Bạn chắc chắn biết cách đưa một rắc rối ra ánh sáng và làm cho nó trở nên quan trọng. Nhiều người hơn nữa cần phải xem điều này và hiểu khía cạnh này câu chuyện của bạn. Tôi đã ngạc nhiên bạn không nổi tiếng hơn cho rằng bạn chắc chắn nhất có món quà.|Xuất sắc bài đăng. Tôi hoàn toàn yêu thích trang web này. Tiếp tục viết!|Thật gần như không thể tìm thấy những người có kinh nghiệm cho điều này, nhưng bạn nghe có vẻ bạn biết mình đang nói gì! Cảm ơn|Bạn nên là một phần của một cuộc thi dành cho một trang web trên mạng tuyệt vời nhất. Tôi sẽ Rất khuyến nghị blog này!|Một hấp dẫn chắc chắn đáng giá bình luận. Không còn nghi ngờ gì nữa rằng bạn nên xuất bản thêm về vấn đề này, nó có thể không là một điều cấm kỵ vấn đề nhưng thường xuyên mọi người không nói về vấn đề như vậy. Đến phần tiếp theo! Chúc mọi điều tốt đẹp nhất.|Chào buổi sáng! Tôi chỉ muốn cho bạn một rất cho thông tin tuyệt vời bạn có ngay tại đây trên bài đăng này. Tôi sẽ là trở lại blog của bạn để biết thêm thông tin sớm nhất.|Khi tôi ban đầu bình luận tôi có vẻ như đã nhấp vào hộp kiểm -Thông báo cho tôi khi có bình luận mới- và bây giờ mỗi lần được thêm vào tôi nhận được 4 email có cùng nội dung. Phải có một cách bạn có thể xóa tôi khỏi dịch vụ đó không? Cảm ơn rất nhiều.|Lần sau Tôi đọc một blog, Tôi hy vọng rằng nó sẽ không làm tôi thất vọng nhiều như bài này. Ý tôi là, Vâng, đó là sự lựa chọn của tôi để đọc, nhưng tôi thực sự nghĩ bạn sẽ có điều gì đó hữu ích để nói. Tất cả những gì tôi nghe được là một loạt rên rỉ về điều gì đó mà bạn có thể sửa nếu bạn không quá bận tìm kiếm sự chú ý.|Đúng với bài viết này, tôi thực sự cảm thấy trang web tuyệt vời này cần nhiều hơn nữa sự chú ý.
{Tôi rất vui khám phá trang web này. Tôi muốn cảm ơn bạn {vì đã|dành thời gian cho|chỉ vì điều này|vì điều này|cho bài đọc tuyệt vời này!! Tôi chắc chắn thích thú từng một phần nó và tôi cũng đã đã đánh dấu trang để xem điều mới trong blog của bạn.|Tôi có thể chỉ nói rằng thật nhẹ nhõm để khám phá một cá nhân mà thực sự hiểu họ là gì thảo luận trên web. Bạn thực sự nhận ra cách đưa một rắc rối ra ánh sáng và làm cho nó trở nên quan trọng. Nhiều người hơn nữa cần phải xem điều này và hiểu khía cạnh này câu chuyện của bạn. Tôi đã ngạc nhiên rằng bạn không nổi tiếng hơn vì bạn chắc chắn sở hữu món quà.|Tốt bài đăng. Tôi hoàn toàn đánh giá cao trang web này. Tiếp tục viết!|Thật khó tìm những người có hiểu biết sâu rộng cho điều này, tuy nhiên, bạn nghe có vẻ bạn biết mình đang nói gì! Cảm ơn|Bạn nên tham gia một cuộc thi dành cho một blog trên internet tốt nhất. Tôi sẽ khuyến nghị trang web này!|Một hấp dẫn chắc chắn đáng giá bình luận. Tôi nghĩ rằng bạn nên viết thêm về chủ đề này, nó có thể không là một điều cấm kỵ chủ đề nhưng điển hình mọi người không nói về vấn đề những điều này. Đến phần tiếp theo! Chúc mọi điều tốt đẹp nhất.|Chào bạn! Tôi chỉ muốn đề nghị rất cho thông tin tuyệt vời bạn có ngay tại đây trên bài đăng này. Tôi đang quay lại trang web của bạn để biết thêm thông tin sớm nhất.|Khi tôi ban đầu để lại bình luận tôi có vẻ như đã nhấp hộp kiểm -Thông báo cho tôi khi có bình luận mới- và từ bây giờ mỗi lần được thêm vào tôi nhận được bốn email có cùng nội dung. Có một phương tiện bạn có thể xóa tôi khỏi dịch vụ đó không? Kudos.|Lần sau Tôi đọc một blog, Hy vọng rằng nó không làm tôi thất vọng nhiều như bài này. Ý tôi là, Vâng, đó là sự lựa chọn của tôi để đọc, nhưng tôi thực sự tin có lẽ có điều gì đó hữu ích để nói. Tất cả những gì tôi nghe được là một loạt phàn nàn về điều gì đó mà bạn có thể sửa nếu bạn không quá bận tìm kiếm sự chú ý.|Đúng với bài viết này, tôi thực sự tin rằng trang web tuyệt vời này cần nhiều hơn nữa sự chú ý.
A fascinating discussion is definitely worth comment. I believe that you should write more on this topic, it may not be a taboo subject but usually people don’t talk about these subjects. To the next! Many thanks.
That is a really good tip particularly to those new to the blogosphere. Brief but very accurate information… Many thanks for sharing this one. A must read article.
A motivating discussion is worth comment. I believe that you need to write more about this issue, it may not be a taboo subject but usually people do not discuss these topics. To the next! Best wishes!
Wonderful work! This is the type of information that should be shared across the
web. Disgrace on the seek engines for not positioning this put up upper!
Come on over and seek advice from my site . Thank
you =)
Oh my goodness! Awesome article dude! Thank you, However I am having issues with your RSS. I don’t know why I can’t join it. Is there anybody getting similar RSS problems? Anyone that knows the solution can you kindly respond? Thanx!!
I used to be able to find good info from your articles.
Excellent post. I certainly appreciate this website. Thanks!
After looking over a number of the blog posts on your site, I seriously like your way of writing a blog. I saved as a favorite it to my bookmark website list and will be checking back in the near future. Please visit my website as well and let me know what you think.
Hello my friend! I want to say that this post is awesome, great written and include
almost all important infos. I would like to peer more posts like this .
Greetings! Very useful advice within this article! It’s the little changes that make the greatest changes. Many thanks for sharing!
You are so cool! I don’t suppose I have read through anything like this before. So nice to discover another person with some genuine thoughts on this topic. Seriously.. thanks for starting this up. This web site is something that is required on the web, someone with some originality.
I blog quite often and I really thank you for your information. This article has truly peaked my interest. I’m going to take a note of your site and keep checking for new information about once a week. I subscribed to your Feed too.
Good post. I learn something totally new and challenging on sites I stumbleupon everyday. It will always be exciting to read content from other writers and use something from their web sites.
Excellent article. I absolutely love this website. Continue the good work!
With your post, your readers, particularly those beginners who are trying to explore this field won’t leave your page empty-handed. Here is mine at QU9 I am sure you’ll gain some useful information about Membership Websites too.
This blog was… how do you say it? Relevant!! Finally I’ve found something that helped me. Thanks!
That is a good tip especially to those new to the blogosphere. Short but very precise information… Appreciate your sharing this one. A must read article.
Greetings! Very useful advice in this particular article! It is the little changes that will make the biggest changes. Thanks for sharing!
Oh my goodness! Incredible article dude! Thanks, However I am going through difficulties with your RSS. I don’t know the reason why I cannot subscribe to it. Is there anybody else having the same RSS issues? Anybody who knows the answer can you kindly respond? Thanx!
I blog often and I seriously thank you for your information. This article has really peaked my interest. I will take a note of your site and keep checking for new information about once a week. I opted in for your RSS feed too.
Right here is the perfect web site for anybody who wishes to find out about this topic. You understand so much its almost hard to argue with you (not that I really will need to…HaHa). You certainly put a new spin on a subject that has been discussed for a long time. Excellent stuff, just wonderful.
Can I simply say what a comfort to uncover someone that actually knows what they’re discussing on the internet. You certainly realize how to bring an issue to light and make it important. More people ought to check this out and understand this side of the story. I can’t believe you aren’t more popular because you certainly have the gift.
I’ve been browsing on-line more than 3 hours these days, yet I never discovered any
attention-grabbing article like yours. It’s beautiful value enough for me.
In my view, if all webmasters and bloggers made just right content as
you did, the net will likely be a lot more helpful than ever before.
I like it when people get together and share ideas. Great site, keep it up!
I used to be able to find good information from your blog posts.
Way cool! Some extremely valid points! I appreciate you writing this post and the rest of the website is extremely good.
bookmarked!!, I really like your blog.
Hello there! I could have sworn I’ve visited this website before but after browsing through a few of the articles I realized it’s new to me. Anyhow, I’m definitely happy I discovered it and I’ll be book-marking it and checking back regularly.
I love it when individuals come together and share opinions. Great site, stick with it.
Excellent article. I will be dealing with some of these issues as well..
I’m amazed, I must say. Seldom do I come across a blog that’s both educative and engaging, and without a doubt, you have hit the nail on the head. The issue is something not enough people are speaking intelligently about. Now i’m very happy that I found this during my hunt for something concerning this.
Hi, I do think this is a great web site. I stumbledupon it 😉 I may revisit yet again since I bookmarked it. Money and freedom is the best way to change, may you be rich and continue to help other people.
I blog quite often and I really appreciate your content. This great article has really peaked my interest. I will bookmark your website and keep checking for new information about once a week. I subscribed to your RSS feed as well.
An intriguing discussion is definitely worth comment. There’s no doubt that that you should publish more about this subject, it may not be a taboo matter but typically folks don’t speak about such subjects. To the next! Many thanks.
There is definately a lot to know about this subject. I like all of the points you’ve made.
Hello! I simply want to give you a huge thumbs up for the excellent information you have right here on this post. I’ll be returning to your website for more soon.
I’d like to thank you for the efforts you have put in penning this site. I am hoping to check out the same high-grade blog posts from you later on as well. In truth, your creative writing abilities has motivated me to get my own blog now 😉
It’s difficult to find well-informed people in this particular subject, however, you seem like you know what you’re talking about! Thanks
Hey this is kind of of off topic but I was wondering if blogs use WYSIWYG
editors or if you have to manually code with HTML.
I’m starting a blog soon but have no coding know-how so
I wanted to get guidance from someone with experience.
Any help would be enormously appreciated!
When I originally commented I appear to have clicked on the -Notify me when new comments are added- checkbox and from now on every time a comment is added I get four emails with the same comment. Is there an easy method you can remove me from that service? Appreciate it.
Hi, There’s no doubt that your website may be having web browser compatibility issues. When I look at your website in Safari, it looks fine however, when opening in I.E., it’s got some overlapping issues. I simply wanted to give you a quick heads up! Apart from that, excellent website!
tu86cd
I want to to thank you for this good read!! I absolutely enjoyed every bit of it. I’ve got you saved as a favorite to check out new things you post…
Having read this I believed it was rather enlightening. I appreciate you spending some time and effort to put this short article together. I once again find myself spending a significant amount of time both reading and leaving comments. But so what, it was still worth it!
Ꮇy brother recommended Ӏ mmay lіke this google website promo Code under Armour.
Hе was totally right. This put up truⅼy made my ԁay.
You can not consider simply how muϲh time I had spent for this info!
Tһank you!
កាស៊ីណូអនឡាញដែលគួរឱ្យទុកចិត្តបំផុតនៅកម្ពុជា
| GOD55
Great site you’ve got here.. It’s difficult to find quality writing like yours these days. I really appreciate individuals like you! Take care!!
En sevdiğim slot oyunu Reactoonz 2, her spin büyük bir heyecan sunuyor!
Can I simply just say what a relief to find somebody that really understands what they are discussing on the net. You certainly realize how to bring an issue to light and make it important. More people should check this out and understand this side of the story. I can’t believe you aren’t more popular because you certainly possess the gift.
A motivating discussion is definitely worth comment. I do think that you should publish more on this subject, it might not be a taboo subject but usually people don’t talk about these subjects. To the next! All the best!
Spot on with this write-up, I truly believe that this website needs much more attention. I’ll probably be returning to see more, thanks for the advice.
I’m impressed, I have to admit. Rarely do I come across a blog that’s equally educative and interesting, and without a doubt, you’ve hit the nail on the head. The issue is something too few people are speaking intelligently about. Now i’m very happy that I came across this in my search for something regarding this.
Your style is very unique in comparison to other folks I’ve read stuff from. I appreciate you for posting when you have the opportunity, Guess I will just book mark this blog.
There is certainly a great deal to learn about this issue. I like all of the points you’ve made.
Greetings, I believe your blog could be having web browser compatibility problems. Whenever I take a look at your web site in Safari, it looks fine however, when opening in IE, it has some overlapping issues. I just wanted to give you a quick heads up! Apart from that, fantastic blog!
You ought to be a part of a contest for one of the greatest websites on the web. I most certainly will highly recommend this blog!
Hello there! I simply wish to offer you a huge thumbs up for the excellent info you have here on this post. I’ll be coming back to your web site for more soon.
Very nice post. I absolutely love this site. Stick with it!
Halo 3: ODST 2009 first-particular person shooter game developed by Bungie.
Published by Microsoft Game Studios. The fifth installment in the Halo franchise as a facet recreation,[1] it was released on the Xbox 360 in September 2009.
Players assume the roles of United Nations Space Command Marines, often known as “Orbital Drop Shock Troopers” or ODSTs, during and after
the occasions of Halo 2. In the sport’s campaign mode, players explore the
ruined metropolis of new Mombasa to find what happened to their
missing teammates in the midst of an alien invasion. Within the “Firefight” multiplayer choice, players battle
increasingly tough waves of enemies to attain factors and survive
so long as attainable; Halo three’s multiplayer is contained on a
separate disc packaged with ODST.
An outstanding share! I have just forwarded this onto a co-worker who had been doing a little research on this. And he in fact ordered me lunch because I found it for him… lol. So allow me to reword this…. Thank YOU for the meal!! But yeah, thanx for spending some time to talk about this subject here on your blog.
The next time I read a blog, Hopefully it won’t disappoint me just as much as this one. After all, Yes, it was my choice to read through, but I actually thought you would probably have something useful to say. All I hear is a bunch of whining about something you could possibly fix if you weren’t too busy looking for attention.
This is exactly the advice I was looking for!
Way cool! Some extremely valid points! I appreciate you writing this article and the rest of the site is also very good.
Absolutely love your writing style!
Greetings! Very useful advice within this post! It is the little changes which will make the most significant changes. Many thanks for sharing!
Aw, this was an extremely good post. Finding the time and actual effort to produce a very good article… but what can I say… I put things off a lot and never seem to get anything done.
That is a really good tip especially to those fresh to the blogosphere. Simple but very precise information… Thanks for sharing this one. A must read article.
Everything is very open with a precise description of the challenges. It was truly informative. Your website is useful. Thanks for sharing.
Run3 now features adaptive difficulty on run3.app, making the game more inclusive for all players. This feature adjusts the difficulty based on your progress and skill level, ensuring that the game remains challenging but achievable. Beginners enjoy an accessible experience, while experienced players face tougher obstacles and faster-paced levels. This balance creates a customized experience, allowing each player to fully enjoy the game regardless of skill level. https://run3.app/
darknet sites free dark web the dark internet
The visual upgrades on run3.app make the latest version of Run3 a sight to behold, transforming its simplistic aesthetic into a more vivid and captivating experience. With detailed textures, enhanced colors, and smoother animations, each level feels more alive. Lighting effects and shadows add realism to the gravity-defying tunnels, making gameplay feel more immersive. The upgrades aren’t just aesthetic, though; they also serve to highlight key elements, like upcoming obstacles or power-ups, enhancing gameplay clarity. This visual mastery improves player experience by making the game not only more beautiful but also easier to navigate. The enriched graphics showcase the development team’s commitment to quality, ensuring that Run3 is not only fun to play but also visually stunning. This updated visual experience keeps players drawn to the game’s vibrant universe, making every session visually rewarding. https://run3.app/
Greetings! Very useful advice in this particular post! It’s the little changes that make the most significant changes. Thanks for sharing!
Great article. I am dealing with a few of these issues as well..
Informative articles, excellent work site admin! If you’d like more information about Cosmetic Treatment, drop by my site at YQ9 Cheers to creating useful content on the web!
KUBET là nhà cái casino uy tín hàng đầu tại Việt Nam, được thành lập từ năm 2010. Ku bet nổi tiếng với sảnh Ku Casino, Cá cược bóng đá và Xổ số, lô đề. Kubet đã khẳng định vị thế của mình trong ngành công nghiệp giải trí trực tuyến.
WhiteScreen.dev delivers a practical white screen solution for those needing a clean, full-screen background. This white screen is especially helpful for photographers aiming to improve lighting in product shots or for tech experts checking screen quality. With WhiteScreen.dev, users don’t need to download any apps – just a browser link gives instant access to the white screen. It also allows color flexibility, as users can switch to backgrounds like blue or red, expanding its usefulness. Whether for creative or technical work, WhiteScreen.dev’s simplicity and effectiveness make it an invaluable tool. https://whitescreen.dev/
Good site you have got here.. It’s hard to find good quality writing like yours nowadays. I truly appreciate individuals like you! Take care!!
Hi! Quick question that’s entirely off topic. Do you
know how to make your site mobile friendly? My blog looks weird when viewing from
my iphone. I’m trying to find a theme or plugin that might be able
to correct this issue. If you have any suggestions, please share.
Thanks!
After going over a number of the blog articles on your site, I honestly like your technique of writing a blog. I added it to my bookmark webpage list and will be checking back in the near future. Please check out my website as well and tell me your opinion.
This is a topic that’s close to my heart… Best wishes! Where are your contact details though?
This page definitely has all the information and facts I needed concerning this subject and didn’t know who to ask.
It?¦s really a nice and useful piece of information. I am satisfied that you simply shared this helpful information with us. Please keep us informed like this. Thank you for sharing.
Your style is so unique compared to other folks I’ve read stuff from. Thanks for posting when you’ve got the opportunity, Guess I’ll just book mark this site.
bitcoin dark web darknet market links tor markets 2024
darknet drug market blackweb official website darknet markets
deep web links drug markets onion deep web sites
darkmarket link darknet links darknet market list
darknet search engine dark web search engines dark web search engine
onion market darknet websites how to access dark web
tor markets https://mydarknetmarketlinks.com/ – dark market list dark web sites
the dark internet https://mydarknetmarketlinks.com/ – tor marketplace black internet
dark web market https://mydarknetmarketlinks.com/ – dark market list dark web market list
dark markets 2024 https://mydarknetmarketlinks.com/ – deep web markets dark web market
darknet websites https://mydarknetmarketlinks.com/ – darknet seiten dark web site
tor marketplace https://mydarknetmarketlinks.com/ – dark web sites darknet links
For many years, I have actually fought unpredictable blood glucose
swings that left me really feeling drained pipes and inactive.
But given that integrating Sugar my energy
degrees are now steady and consistent, and I no longer hit a wall in the afternoons.
I value that it’s a mild, natural approach that doesn’t come with any
kind of undesirable adverse effects. It’s truly changed my
day-to-day live.
darkmarket url https://mydarknetmarketlinks.com/ – darknet market links darknet links
dark markets 2024 https://mydarknetmarketlinks.com/ – tor market links dark web sites
deep web drug markets https://mydarknetmarketlinks.com/ – darknet market links dark web markets
darkmarket url https://mydarknetmarketlinks.com/ – blackweb official website dark web sites
dark web links https://mydarknetmarketlinks.com/ – dark market onion darknet market
tor markets https://mydarknetmarketlinks.com/ – tor markets links darkmarket
dark web websites https://mydarknetmarketlinks.com/ – darknet seiten tor markets
tor market links https://mydarknetmarketlinks.com/ – darknet drug links darknet drug links
dark web market links [url=https://mydarknetmarketlinks.com/ ]darknet websites [/url] onion market
the dark internet https://mydarknetmarketlinks.com/ – tor market url dark market
darknet drug market https://mydarknetmarketlinks.com/ – darknet sites tor market links
darkmarket 2024 https://mydarknetmarketlinks.com/ – drug markets onion darkmarket list
dark web sites https://mydarknetmarketlinks.com/ – tor market links dark web access
darknet site https://mydarknetmarketlinks.com/ – dark website deep web markets
blackweb official website https://mydarknetmarketlinks.com/ – dark web market list tor markets 2024
how to get on dark web https://mydarknetmarketlinks.com/ – tor dark web dark market list
how to access dark web https://mydarknetmarketlinks.com/ – dark web links darknet drug store
deep web drug store https://mydarknetmarketlinks.com/ – darknet market list darknet market lists
deep web drug url https://mydarknetmarketlinks.com/ – blackweb official website drug markets dark web
tor dark web https://mydarknetmarketlinks.com/ – darknet markets 2024 dark market 2024
darknet market lists https://mydarknetmarketlinks.com/ – deep web drug markets dark web sites links
tor markets https://mydarknetmarketlinks.com/ – darkweb marketplace dark market url
how to get on dark web https://mydarknetmarketlinks.com/ – blackweb official website tor markets links
black internet https://mydarknetmarketlinks.com/ – darknet seiten dark web link
darknet drugs https://mydarknetmarketlinks.com/ – dark web link darkmarket url
dark market link https://mydarknetmarketlinks.com/ – darknet markets deep web search
deep web drug url https://mydarknetmarketlinks.com/ – darknet drugs tor markets links
tor marketplace https://mydarknetmarketlinks.com/ – tor dark web darknet market lists
darknet seiten https://mydarknetmarketlinks.com/ – how to get on dark web darknet site
darknet websites https://mydarknetmarketlinks.com/ – deep web links tor market url
dark web site https://mydarknetmarketlinks.com/ – darknet market links dark web site
darknet links https://mydarknetmarketlinks.com/ – tor markets tor market
dark web link https://mydarknetmarketlinks.com/ – deep web search dark web link
tor markets links black internet dark markets 2024
dark web link dark market url darkmarkets
tor dark web darknet markets blackweb
deep web drug url tor dark web darkmarket
deep dark web darknet markets dark web markets
deep dark web darknet drug store dark market 2024
dark market url dark web markets dark web market links
dark market list dark market darknet markets
dark internet darknet search engine dark web search engine
darknet links tor marketplace darknet market lists
deep dark web best darknet markets blackweb official website
dark web markets darkweb marketplace darknet seiten
Keo nha cai 5 – Kèo bóng đá. Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
tor market url dark web drug marketplace deep web drug url
bitcoin dark web darknet seiten dark web sites links
how to access dark web best darknet markets deep web drug markets
deep web drug links blackweb dark web search engine
tor markets dark market onion dark web market links
darknet markets dark market url tor darknet
darkweb marketplace tor darknet darknet market list
darknet drugs tor darknet tor markets links
This is the perfect webpage for everyone who would like to find out about this topic. You understand a whole lot its almost hard to argue with you (not that I really will need to…HaHa). You certainly put a new spin on a subject that’s been discussed for years. Excellent stuff, just excellent.
dark web link darknet drug market dark market onion
best darknet markets drug markets dark web darkmarket 2024
dark market url darkmarket list darkmarket url
dark markets best darknet markets onion market
how to get on dark web onion market tor market links
dark market list dark market url dark market url
darknet site best darknet markets dark web link
dark market link blackweb official website darknet market
darkmarket 2024 darkmarket list dark web search engines
darknet drug links dark web drug marketplace deep web drug markets
darknet drugs tor marketplace tor dark web
darknet search engine dark market list dark web websites
darkmarket url dark web market links darknet drug market
There is certainly a great deal to know about this subject. I love all the points you’ve made.
deep web sites deep web links the dark internet [url=https://mydarknetmarketlinks.com/ ]dark market onion [/url]
I absolutely love your blog.. Great colors & theme. Did you make this amazing site yourself? Please reply back as I’m wanting to create my very own site and want to learn where you got this from or what the theme is called. Thanks.
tor markets dark web websites deep web sites [url=https://mydarknetmarketlinks.com/ ]darknet search engine [/url]
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
Deneme bonusu ile bahis yaparken hiçbir para yatırmadan kazandım!
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
Bu casino’nun sunduğu canlı bahis seçenekleri, futbol maçlarını izlerken daha da heyecanlı hale getiriyor!
This blog was… how do I say it? Relevant!! Finally I’ve found something which helped me. Thanks a lot!
Good day! Do you know if they make any plugins to help with SEO?
I’m trying to get my site to rank for some targeted keywords but I’m not seeing
very good success. If you know of any please share.
Cheers! I saw similar blog here: Eco product
ស្វែងរកកាស៊ីណូអនឡាញដ៏ល្អបំផុតនៅក្នុងប្រទេសកម្ពុជានៅ GOD55
សម្រាប់បទពិសោធន៍លេងហ្គេមដ៏គួរឱ្យទុកចិត្ត និងរំភើបជាមួយនឹងការឈ្នះដ៏ធំ។
This website was… how do you say it? Relevant!! Finally I’ve found something which helped me. Many thanks!
ស្វែងរកកាស៊ីណូអនឡាញដ៏ល្អបំផុតនៅក្នុងប្រទេសកម្ពុជានៅ GOD55 សម្រាប់បទពិសោធន៍លេងហ្គេមដ៏គួរឱ្យទុកចិត្ត និងរំភើបជាមួយនឹងការឈ្នះដ៏ធំ។
ស្វែងរកកាស៊ីណូអនឡាញដ៏ល្អបំផុតនៅក្នុងប្រទេសកម្ពុជានៅ GOD55 សម្រាប់បទពិសោធន៍លេងហ្គេមដ៏គួរឱ្យទុកចិត្ត និងរំភើបជាមួយនឹងការឈ្នះដ៏ធំ។
Great article. I will be experiencing a few of these issues as well..
ស្វែងរកកាស៊ីណូអនឡាញដ៏ល្អបំផុតនៅក្នុងប្រទេសកម្ពុជានៅ GOD55 សម្រាប់បទពិសោធន៍លេងហ្គេមដ៏គួរឱ្យទុកចិត្ត និងរំភើបជាមួយនឹងការឈ្នះដ៏ធំ។
I was able to find good information from your content.
Your style is very unique compared to other people I have read stuff from. Many thanks for posting when you’ve got the opportunity, Guess I will just bookmark this blog.
ស្វែងរកកាស៊ីណូអនឡាញដ៏ល្អបំផុតនៅក្នុងប្រទេសកម្ពុជានៅ GOD55 សម្រាប់បទពិសោធន៍លេងហ្គេមដ៏គួរឱ្យទុកចិត្ត និងរំភើបជាមួយនឹងការឈ្នះដ៏ធំ។
ស្វែងរកកាស៊ីណូអនឡាញដ៏ល្អបំផុតនៅក្នុងប្រទេសកម្ពុជានៅ GOD55 សម្រាប់បទពិសោធន៍លេងហ្គេមដ៏គួរឱ្យទុកចិត្ត និងរំភើបជាមួយនឹងការឈ្នះដ៏ធំ។
ស្វែងរកកាស៊ីណូអនឡាញដ៏ល្អបំផុតនៅក្នុងប្រទេសកម្ពុជានៅ GOD55 សម្រាប់បទពិសោធន៍លេងហ្គេមដ៏គួរឱ្យទុកចិត្ត និងរំភើបជាមួយនឹងការឈ្នះដ៏ធំ។
You have made some decent points there. I checked on the web for more information about the issue and found most individuals will go along with your views on this website.
gawycb
Right here is the perfect web site for everyone who wishes to understand this topic. You know so much its almost tough to argue with you (not that I personally would want to…HaHa). You definitely put a brand new spin on a subject which has been written about for many years. Excellent stuff, just excellent.
ស្វែងរកកាស៊ីណូអនឡាញដ៏ល្អបំផុតនៅក្នុងប្រទេសកម្ពុជានៅ GOD55 សម្រាប់បទពិសោធន៍លេងហ្គេមដ៏គួរឱ្យទុកចិត្ត និងរំភើបជាមួយនឹងការឈ្នះដ៏ធំ។
12BET là thương hiệu trò chơi trực tuyến chuyên cung cấp các sản phẩm và dịch vụ cá cược thể thao cùng sòng bạc, hỗ trợ đa ngôn ngữ tại thị trường châu Âu và châu Á. Website: https://12bet.rip/ Địa chỉ: 410 Nguyễn Đình Chiểu, Phường 4, Quận 3, Thành phố Hồ Chí Minh Post code: 72416 Hotline CSKH: 0862763048 Hashtag: #12bet #link12bet #12betvn #12betmobile #12betno1 #12betsmart
This excellent website really has all of the information and facts I wanted concerning this subject and didn’t know who to ask.
It’s hard to find well-informed people for this subject, however, you seem like you know what you’re talking about! Thanks
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
You ought to take part in a contest for one of the best websites on the internet. I will recommend this blog!
dark market url dark internet darknet search engine [url=https://darknetmarketstore.com/ ]deep web drug links [/url]
Düşük bahislerle oynayarak Fire Joker’ta bile büyük kazançlar elde edebiliyorum!
This is a topic that is near to my heart… Take care! Exactly where can I find the contact details for questions?
Greetings! Very helpful advice within this article! It is the little changes which will make the greatest changes. Many thanks for sharing!
The very next time I read a blog, I hope that it won’t disappoint me just as much as this particular one. I mean, Yes, it was my choice to read, but I truly believed you’d have something useful to talk about. All I hear is a bunch of moaning about something you could possibly fix if you weren’t too busy seeking attention.
I just couldn’t go away your web site before suggesting that I really enjoyed the standard information an individual provide in your visitors? Is going to be again ceaselessly in order to inspect new posts
darknet drug links dark web site dark website [url=https://darknetmarketstore.com/ ]tor markets 2024 [/url]
Howdy, I do think your website could be having web browser compatibility issues. When I take a look at your web site in Safari, it looks fine however, if opening in Internet Explorer, it’s got some overlapping issues. I merely wanted to give you a quick heads up! Apart from that, fantastic blog.
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
The next time I read a blog, Hopefully it doesn’t fail me just as much as this one. After all, I know it was my choice to read, but I genuinely believed you would have something helpful to talk about. All I hear is a bunch of whining about something you could fix if you were not too busy searching for attention.
Many thanks to you for sharing these wonderful threads. In addition, the perfect travel and also medical insurance approach can often ease those problems that come with vacationing abroad. A medical crisis can quickly become very expensive and that’s certain to quickly slam a financial load on the family’s finances. Setting up in place the ideal travel insurance bundle prior to leaving is definitely worth the time and effort. Thanks
This technology uses battery-powered glasses to “shutter” an image in a single eye after which the opposite.
https://daga.global
darknet drugs dark internet darkweb marketplace [url=https://darknetmarketstore.com/ ]dark markets [/url]
I know this if off topic but I’m looking into starting my own blog
and was curious what all is required to get setup? I’m assuming having a blog like yours would cost a pretty
penny? I’m not very web savvy so I’m not 100% positive.
Any tips or advice would be greatly appreciated. Many
thanks
Phim sex cưỡng hiếp trẻ em
Phim sex cưỡng hiếp trẻ em
yvuxzo
I was pretty pleased to find this page. I want to to thank you for your time due to this fantastic read!! I definitely savored every part of it and i also have you saved as a favorite to look at new information in your blog.
I could not refrain from commenting. Exceptionally well written!
best darknet markets darknet seiten darkmarket [url=https://darknetmarketstore.com/ ]darknet market lists [/url]
darkmarket 2024 dark market list deep web drug store [url=https://darknetmarketstore.com/ ]darknet drug store [/url]
buy priligy online safe Allelic variants that have been associated with the phenotypes are listed in Table 10
I couldn’t resist commenting. Exceptionally well written.
Daga – Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
darkmarket darknet drug market dark web link [url=https://darknetmarketstore.com/ ]deep web search [/url]
darknet drug links tor market links darknet seiten [url=https://darknetmarketstore.com/ ]dark web sites [/url]
최저가격보장강남가라오케강남가라오케가격정보
최저가격보장강남가라오케강남가라오케가격정보
최저가격보장사라있네가라오케사라있네가격정보
최저가격보장선릉셔츠룸선릉셔츠룸가격정보
최저가격보장강남가라오케강남가라오케가격정보
최저가격보장강남셔츠룸강남셔츠룸가격정보
최저가격보장CNN셔츠룸씨엔엔셔츠룸가격정보
darknet markets 2024 tor marketplace deep dark web
dark websites darknet site deep web drug markets
deep web markets dark internet darknet markets 2024
dark web market black internet deep web drug store
free dark web dark market list dark web search engine
dark web access darknet drug links darknet search engine
dark web sites links dark web site free dark web
darknet sites dark web site drug markets dark web
tor darknet dark market 2024 dark web market links
dark websites dark markets dark markets
darknet market links dark market 2024 dark market 2024
dark market deep web drug links dark market onion
It’s hard to come by educated people for this subject, but you seem like you know what you’re talking about! Thanks
deep web search dark market link dark web sites links
drug markets dark web deep web drug url tor markets links
tor markets 2024 deep web drug store how to access dark web
free dark web dark web websites dark web market
dark web sites deep web drug url how to access dark web
You’re so cool! I don’t believe I’ve truly read through anything like this before. So good to discover somebody with some genuine thoughts on this subject matter. Seriously.. thank you for starting this up. This site is something that is needed on the web, someone with a little originality.
deep web drug markets dark web site darknet drug market
darknet drugs how to access dark web dark web websites
best darknet markets dark web market links darknet market list
deep web drug url darkmarket list bitcoin dark web
dark internet how to get on dark web tor darknet
dark market url blackweb deep web search
darknet sites dark web site darknet drugs
darkmarket list dark web drug marketplace dark web websites
dark market 2024 darkmarkets deep web sites
deep web drug url darknet websites black internet
drug markets onion blackweb darknet market links
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
darknet drugs tor markets links dark markets
You’re so interesting! I do not believe I have read something like that before. So wonderful to discover somebody with genuine thoughts on this subject. Seriously.. thanks for starting this up. This web site is something that is needed on the web, someone with a little originality.
tor darknet deep web drug markets drug markets onion
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
darkmarket url darknet links blackweb official website
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
dark website dark web sites dark web markets
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
dark markets dark net drug markets dark web
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
dark market 2024 black internet tor darknet
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
dark web links darknet seiten dark markets
dark web site deep web sites dark market onion
dark website darkmarket the dark internet
darknet market links tor markets darknet sites
deep web sites dark internet darknet seiten
darknet market links tor markets links darknet market links
dark web market darknet market links dark net
darkmarket 2024 deep web markets darknet links
dark markets tor market dark market
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
dark web links dark websites darkmarket 2024
darkmarket dark web sites tor darknet
I must thank you for the efforts you have put in writing this site. I really hope to view the same high-grade blog posts by you in the future as well. In truth, your creative writing abilities has inspired me to get my very own website now 😉
deep web drug links dark market 2024 dark market onion
vip79.deal
darknet markets darknet market links deep web sites
darkmarket 2024 how to access dark web darknet drugs
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
deep web sites deep web search darknet site
dark markets dark web sites dark web links
darknet market list darknet market links tor market links
tor market links dark web market links dark market list
deep web drug store dark web link bitcoin dark web
darkmarket link dark websites dark web market
darknet drug market deep web markets https://darknetmarketstore.com/ – dark market url
deep web links tor markets https://darknetmarketstore.com/ – tor markets 2024
blackweb dark web sites links https://darknetmarketstore.com/ – darknet websites
deep web search darkmarket url https://darknetmarketstore.com/ – tor market links
darknet market list dark market https://darknetmarketstore.com/ – tor market links
darknet site dark web link https://darknetmarketstore.com/ – darknet sites
drug markets onion deep web drug markets https://darknetmarketstore.com/ – darknet marketplace
drug markets onion bitcoin dark web https://darknetmarketstore.com/ – dark market 2024
darkmarket dark market link https://darknetmarketstore.com/ – how to access dark web
deep web drug store tor markets links https://darknetmarketstore.com/ – blackweb official website
deep web search deep dark web https://darknetmarketstore.com/ – tor dark web
tor markets links darknet drug market https://darknetmarketstore.com/ – darknet drug store
dark web market how to get on dark web https://darknetmarketstore.com/ – deep dark web
darknet links deep web drug links https://darknetmarketstore.com/ – dark web markets
tor market dark markets https://darknetmarketstore.com/ – tor market
darkmarket 2024 best darknet markets https://darknetmarketstore.com/ – tor market url
dark market link darknet search engine https://darknetmarketstore.com/ – darkmarket 2024
Bu casino’daki slot oyunları beni her seferinde büyük kazançlarla ödüllendiriyor.
You need to be a part of a contest for one of the best websites on the internet. I am going to highly recommend this web site!
dark market url dark web market links https://darknetmarketstore.com/ – the dark internet
dark market onion darknet market https://darknetmarketstore.com/ – how to access dark web
88CLB
tor darknet dark market onion https://darknetmarketstore.com/ – darkweb marketplace
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
black internet tor marketplace https://darknetmarketstore.com/ – darknet market lists
https://km88.band/
darknet drug market darkmarket link https://darknetmarketstore.com/ – dark website
deep web sites best darknet markets https://darknetmarketstore.com/ – darkmarket url
the dark internet dark web websites https://darknetmarketstore.com/ – darknet market list
You’re so interesting! I do not believe I’ve truly read through a single thing like this before. So great to find another person with some original thoughts on this issue. Really.. thank you for starting this up. This site is something that is needed on the web, someone with some originality.
deep web drug markets tor marketplace https://darknetmarketstore.com/ – tor dark web
dark web search engines deep dark web https://darknetmarketstore.com/ – dark web drug marketplace
deep web sites darknet drug market https://darknetmarketstore.com/ – darknet markets 2024
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
dark net tor dark web https://darknetmarketstore.com/ – dark web sites
tor dark web darkmarket url https://darknetmarketstore.com/ – dark web link
darkmarket free dark web https://darknetmarketstore.com/ – darknet site
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
bitcoin dark web darknet site https://darknetmarketstore.com/ – darknet seiten
darknet market darknet market links https://darknetmarketstore.com/ – dark web site
dark web sites links darknet drug links https://darknetmarketstore.com/ – darknet market lists
dark web drug marketplace tor market links https://darknetmarketstore.com/ – darkweb marketplace
drug markets onion dark websites https://darknetmarketstore.com/ – tor market
deep web drug store tor market url https://darknetmarketstore.com/ – tor market links
free dark web dark market onion [url=https://darknetmarketstore.com/ ]dark market url [/url]
dark web market list dark web market list https://darknetmarketstore.com/ – how to get on dark web
blackweb official website darknet drug market https://darknetmarketstore.com/ – blackweb
darknet market links blackweb official website https://darknetmarketstore.com/ – darknet websites
dark web websites dark markets 2024 https://darknetmarketstore.com/ – darknet site
dark web sites links darknet websites https://darknetmarketstore.com/
deep web drug url dark web link https://darknetmarketstore.com/
tor markets 2024 drug markets dark web https://darknetmarketstore.com/
Müşteri desteği 7/24 aktif, her zaman yardımcı oluyorlar.
deep dark web dark web access https://darknetmarketstore.com/
darkmarkets dark web market list https://darknetmarketstore.com/
dark market dark market onion https://darknetmarketstore.com/
Great information. Lucky me I discovered your website by chance (stumbleupon). I’ve book marked it for later!
tor market darknet search engine https://darknetmarketstore.com/
how to get on dark web dark market link https://darknetmarketstore.com/
tor market darknet markets 2024 https://darknetmarketstore.com/
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
dark market url dark websites https://darknetmarketstore.com/
darknet drug market dark web market https://darknetmarketstore.com/
dark web websites dark web market https://darknetmarketstore.com/
darknet market dark web sites links https://darknetmarketstore.com/
deep web drug markets tor darknet https://darknetmarketstore.com/
drug markets onion deep web markets https://darknetmarketstore.com/
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
dark web links dark web access https://darknetmarketstore.com/
tor market links dark market url https://darknetmarketstore.com/
darkmarket url deep web sites https://darknetmarketstore.com/
how to get on dark web darkmarket 2024 https://darknetmarketstore.com/
darknet drug store tor markets 2024 https://darknetmarketstore.com/
dark market deep web drug url https://darknetmarketstore.com/
Good site you’ve got here.. It’s hard to find high quality writing like yours nowadays. I honestly appreciate people like you! Take care!!
deep web search dark markets 2024 https://darknetmarketstore.com/
deep web links dark web websites https://darknetmarketstore.com/
darkmarkets dark web links https://mydarknetmarketlinks.com/
darknet search engine best darknet markets https://mydarknetmarketlinks.com/
darknet site darkweb marketplace https://mydarknetmarketlinks.com/
onion market dark web websites https://mydarknetmarketlinks.com/
An impressive share! I’ve just forwarded this onto a colleague who had been conducting a little homework on this. And he actually ordered me breakfast due to the fact that I found it for him… lol. So let me reword this…. Thanks for the meal!! But yeah, thanx for spending the time to talk about this topic here on your internet site.
dark web link deep web drug store https://mydarknetmarketlinks.com/
blackweb deep web markets https://mydarknetmarketlinks.com/
dark market list dark web drug marketplace https://mydarknetmarketlinks.com/
tor market links darknet market list https://mydarknetmarketlinks.com/
deep web drug store dark internet https://mydarknetmarketlinks.com/
darkmarket 2024 dark net https://mydarknetmarketlinks.com/
tor markets 2024 the dark internet https://mydarknetmarketlinks.com/
dark website tor market https://mydarknetmarketlinks.com/
darkmarket url darkmarket 2024 https://mydarknetmarketlinks.com/
dark market link dark web sites links https://mydarknetmarketlinks.com/
dark web link tor market links https://mydarknetmarketlinks.com/
dark market 2024 dark web sites links https://mydarknetmarketlinks.com/
darknet drugs drug markets onion https://mydarknetmarketlinks.com/
dark web link dark web links https://mydarknetmarketlinks.com/
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
tor market dark web drug marketplace https://mydarknetmarketlinks.com/
Greetings! Very useful advice in this particular post! It’s the little changes which will make the greatest changes. Many thanks for sharing!
Fun88 – Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
darkmarket 2024 darknet links https://mydarknetmarketlinks.com/
dark web sites dark web drug marketplace https://mydarknetmarketlinks.com/
dark market link dark web markets https://mydarknetmarketlinks.com/
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
darknet drug market free dark web https://mydarknetmarketlinks.com/
tor market tor market https://mydarknetmarketlinks.com/
Thanks for any other informative site. Where else may I get that kind of info written in such a perfect method? I’ve a mission that I’m just now operating on, and I’ve been on the look out for such info.
dark internet dark web site https://mydarknetmarketlinks.com/
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
darknet drug links bitcoin dark web https://mydarknetmarketlinks.com/
darknet markets 2024 deep web markets https://mydarknetmarketlinks.com/
Slot oyunlarında kazanmak bu casino’da her zaman çok kolay, şansınızı denemelisiniz!
dark web market darknet websites https://mydarknetmarketlinks.com/
dark net tor markets 2024 https://mydarknetmarketlinks.com/
En sevdiğim slot oyunu Moon Princess, grafikler ve kazançlar mükemmel!
deep web search darknet drug market https://mydarknetmarketlinks.com/
darkmarket url drug markets onion https://mydarknetmarketlinks.com/
Futbol bahislerinde aldığım bonuslar sayesinde her bahis daha kazançlı hale geliyor.
darknet drug store dark market list https://mydarknetmarketlinks.com/
dark web market links tor market https://mydarknetmarketlinks.com/
dark market url dark web access https://mydarknetmarketlinks.com/
dark markets 2024 darknet market https://mydarknetmarketlinks.com/
dark web markets deep web links https://mydarknetmarketlinks.com/
VIP programı çok avantajlı, sadık oyunculara özel bonuslar sunuyorlar.
dark web links darknet marketplace https://mydarknetmarketlinks.com/
Futbol bahislerinde doğru strateji yaparak her zaman kazançlı çıkıyorum!
En sevdiğim slot oyunları arasında Jammin’ Jars ve Razor Shark var, ikisi de çok kazandırıyor.
Casino’nun sunduğu bonuslar sayesinde slot oyunlarında daha fazla kazanıyorum.
Valuable information. Lucky me I found your site accidentally, and I’m surprised why this coincidence
did not took place earlier! I bookmarked it.
darknet drug store tor markets 2024 dark web site
dark web market list deep web sites bitcoin dark web
dark web access blackweb dark web links
deep web sites dark web sites links darkmarket url
drug markets onion tor darknet dark web link
dark web sites links darkmarkets dark web market list
Deneme bonusu ile bahis yaparken hiç para yatırmadan kazanç elde ettim!
darknet sites dark web drug marketplace dark web drug marketplace
darkmarket link dark web sites links dark market
dark market tor markets dark market url
dark web markets darkmarket the dark internet
drug markets dark web tor dark web deep web drug markets
deep web sites blackweb official website darknet markets
Bu casino’da düşük bahislerle oynarken bile büyük ödüller kazanmak mümkün!
darkmarket list darknet market list darkweb marketplace
dark web search engines darknet drugs darknet site
darknet drugs how to get on dark web dark web search engine
Hello there! Would you mind if I share your blog with
my facebook group? There’s a lot of people that I think would really enjoy your content.
Please let me know. Many thanks
Everything is very open with a very clear clarification of the challenges. It was definitely informative. Your website is very useful. Thank you for sharing.
dark web sites links darknet markets 2024 deep web markets
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
darkmarket url dark web sites darknet markets
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
darkmarkets darknet search engine darkmarket
https://sv88.deals/
tor dark web darknet site dark websites
Trực tiếp đá gà BJ388
darkmarket url darknet search engine dark web markets
dark market onion darkmarket best darknet markets
five88
tor darknet tor marketplace dark web market list
blackweb best darknet markets dark markets
Hiếp dâm trẻ em
deep web drug url dark markets 2024 darknet drug links
darknet marketplace dark market blackweb
tor market url dark web access tor markets
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
dark market link tor dark web deep web links
dark market 2024 tor marketplace dark web drug marketplace
Bahis siteleri deneme bonusu ile oyunlara riske girmeden başlamak harika bir fırsat!
darkmarkets dark web site tor markets 2024
Everyone loves it whenever people come together and share ideas. Great website, stick with it.
drug markets onion darkmarket 2024 deep dark web
Hey just wanted to give you a brief heads up and
let you know a few of the pictures aren’t loading properly.
I’m not sure why but I think its a linking issue. I’ve tried it
in two different internet browsers and both show the same outcome.
tor marketplace dark web site dark web search engines
dark web markets dark websites tor dark web
darkmarket 2024 darkmarket link darknet drugs
Bu sitenin sunduğu deneme bonusu ile bedava Aviator oynayarak büyük kazançlar elde ettim!
best darknet markets darknet drug store dark market url
Hello there! I just want to offer you a huge thumbs up for your excellent information you have here on this post. I am coming back to your website for more soon.
deep web sites darknet websites deep web sites
darknet market darknet drugs deep web drug links
free dark web darkmarket tor darknet
dark market list dark market url tor markets links
darknet markets drug markets dark web darknet drug store
deep web markets tor markets links darkmarket list
darknet markets dark market onion dark market onion
dark website dark web search engine darknet links
Sweet blog! I found it while surfing around on Yahoo News. Do you have
any suggestions on how to get listed in Yahoo News? I’ve been trying for a
while but I never seem to get there! Cheers
blackweb official website darknet market darknet market lists
After going over a few of the blog posts on your blog, I truly like your way of blogging. I saved it to my bookmark webpage list and will be checking back soon. Take a look at my web site too and let me know your opinion.
darknet search engine darknet sites onion market
dark websites dark market 2024 blackweb
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
darknet market lists deep web links deep web drug store
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
darkmarket 2024 dark market url best darknet markets
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
dark web websites darkmarket dark market link
best darknet markets darknet market darkmarket
dark web markets dark web market list darkmarket
deep web drug url blackweb official website deep web links
WOW just what I was searching for. Came here by searching for 카지노사이트
dark web link dark web search engine dark website
dark web market dark web market links deep dark web
https://thew14.com/
darknet market links dark web link blackweb official website
deep web drug store dark market url deep dark web
https://fun88.social
dark markets tor markets 2024 dark market list
deep web drug markets dark markets 2024 darknet links
darkmarket darknet site deep web drug links
dark web access darkmarkets tor markets links
dark website tor dark web dark web market list
dark web drug marketplace deep web links black internet
dark web links onion market darknet links
dark web site dark market darknet market list
Good day! Do you use Twitter? I’d like to follow
you if that would be okay. I’m definitely enjoying your blog and
look forward to new updates.
dark web link dark net darknet market list
deep web links dark web link how to get on dark web
dark market 2024 darkweb marketplace dark web site
darkmarket link deep web markets darkmarket url
blackweb darkmarkets darknet market links
darknet market list tor markets darknet search engine
darknet links deep web markets darknet market
darknet markets dark web market drug markets onion
tor market links best darknet markets darknet websites
deep web sites best darknet markets darknet market list
dark internet darknet seiten tor market url
darknet drug links blackweb tor market
dark net darknet market tor markets
tor darknet darkmarket url how to access dark web
I do not know whether it’s just me or if perhaps everybody else encountering issues with your blog.
It seems like some of the written text on your posts are
running off the screen. Can somebody else please comment and let me know if this is happening to them too?
This might be a issue with my internet browser because
I’ve had this happen previously. Cheers
https://top88.guide
how to access dark web how to access dark web deep web sites
Having read this I believed it was very informative. I appreciate you taking the time and effort to put this article together. I once again find myself personally spending a significant amount of time both reading and commenting. But so what, it was still worthwhile!
deep dark web darknet drugs blackweb
tor market onion market dark web sites
dark web sites links darknet marketplace tor market
darknet markets 2024 dark markets dark web market
dark web sites links deep web sites how to access dark web
deep web search onion market blackweb official website
deep web drug markets deep web drug url dark market link
how to access dark web tor market links how to get on dark web
darkmarkets darknet market lists deep web drug markets
darknet marketplace tor markets dark websites
very successful thank you, journalinsights
deep web drug links darknet search engine blackweb
deep web drug url dark market dark market onion
Right here is the right website for anybody who hopes to find out about this topic. You understand a whole lot its almost hard to argue with you (not that I actually would want to…HaHa). You definitely put a brand new spin on a subject that has been discussed for ages. Great stuff, just great.
dark web access dark web websites darkweb marketplace
h7sc5y
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
You made some good points there. I looked on the net for more information about the issue and found most people will go along with your views on this website.
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
very successful thank you, chemistryres
very successful thank you, imedresearch
very successful thank you, biochemresearch
very successful thank you, imedpubjournals
Crash oyunları arasında Aviator en kazançlısı, deneme bonusu ile risksiz oynayarak büyük ödüller kazanıyorum!
Deneme bonusu ile bahis yapmak, riske girmeden kazanç elde etmenin en iyi yolu!
Bu casino’daki slot oyunları beni her seferinde büyük kazançlarla ödüllendiriyor!
Everything is very open with a precise explanation of the issues. It was definitely informative. Your website is extremely helpful. Thanks for sharing!
very successful thank you, scitecjournals
very successful thank you, longdomjournals
Hello there! This article could not be written much better! Looking at this post reminds me of my previous roommate! He always kept talking about this. I’ll send this article to him. Fairly certain he’ll have a great read. Many thanks for sharing!
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
Bu casino sitesi her hafta yeni slot oyunları ekliyor, sıkılmak imkansız.
very successful thank you, imedpubjournal
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
very successful thank you, scitechjournal
It’s nearly impossible to find educated people in this particular topic, but you sound like you know what you’re talking about! Thanks
Bu sitenin sunduğu deneme bonusu sayesinde kazançlı bir başlangıç yaptım!
Ödeme yöntemleri çok çeşitli, bu harika!
Casino’nun sunduğu promosyonlar futbol bahislerinde ekstra şans sağlıyor!
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
Bu siteye üye olur olmaz deneme bonusu aldım ve hemen kazanç sağladım!
mk sport vi phạm đạo đức làm người
Spot on with this write-up, I honestly think this web site needs much more attention. I’ll probably be returning to read more, thanks for the info.
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
very successful thank you, jopenaccess
Bahis siteleri deneme bonusu ile oyunlara bedava başlamak çok keyifli!
I know this if off topic but I’m looking into starting my own weblog and
was wondering what all is required to get set up?
I’m assuming having a blog like yours would cost a pretty penny?
I’m not very web savvy so I’m not 100% positive.
Any tips or advice would be greatly appreciated.
Appreciate it
I delight in, cause I found exactly what I used to be looking for.
You have ended my 4 day long hunt! God Bless you man. Have a nice day.
Bye
Slot oyunlarının çeşitliliği sayesinde bu casino’da her gün farklı bir oyun deniyorum.
It’s a pity you don’t have a donate button! I’d without a doubt donate to
this fantastic blog! I suppose for now i’ll settle for book-marking and adding your RSS
feed to my Google account. I look forward to brand
new updates and will talk about this blog with my Facebook
group. Chat soon!
Deneme bonusu sayesinde hiçbir para yatırmadan kazanmaya başladım!
Canlı casino ve slotların birleşimi, bu siteyi rakipsiz yapıyor.
After looking into a number of the blog posts on your site, I seriously like your way of blogging. I book marked it to my bookmark site list and will be checking back soon. Take a look at my website too and tell me what you think.
These medications may worsen kidney function if taken together, potentially causing kidney failure DailyMed, 2019 cytotec tablet price in pakistan Juhaimi FA, Ghafoor K, Babiker EE et al 2018 Influence of storage and roasting on the quality properties of kernel and oils of raw and roasted peanuts
En sevdiğim slot oyunu Jammin’ Jars, her spin büyük bir heyecan ve kazanç sağlıyor.
Deneme bonusu ile hiçbir para yatırmadan kazandım, herkese tavsiye ederim!
Casino’nun sunduğu turnuvalar ile ekstra ödüller kazanmak çok eğlenceli ve kazançlı!
Greetings! Very useful advice in this particular post! It’s the little changes that produce the biggest changes. Thanks for sharing!
https://789club.ong
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
https://zbet.boo
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
https://debet.men
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
vip79.deal
darknet drug store dark web sites bitcoin dark web
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
dark market onion deep web sites deep web sites
darknet sites dark net dark web access
Bu casino’nun sunduğu slot oyunları gerçekten büyük kazanç fırsatları sunuyor.
dark market list dark web sites links tor market
blackweb official website dark market link tor markets
best darknet markets best darknet markets tor dark web
tor dark web tor dark web darkmarket
tor dark web dark market list dark market 2024
Casino’nun sunduğu bonuslar ve turnuvalar sayesinde slot oyunlarında daha fazla kazanıyorum.
dark web access darknet markets 2024 darknet drug links
darkmarket url tor markets 2024 darknet markets
tor market links darknet marketplace tor marketplace
deep web sites dark web search engines dark market onion
dark web market darkmarket list darknet search engine
darknet market lists darkmarkets deep web drug store
drug markets dark web tor dark web darknet sites
Deneme bonusu sayesinde Aviator gibi crash oyunlarında hiç para kaybetmeden kazandım!
dark market link darknet websites the dark internet
how to get on dark web deep dark web darkmarket
tor markets 2024 dark web site deep web sites
darknet links darkmarket list dark web sites links
Her gün bu casino’daki slot oyunlarında büyük kazançlar elde ediyorum.
dark markets 2024 dark web market links darknet marketplace
darkmarket dark market link deep web links
dark web search engines darknet seiten dark websites
darknet market links dark web search engines how to get on dark web
dark market list darknet market dark internet
dark web access deep web drug store darknet market links
Bahis siteleri deneme bonusu ile bedava bahis yaparak büyük ödüller kazanmak çok kolay!
deep web markets darknet market links dark web search engine
dark market link dark market url free dark web
darknet drug market darkmarket list dark web market list
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
This blog was… how do you say it? Relevant!! Finally I have found something which helped me. Many thanks.
bitcoin dark web darknet site drug markets dark web
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
dark market 2024 drug markets onion deep web links
darknet market list tor marketplace dark market url
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
dark net darkmarkets deep web links
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
This is an optional argument to define the IAM policy name.
✦ description:- This is an optional argument to provide more details about the IAM policy.
✦ policy:- This is a ma속초출장샵ndatory argument to JSON policy document.
dark web sites links darknet marketplace dark web market list
dark markets dark web search engines darkmarket 2024
darknet seiten free dark web dark web links
I truly love your blog.. Very nice colors & theme. Did you build this website yourself? Please reply back as I’m wanting to create my own personal site and would like to find out where you got this from or exactly what the theme is named. Thanks!
tor dark web deep dark web drug markets onion
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
deep dark web dark web markets dark web market
very successful thank you, holemans
darkmarket link darknet drug store tor market
darknet seiten dark web websites dark market onion
deep dark web dark market dark web links
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
very successful thank you, homedelano
deep web drug store darkmarket 2024 darknet seiten
Bahis sitelerinde deneme bonusu ile oyunlara sıfır yatırımla başlamak çok kolay!
dark web market links dark net deep web sites
tor dark web deep dark web tor market url
darknet markets darkmarket link darknet drug store
dark websites darknet markets dark market list
blackweb official website darkmarket list darkmarket url
Casino’nun sunduğu promosyonlar sayesinde slot oyunlarında her zaman şansım artıyor.
dark web link drug markets onion drug markets dark web
onion market tor markets tor market links
dark market url dark market blackweb
tor markets 2024 dark web market dark web drug marketplace
darkmarket deep web drug links dark market 2024
dark web sites links darkmarket 2024 deep web drug url
experience and quality thank you.greenrecuperi
Casino’daki slot oyunları ile büyük jackpot kazanmak gerçekten mümkün, denemeye değer!
darknet drug links deep web drug links dark web sites
darkmarket 2024 tor markets links blackweb official website
experience and quality thank you.grossoregistratori
You are so interesting! I do not suppose I’ve truly read a single thing like that before. So nice to find another person with a few genuine thoughts on this subject matter. Seriously.. thank you for starting this up. This web site is something that is required on the internet, someone with some originality.
darknet drug store drug markets onion darkmarket list
darknet market black internet deep web links
experience and quality thank you.hotelpisa
the dark internet tor markets darknet sites
darkmarket dark web market dark web link
Bahis siteleri deneme bonusu ile oyunlara başlamak hiç bu kadar kolay olmamıştı!
tor market url black internet darknet links
dark net dark web search engines https://mydarknetmarketlinks.com/ – dark web drug marketplace
I used to be able to find good advice from your content.
Bahis miktarımı ayarlayarak Starburst’ta büyük ödüller kazandım!
Quay lén phụ nữ
Sex trẻ em
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
I needed to thank you for this good read!! I certainly enjoyed every bit of it. I’ve got you book marked to look at new things you post…
https://789club60.com/
https://iwin.international/
very successful thank you, hotelalcantara
very successful thank you, ismllw
I blog frequently and I genuinely appreciate your information. This article has really peaked my interest. I’m going to bookmark your site and keep checking for new details about once a week. I opted in for your RSS feed as well.
very successful thank you, jamaistropdart
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
Yüksek bahislerle oynadığım futbol bahislerinden büyük kazançlar elde ettim!
Bu bahis sitesinin sunduğu deneme bonusu ile bedava bahis yaparak anında kazanç sağladım!
experience and quality thank you.igiardinidibeatrice
Great web site you have here.. It’s hard to find excellent writing like yours nowadays. I really appreciate people like you! Take care!!
Saved as a favorite, I like your web site!
experience and quality thank you.impianti-antizanzare
Casino’nun sunduğu bonuslar futbol bahislerinde ekstra kazanç sağlıyor!
Some truly interesting points you have written.Aided me a lot, just what I was looking for : D.
experience and quality thank you.irrigazione-giardini
Good article. I will be dealing with many of these issues as well..
En sevdiğim slot oyunu Legacy of Dead, her spin büyük bir heyecan ve kazanç sağlıyor.
https://789club24.com/
https://iwin.locker/
https://8xbet1880.com/
En sevdiğim slot oyunu Legacy of Dead, grafikler harika, kazançlar büyük!
https://i9bett.us/
https://8xbet1881.com/
https://i9bett.us/
https://iwinvn.app/
Great post! We are linking to this particularly great article on our site. Keep up the good writing.
https://888bj.net/
https://iwinvn.live/
https://sunwin.education/
789 club
https://bj8882.com/
Hi to every one, the contents present at this web site are genuinely awesome for people experience,
well, keep up the good work fellows.
https://kubetvn88.com/
BJ88
Yüksek bahislerle Razor Shark’ta oynadığımda büyük kazançlar elde ediyorum!
https://bj8883.com/
Oh my goodness! Amazing article dude! Many thanks, However I am experiencing problems with your RSS. I don’t understand the reason why I am unable to join it. Is there anybody having similar RSS issues? Anyone that knows the solution will you kindly respond? Thanx.
Tải Go88
BJ88
GO 88
En sevdiğim slot oyunu Thunderstruck II, her zaman büyük kazançlar elde ediyorum.
Futbol bahislerinde strateji yaparak her maçtan kazançlı çıkıyorum!
Hello! I could have sworn I’ve been to this web site before but after looking at a few of the articles I realized it’s new to me. Anyhow, I’m definitely delighted I discovered it and I’ll be book-marking it and checking back regularly.
Düşük bahislerle futbol maçlarına oynuyorum, ama her zaman kazanç fırsatları yakalıyorum!
You may additionally need to indicate that you have an “emergency fund” financial savings account, in case of surprise expenses.
Bahis seçeneklerinin geniş olması sayesinde her oyunda kazanç fırsatlarını yakalıyorum.
BJ88
33win
Great post! We will be linking to this particularly great content on our website. Keep up the great writing.
Tải Go88
33win
Good blog you’ve got here.. It’s hard to find quality writing like yours nowadays. I honestly appreciate individuals like you! Take care!!
very successful thank you, labandas
very successful thank you, laresidencelepartage
I really love your blog.. Great colors & theme. Did you create this amazing site yourself? Please reply back as I’m hoping to create my own personal site and want to know where you got this from or exactly what the theme is named. Many thanks.
very successful thank you, laurenty.globalnet
very successful thank you, ldclean
Slot oyunlarında her spin heyecan verici, bu casino’da kazanmak çok kolay!
Wonderful post! We will be linking to this particularly great content on our site. Keep up the great writing.
Casino’nun sunduğu promosyonlar ile bahislerim her zaman daha kazançlı hale geliyor.
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
There is definately a great deal to find out about this topic. I love all of the points you’ve made.
Slot oyunlarında kazanmak hiç bu kadar eğlenceli olmamıştı, kesinlikle tavsiye ederim!
Go88
A motivating discussion is definitely worth comment. I think that you should publish more about this subject matter, it may not be a taboo matter but generally people do not speak about such subjects. To the next! Cheers!
https://fb88link1.com/
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
777 loc
very successful thank you, lesgensdere
A fascinating discussion is worth comment. I do think that you ought to write more on this issue, it might not be a taboo matter but generally people don’t speak about these subjects. To the next! All the best.
https://vgo88.net/
vip66
Consultants group has enabled to drag all of the element of function accurately as well as on time.
Viviane Geppert (episodes 1-3) and Annemarie Carpendale (episode 4) had been the presenters of the present.
Iris Wildthyme, a Time Lady appears in the Scarlet Empress, The Blue Angel and Mad Canines and Englishmen.
vip 66
very successful thank you, poi.defigners
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
I’m very pleased to discover this great site. I need to to thank you for your time for this particularly fantastic read!! I definitely loved every bit of it and I have you saved to fav to see new information in your web site.
Bu casino’daki jackpot slot oyunları ile büyük kazançlar elde etmek mümkün!
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
I blog quite often and I genuinely thank you for your information. This article has really peaked my interest. I’m going to book mark your blog and keep checking for new information about once per week. I opted in for your RSS feed too.
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
Everyone loves it when folks get together and share ideas. Great website, stick with it.
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
게임을 개발하는 것이 쉽지 않다 보니 대부분의 사이트는 고작 인기 게임 몇 개만 준비하는 경우가 많습니다.
There’s certainly a lot to know about this issue. I really like all the points you made.
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
https://hitclub.shiksha
Good blog post. I definitely appreciate this site. Continue the good work!
Reliable HVAC Repair Services https://serviceorangecounty.com stay comfortable year-round with our professional HVAC repair services. Our experienced team is dedicated to diagnosing and resolving heating, cooling, and ventilation issues quickly and effectively.
Reliable HVAC Repair Services https://serviceorangecounty.com stay comfortable year-round with our professional HVAC repair services. Our experienced team is dedicated to diagnosing and resolving heating, cooling, and ventilation issues quickly and effectively.
789club
b52club
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
iwin
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
An interesting discussion is definitely worth comment. I do believe that you ought to publish more on this subject matter, it may not be a taboo matter but generally folks don’t talk about such issues. To the next! Kind regards!
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
온라인 카지노의 다양한 매력을 경험하고 싶으신 분들, 지금 바로 카지노 사이트 추천을 확인해보세요. 최고의 베팅 사이트에서 특별한 경험를 경험하실 수 있습니다.
experience and quality thank you.italianvistatravel
I’m amazed, I have to admit. Seldom do I encounter a blog that’s both educative and engaging, and without a doubt, you have hit the nail on the head. The issue is something that not enough men and women are speaking intelligently about. Now i’m very happy I came across this in my hunt for something regarding this.
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
experience and quality thank you.ilmacinapepe
Your style is unique compared to other folks I’ve read stuff from. Many thanks for posting when you’ve got the opportunity, Guess I will just bookmark this site.
Blackjack stratejilerimi geliştirmek için buradaki oyunları kullandım, sonuçlar harika!
I blog often and I really appreciate your content. This great article has truly peaked my interest. I’m going to bookmark your blog and keep checking for new details about once per week. I opted in for your RSS feed as well.
bookmarked!!, I like your website.
Her hafta yeni turnuvalar var, kazanma şansı hiç bitmiyor.
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
one88
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
Sun win
I really love your site.. Pleasant colors & theme. Did you build this site yourself? Please reply back as I’m looking to create my very own site and want to find out where you got this from or what the theme is named. Thanks!
Can I simply say what a comfort to discover somebody that actually understands what they’re talking about on the web. You actually realize how to bring an issue to light and make it important. A lot more people really need to check this out and understand this side of the story. It’s surprising you’re not more popular since you most certainly have the gift.
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
Sunwin
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
very successful thank you, biomedic
very successful thank you, bdsit
sugar defender reviews I’ve dealt
with blood sugar variations for several years, and it actually influenced my power
degrees throughout the day. Considering that beginning Sugar Protector,
I feel more well balanced and sharp, and I do not experience those mid-day slumps
anymore! I love that it’s an all-natural service that
works without any rough side effects. It’s absolutely been a game-changer for me
Bu casino’daki futbol bahisleri ile her maçta kazanç fırsatları buluyorum!
You made some really good points there. I checked on the web to learn more about the issue and found most people will go along with your views on this web site.
very successful thank you, chams
Spot on with this write-up, I absolutely feel this amazing site needs a lot more attention. I’ll probably be returning to read through more, thanks for the info.
Slot oyunlarında büyük kazançlar elde ettim, bu casino en iyisi!
Futbol bahislerinde stratejik oynayarak her zaman kazançlı çıkıyorum!
33win
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
888 b
Right here is the right blog for everyone who really wants to find out about this topic. You know a whole lot its almost tough to argue with you (not that I actually would want to…HaHa). You certainly put a new spin on a topic that has been discussed for many years. Excellent stuff, just excellent.
nhà cái 8xbet
https://kufun1.fun
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
https://bongvip88.club/
https://manclubs.live/
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
https://hitclub.flowers
https://vip79.forum
very successful thank you, medinet
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
very successful thank you, bicotec
Spot on with this write-up, I absolutely feel this amazing site needs a lot more attention. I’ll probably be returning to see more, thanks for the information.
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
In addition to being entertaining, the upgraded Slice Master incorporates gamification elements to improve cognitive skills. Players are encouraged to develop quick reflexes, hand-eye coordination, and strategic thinking through slicing challenges. The game subtly teaches players to focus and make split-second decisions, making it both fun and educational. This unique blend of gameplay and skill-building ensures that Slice Master offers more than just entertainment. Website: https://slicemaster.net/about-us
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
very successful thank you, ans-nettoyage
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
very successful thank you, neodeme
Mobil versiyonu da çok iyi çalışıyor, istediğim her yerden oynuyorum.
very successful thank you, frigo-clim
Excellent post! We are linking to this great post on our website. Keep up the great writing.
You should take part in a contest for one of the highest quality websites on the internet. I will highly recommend this site!
Way cool! Some extremely valid points! I appreciate you writing this write-up and also the rest of the website is very good.
Slotlarda kazanmak bu casino’da her zamankinden daha kolay, herkese tavsiye ederim!
soap2day online streaming soap2day music
АО Ти И Эл Лизинг https://avtee.ru предлагает услуги проката автомобилей в России, Турции, ОАЭ, Черногории, Испании и других странах по всему миру. Широкий выбор авто, выгодные условия и удобное бронирование делают поездки комфортными и доступными для каждого клиента.
I quite like reading an article that will make men and women think. Also, many thanks for allowing for me to comment.
It’s hard to find knowledgeable people on this topic, but you sound like you know what you’re talking about! Thanks
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
iwin
Vip66
iwin
very successful thank you, bestbaby
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
very successful thank you, nova-euro-fashion
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
Good post. I learn something new and challenging on blogs I stumbleupon on a daily basis. It will always be interesting to read through content from other writers and use a little something from their web sites.
very successful thank you, thebestoffairfax
very successful thank you, thebestoflittlerock
Deneme bonusu ile bahis yaparken hiç para kaybetmeden büyük ödüller kazandım!
Excellent post. I am dealing with a few of these issues as well..
Bahis siteleri deneme bonusu ile oyuna sıfır yatırım yaparak büyük kazançlar elde ettim!
двери межкомнатные купить в спб входная дверь
Bu bahis sitesinin sunduğu deneme bonusu ile risksiz bahis yaparak anında kazanç sağladım.
This is a very good tip particularly to those new to the blogosphere. Simple but very accurate information… Many thanks for sharing this one. A must read post!
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
There is certainly a great deal to find out about this topic. I really like all of the points you made.
very successful thank you, thebestofportland
The next time I read a blog, Hopefully it doesn’t fail me as much as this one. After all, I know it was my choice to read, nonetheless I actually believed you’d have something interesting to say. All I hear is a bunch of moaning about something you can fix if you were not too busy looking for attention.
very successful thank you, thebestofwilmington
Phim sex trẻ em
You ought to take part in a contest for one of the highest quality sites online. I’m going to highly recommend this blog!
Profile of Common Demographic Characteristics: 2010 for Bordentown metropolis, New Jersey Division of Labor and Workforce Development.
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
акб купить в спб интернет магазин аккумуляторов для автомобилей
межевание участка ленинградская область mezhevanie-spb.ru
генератор для частного дома 5 квт бензиновый цена https://tss-generators.ru
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
experience and quality thank you.malermester-blakstad
sodo66com
https://sun-win.fund
View Adam Graham Newsletter Now for business startup tips
experience and quality thank you.martemoen
Plinko se ha convertido https://medium.com/@kostumchik.kiev.ua/todo-sobre-el-juego-de-plinko-en-m%C3%A9xico-instrucciones-demos-opiniones-y-m%C3%A1s-d1fde2d99338 en una de las opciones favoritas de los jugadores de casinos en Mexico. Conocido por su simplicidad y gran potencial de ganancias, este adictivo juego ahora cuenta con una plataforma oficial en Mexico.
Онлайн-журнал о строительстве https://zip.org.ua практичные советы, современные технологии, тренды дизайна и архитектуры. Всё о строительных материалах, ремонте, благоустройстве и инновациях в одной удобной платформе.
experience and quality thank you.myrtun
рейтинг онлайн казино казино на деньги хорошее
That is a very good tip particularly to those fresh to the blogosphere. Short but very precise information… Many thanks for sharing this one. A must read post.
Its like you read my mind! You appear to know so much about
this, like you wrote the book in it or something.
I think that you could do with some pics to drive the message home a bit, but other than that,
this is excellent blog. A fantastic read. I’ll certainly be back.
Düşük bahislerle oynadığım futbol bahislerinde bile sürekli kazanç elde ediyorum!
789Club
Hi to every body, it’s my first pay a quick visit of this website; this
website consists of awesome and truly excellent information designed for visitors.
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
i9bet
i9bet
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
vin88
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
The global demand for jewelries like has elevated exponentially since the last decade.
xoso66
https://loto188.dance
Good write-up. I certainly love this site. Keep writing!
https://12bet.actor
ee88
very successful thank you, sanilabcorp
https://888b.okinawa
very successful thank you, sescoindustries
You are so awesome! I don’t believe I’ve truly read a single thing like this before. So wonderful to discover somebody with a few genuine thoughts on this subject matter. Really.. thanks for starting this up. This web site is one thing that is needed on the web, someone with a bit of originality.
experience and quality thank you.nykran.bolkan
интернет магазин секс игрушек https://sex-shop-dp.top
лучший секс шоп https://sex-shop-kh.top
experience and quality thank you.plussplan
Good post. I learn something totally new and challenging on sites I stumbleupon every day. It will always be helpful to read content from other authors and practice a little something from their web sites.
One is in a layered costume of pink with small black bows; her colleague is in a plain black costume with a matching giant bow.
Hi, I do believe this is a great site. I stumbledupon it 😉 I will revisit yet again since i have bookmarked it. Money and freedom is the greatest way to change, may you be rich and continue to help other people.
I like the helpful information you provide in your articles.
I will bookmark your weblog and check again here regularly.
I’m quite certain I’ll learn a lot of new stuff right here!
Best of luck for the next!
Futbol bahislerinde aldığım bonuslar sayesinde her zaman kazançlı çıkıyorum!
Darth Tenebrous is a extra necessary figure within the Legends continuity, where he was Darth Plagueis’ grasp and possessed an unusual ability to foresee the long run, together with his personal loss of life.
Everything is very open with a precise clarification of the challenges. It was truly informative. Your site is very helpful. Many thanks for sharing!
Poff, Zack (August 29, 2021).
8kbet
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
Рейтинг лучших онлайн-казино https://lastdepcasino.ru с быстрыми выплатами и честной игрой. Подробные обзоры, бонусы для новых игроков и актуальные акции.
Slot oyunlarının heyecanı başka hiçbir yerde bu kadar iyi değil!
Bu sitede güvenle oynayabilirsiniz, tamamen lisanslı bir platform.
the dark internet darknet seiten https://mydarknetmarketlinks.com/ – onion market
Cat Clothing https://petluxe.life/collections/cats
Your style is so unique in comparison to other people I’ve read stuff from. Thanks for posting when you’ve got the opportunity, Guess I will just book mark this site.
Ваш гид в мире автомобилей https://clothes-outletstore.com тест-драйвы, советы по ремонту и последние тенденции индустрии.
Автомобильный журнал https://automobile.kyiv.ua с фокусом на практичность. Ремонт, уход за авто, обзор технологий и советы по эксплуатации.
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
After looking into a number of the blog articles on your web site, I seriously like your way of blogging. I saved it to my bookmark website list and will be checking back soon. Take a look at my website as well and let me know how you feel.
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
yo88club.app
Всё о машинах https://avtomobilist.kyiv.ua тест-драйвы, сравнения моделей, авто новости, советы по ремонту и уходу.
Авто журнал https://avtonews.kyiv.ua новости автопрома, сравнения моделей, тест-драйвы, советы по ремонту и уходу.
Авто портал https://autonovosti.kyiv.ua актуальные новости, обзоры авто, тест-драйвы, инструкции по ремонту и тюнингу. Минимум текста, максимум полезной информации.
Всё о машинах https://black-star.com.ua авто новости, тест-драйвы, обзоры моделей, рейтинги, инструкции по обслуживанию и ремонту.
Generally I do not learn post on blogs, but I wish to say that this write-up very compelled me to check out and do so! Your writing style has been amazed me. Thanks, quite nice post.
Всё о машинах https://avtomobilist.kyiv.ua тест-драйвы, сравнения моделей, авто новости, советы по ремонту и уходу.
Авто журнал https://avtonews.kyiv.ua новости автопрома, сравнения моделей, тест-драйвы, советы по ремонту и уходу.
Авто портал https://autonovosti.kyiv.ua актуальные новости, обзоры авто, тест-драйвы, инструкции по ремонту и тюнингу. Минимум текста, максимум полезной информации.
Всё о машинах https://black-star.com.ua авто новости, тест-драйвы, обзоры моделей, рейтинги, инструкции по обслуживанию и ремонту.
2013-2014 South Korean romantic comedy tv collection starring Jang Keun-suk, Lee Ji-eun, Lee Jang-woo, and Han Chae-younger.
Very good article. I’m experiencing some of these issues as well..
Всё о самогоноварении https://brewsugar.ru на одном сайте: от истории напитка до современных технологий перегонки.
Всё об авто https://road.kyiv.ua в одном месте: новости, тест-драйвы, сравнения, характеристики, ремонт и уход. Автомобильный онлайн-журнал — ваш эксперт в мире машин.
Место для общения на любые темы https://xn--9i1b12ab68a.com/ актуальные вопросы, обмен опытом, интересные дискуссии. Здесь найдётся тема для каждого.
Перевозка товаров из Китая https://chinaex.ru в Россию под ключ: авиа, море, автотранспорт. Гарантия сроков и сохранности груза.
Wonderful beat ! I would like to apprentice while you amend your site, how could i subscribe for a blog site? The account helped me a acceptable deal. LSAT Analytical Reasoning I had been tiny bit acquainted of this your broadcast offered bright clear concept.
Casino’daki slot oyunlarıyla büyük jackpotlara ulaşmak mümkün, denemelisiniz!
I couldn’t refrain from commenting. Exceptionally well written!
In 1853 JW Randolph and Company republished the work and included numerous supplies from the property supplied by Jefferson’s literary executor, Thomas Jefferson Randolph.
Женский портал https://abuki.info мода, красота, здоровье, семья, карьера. Советы, тренды, лайфхаки, рецепты и всё, что важно для современных женщин.
Автомобильный онлайн-журнал https://simpsonsua.com.ua предлагает свежие новости, обзоры авто, тест-драйвы, рейтинги и полезные советы для водителей.
Мода, здоровье, красота https://gratransymas.com семья, кулинария, карьера. Женский портал — полезные советы и свежие идеи для каждой.
Познавательный портал для детей https://detiwki.com.ua обучающие материалы, интересные факты, научные эксперименты, игры и задания для развития кругозора.
whoah this blog is great i love reading your articles. Keep up the great work! You know, a lot of people are hunting around for this info, you could aid them greatly.
Good information. Lucky me I found your website by chance (stumbleupon). I have saved it for later!
Женский онлайн-журнал https://womanfashion.com.ua секреты красоты, модные тренды, здоровье, отношения, семья, кулинария и карьера. Всё, что важно и интересно.
Discover the latest game codes https://pocket-codes.com detailed guides, and expertly crafted tier lists to enhance your gaming experience. Unlock rewards, master strategies, and dominate every level with our curated content. Perfect for gamers seeking an edge!
деловая офисная мебель https://ковка116.рф
Женский онлайн-журнал https://stylewoman.kyiv.ua стиль, уход, здоровье, отношения, семья, кулинарные рецепты, психология и карьера.
En sevdiğim slot oyunu Starburst, grafikler mükemmel, kazançlar çok büyük!
Spot on with this write-up, I really believe that this amazing site needs much more attention. I’ll probably be back again to read through more, thanks for the advice.
https://ee88.love
Туристический портал https://aliana.com.ua лучшие маршруты, путеводители, советы путешественникам, обзоры отелей.
мебель офисная купить в спб https://ковка116.рф
Всё о туризме https://atrium.if.ua маршруты, путеводители, советы по отдыху, обзор отелей и лайфхаки. Туристический портал — ваш помощник в путешествиях.
Всё для путешествий https://cmc.com.ua уникальные маршруты, гиды по городам, актуальные акции на туры и полезные статьи для туристов.
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
May I simply say what a relief to uncover somebody who really understands what they are discussing on the web. You definitely understand how to bring an issue to light and make it important. More and more people should read this and understand this side of your story. It’s surprising you are not more popular given that you most certainly possess the gift.
very successful thank you, smithoilcompany
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
very successful thank you, spantecsystems
I haven’t checked in here for some time because I thought it was getting boring, but the last few posts are really good quality so I guess I’ll add you back to my daily bloglist. You deserve it my friend. insurance guides
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
nhà cái Yeu88
very successful thank you, springeroilltd
Статьи о путешествиях https://deluxtour.com.ua гиды по направлениям, лайфхаки для отдыха, советы по сбору багажа и туристические обзоры.
Путешествия по Греции https://cpcfpu.org.ua лучшие курорты, гиды по островам, экскурсии, пляжи и советы по планированию отпуска.
Туристический журнал https://elnik.kiev.ua свежие идеи для путешествий, обзоры курортов, гиды по городам, советы для самостоятельных поездок и туристические новости.
very successful thank you, sweetkarmadesserts
Туристический портал https://feokurort.com.ua необычные маршруты, вдохновляющие истории, секреты бюджетных путешествий, советы по визам и топовые направления для отдыха.
I am not real superb with English but I find this very leisurely to understand .
Bu casino’nun sunduğu canlı bahis seçenekleri futbol maçlarını izlerken ekstra heyecan katıyor!
After I initially commented I appear to have clicked the -Notify me when new comments are added- checkbox and now whenever a comment is added I get 4 emails with the same comment. Is there a means you are able to remove me from that service? Many thanks.
very successful thank you, tacticalpublicrelations
Статьи о туризме и путешествиях https://inhotel.com.ua маршруты, гиды по достопримечательностям, советы по планированию поездок, рекомендации по отелям и лайфхаки для туристов.
Гиды по странам https://hotel-atlantika.com.ua экскурсии по городам, советы по выбору жилья и маршрутов. Туристический журнал — всё для комфортного и яркого путешествия.
Комплексный ремонт квартир https://anti-orange.com.ua и домов от Студии ремонта. Полный цикл работ: от дизайна до финишной отделки.
I have to thank you for the efforts you’ve put in writing this website. I am hoping to view the same high-grade blog posts from you in the future as well. In truth, your creative writing abilities has motivated me to get my own, personal website now 😉
Spot up for this write-up, I must say i think this excellent website wants much more consideration. I’ll more likely once more to see far more, thank you for that information.
Строительная компания https://as-el.com.ua выполняем строительство жилых и коммерческих объектов под ключ. Полный цикл: проектирование, согласование, строительство и отделка.
На строительном портале https://avian.org.ua вы найдете всё: от пошаговых инструкций до списка лучших подрядчиков. Помогаем реализовать проекты любой сложности быстро и удобно.
Строительный портал https://ateku.org.ua ваш гид в мире строительства и ремонта. Полезные статьи, обзоры материалов, советы по выбору подрядчиков и идеи дизайна.
Портал по ремонту https://azst.com.ua всё для вашего ремонта: подбор подрядчиков, советы по выбору материалов, готовые решения для интерьера и проверенные рекомендации.
Bu sitede kazandığım parayı hızlıca çekebildim, çok güvenilir.
Всё о ремонте на одном сайте https://comart.com.ua Портал по ремонту предлагает обзоры материалов, рейтинги специалистов, советы экспертов и примеры готовых проектов для вдохновения.
Having read this I thought it was rather informative. I appreciate you taking the time and effort to put this article together. I once again find myself spending a significant amount of time both reading and commenting. But so what, it was still worth it.
Журнал по ремонту https://domtut.com.ua и строительству – советы, идеи и обзоры. Узнайте о трендах, изучите технологии и воплотите свои строительные или дизайнерские задумки легко и эффективно.
Портал о ремонте https://eeu-a.kiev.ua всё для тех, кто ремонтирует: пошаговые инструкции, идеи дизайна, обзор материалов и подбор подрядчиков.
Журнал по ремонту и строительству https://diasoft.kiev.ua гид по современным тенденциям. Полезные статьи, лайфхаки, инструкции и обзор решений для дома и офиса.
En sevdiğim slot oyunu Legacy of Dead, her spin büyük bir kazanç fırsatı sunuyor.
Новости технологий https://helikon.com.ua все о последних IT-разработках, гаджетах и научных открытиях. Свежие обзоры, аналитика и тренды высоких технологий.
оценка профессиональных рисков в строительстве Москва https://ocenka-riskov-msk.ru
https://b52club.select
8live
Строительный онлайн журнал https://inter-biz.com.ua руководства по проектам любой сложности. Советы экспертов, подбор материалов, идеи дизайна и новинки рынка.
Сайт о строительстве и ремонте https://hydromech.kiev.ua полезные советы, инструкции, обзоры материалов и технологий. Все этапы: от фундамента до отделки.
Строительные технологии https://ibss.org.ua новейшие разработки и решения в строительной сфере. Материалы, оборудование, инновации и тренды для профессионалов и застройщиков.
8live
https://zbet100.net/
Oh my goodness! Awesome article dude! Thank you so much, However I am having difficulties with your RSS. I don’t know the reason why I am unable to join it. Is there anybody else getting identical RSS problems? Anyone who knows the answer can you kindly respond? Thanx!!
Все о строительстве и ремонте https://kennan.kiev.ua практичные рекомендации, идеи интерьеров, новинки рынка и советы профессионалов.
https://zbet.london
Oh my goodness! Awesome article dude! Many thanks, However I am encountering difficulties with your RSS. I don’t understand why I am unable to join it. Is there anybody getting the same RSS issues? Anybody who knows the answer will you kindly respond? Thanks!
Sweet web site , super style and design , rattling clean and utilize genial .
This is the right blog for anybody who hopes to find out about this topic. You realize so much its almost hard to argue with you (not that I personally would want to…HaHa). You certainly put a fresh spin on a topic which has been written about for years. Excellent stuff, just wonderful.
This website definitely has all the information I wanted concerning this subject and didn’t know who to ask.
Spot on with this write-up, I actually think this web site needs far more attention. I’ll probably be back again to see more, thanks for the information!
May I simply just say what a comfort to find someone that genuinely knows what they’re discussing on the web. You definitely realize how to bring a problem to light and make it important. More and more people ought to check this out and understand this side of the story. I was surprised that you’re not more popular since you certainly have the gift.
Saved as a favorite, I really like your web site.
Everything is very open with a clear explanation of the issues. It was really informative. Your site is very helpful. Many thanks for sharing.
Very great post. I just stumbled upon your
weblog and wanted to mention that I have truly loved browsing your blog posts.
In any case I will be subscribing to your feed and I hope you write again very soon!
смотреть фильмы бесплатно фантастика новинки кино онлайн в 4К
лучшие фильмы онлайн триллеры фильмы 2000 смотреть онлайн
новинки кино онлайн триллеры фильмы 2024 смотреть онлайн ужасы
фильмы онлайн HD с субтитрами новинки фильмы 2024 смотреть онлайн
дубай аренда яхты https://arenda-yahty-dubai.ru
Download music https://progworld.net in high quality without sound loss. Convenient search, wide choice of genres and artists, fast downloads.
You’ve made some good points there. I checked on the net to find out more about the issue and found most people will go along with your views on this website.
аренда яхты в оаэ аренда супер яхты в дубае
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
HEN88 là cổng game bài đổi thưởng hàng đầu tại Việt Nam, nổi bật với sự đa dạng trong các thể loại trò chơi. Từ slot game, xì dách, đến poker, mỗi game đều mang lại trải nghiệm độc đáo với đồ họa sắc nét và âm thanh sống động
Download music https://progworld.net for free and without registration. Huge database of tracks of all genres in high quality. Convenient search and fast download.
Смотрите аниме онлайн https://reanime.net на русском! Огромная коллекция сериалов и фильмов в хорошем качестве. Все популярные аниме с русской озвучкой и субтитрами. Удобно, бесплатно, в отличном качестве.
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
Доставка грузов из Китая https://cargotlk.ru под ключ. Организуем перевозки любых объемов: от документов до крупногабаритных грузов. Авиа, морская и автодоставка. Полное сопровождение, таможенное оформление, страхование.
I enjoy reading a post that can make men and women think. Also, thank you for permitting me to comment.
Great post! We will be linking to this particularly great article on our site. Keep up the great writing.
Profit pay by the corporation in a proportion of the profit as a dividend to shareholders.
bookmarked!!, I love your web site!
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
India, for example, has one of many worst records of electrical theft; energy corporations there are trying to chop their losses by implementing monitoring software for last-mile losses because the electricity strikes from the substation to the consumer.
I used to be able to find good advice from your content.
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
After I initially commented I seem to have clicked the -Notify me when new comments are added- checkbox and now each time a comment is added I receive 4 emails with the same comment. Perhaps there is an easy method you can remove me from that service? Kudos.
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
Telemarketing provides all the advantages to launch a winning marketing campaign-easy access, fast speed, the ability to ask for direct feedback, plus, it enables to provide the appropriate solutions to the clients’ problems.
Carey started a campaign to start out a kids’s museum in Indianapolis and enlisted the help of other native civic leaders and the Progressive Instructor’s Association.
After exploring a handful of the articles on your website, I honestly like your way of writing a blog. I book-marked it to my bookmark webpage list and will be checking back soon. Please visit my website as well and tell me your opinion.
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
While some wedding ceremonies take place on the noon, some after sundown, or some on the night as effectively, however most of them happen through the day.
bookmarked!!, I love your website.
Everything is very open with a very clear description of the issues. It was definitely informative. Your website is extremely helpful. Thank you for sharing.
Momodoll クリスマスと新年のために実用的なダッチワイフを購入する5つの動機
As the narrative progresses, we witness a heated confrontation in which Hyeong-seok’s roommate gets concerned in a misunderstanding over money he accepted from Hyeong-seok’s mother.
lucky jet hack 1win скачать скачать lucky jet 1win
DocReviews https://docreviews.com.ua это платформа, где пациенты могут оставлять отзывы о врачах. Мы стремимся помочь людям найти лучшего врача для своих нужд, предоставляя им доступную и достоверную информацию.
I’m impressed, I have to admit. Rarely do I encounter a blog that’s equally educative and engaging, and let me tell you, you’ve hit the nail on the head. The problem is an issue that too few folks are speaking intelligently about. Now i’m very happy I stumbled across this during my search for something relating to this.
Интернет-магазин инструментов https://profimaster58.ru для работы по металлу — ваш эксперт в качественном оборудовании! В ассортименте: измерительный инструмент, резцы, сверла, фрезы, пилы и многое другое. Гарантия точности, надежности и выгодных цен.
These days, the rancid coffee odor may still linger, but in many places the printer aroma is waning.
Great web site you have got here.. It’s hard to find excellent writing like yours nowadays. I honestly appreciate individuals like you! Take care!!
Thank for share! Play at https://kccommand.com to win
Capital stars also provides its services in providing free MCX tips, NCDX tips, Intraday tips and free trial MCX tips as well as Jackpot calls.
Good day! I could have sworn I’ve visited this website before but after going through a few of the posts I realized it’s new to me. Nonetheless, I’m definitely delighted I found it and I’ll be book-marking it and checking back regularly.
Смотрите аниме онлайн https://studiobanda.net бесплатно и без рекламы. Удобный каталог с популярными тайтлами, новинками и свежими сериями. Высокое качество видео и быстрый плеер обеспечат комфортный просмотр. Подборки по жанрам, рекомендации и регулярные обновления сделают ваш опыт максимально приятным.
лучшие школы фигурного катания записаться в секцию по фигурному катанию
And Glasner’s ploy worked a deal with as his staff won six of their final seven matches.
You’re so awesome! I don’t believe I’ve truly read a single thing like that before. So wonderful to find another person with unique thoughts on this subject. Really.. thank you for starting this up. This web site is something that’s needed on the internet, someone with some originality.
шурыгина новый слив шурыгина говорит
Официальная страница Дианы Шурыгиной https://x.com/DianaShyriginas свежие новости, уникальные фото и видео, личные откровения и новые проекты. Погружайтесь в мир Дианы, узнавайте её историю и вдохновение. Будьте в центре её жизни и не пропустите ни одного яркого момента!
Excellent post. I will be facing some of these issues as well..
Hi there! This article couldn’t be written any better! Looking through this article reminds me of my previous roommate! He constantly kept preaching about this. I am going to forward this information to him. Fairly certain he’s going to have a great read. I appreciate you for sharing!
Предприниматель и инвестор Святослав Гусев https://pinterest.com/gusevlive/ специализирующийся на IT, блокчейн-технологиях и венчурном инвестировании. Активно делится аналитикой рынка, инсайдами и новостями, которые помогут заработать каждому!
Sunwin chính thức cập nhật thêm domain chính hãng sunwin20a.com. Sunwin tặng code tân thủ 199k trong T1/2025 mừng sự kiện ra mắt domain mới tại sunwin20a.com, cổng game bài ma cao số 1 Châu Á. Khám phá kho game khổng lồ: Tài xỉu, bắn cá, slot game… Nạp rút siêu tốc, bảo mật tuyệt đối.
Địa chỉ: 15 Đường số 16, Tân Phú, Quận 7, Hồ Chí Minh, VN
Post Code: 756335
SĐT: +842816881699
Hashtag: sunwin, sun_win, tài_xỉu_sunwin, tải_sunwin, tải_sun_win, link_tải_sunwin, tải_game_sunwin, #sunwin #sun_win #tài_xỉu_sunwin #tải_sunwin #tải_sun_win #link_tải_sunwin #tải_game_sunwin
Website sunwin : https://sunwin20a.com/
I enjoy reading a post that can make people think. Also, thank you for allowing for me to comment.
I absolutely love your blog.. Pleasant colors & theme. Did you develop this web site yourself? Please reply back as I’m attempting to create my own blog and would love to learn where you got this from or what the theme is named. Appreciate it!
Thank you for this specific facts I was basically seeking all Msn in order to find it!
This website was… how do I say it? Relevant!! Finally I have found something that helped me. Appreciate it.
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
фильмы онлайн HD ужасы фильмы 2004 смотреть онлайн
смотреть фильмы бесплатно триллеры смотреть фильмы бесплатно в Украине
“Thank you, I have just been searching for info about this subject for a long time and yours is the best I have found out so far. However, what about the conclusion? Are you certain concerning the supply?”
смотреть фильмы бесплатно в СНГ фильмы 2024 смотреть онлайн фантастика
дивитися фільм безкоштовно в США фільми онлайн безкоштовно в Європі
This website was… how do you say it? Relevant!! Finally I’ve found something which helped me. Thanks a lot!
One other important issue is that if you are an elderly person, travel insurance with regard to pensioners is something you must really consider. The more mature you are, the more at risk you’re for allowing something undesirable happen to you while abroad. If you are certainly not covered by a few comprehensive insurance policy, you could have quite a few serious issues. Thanks for giving your ideas on this website.
I couldn’t refrain from commenting. Very well written!
Top post Genachowski’s less than artful weaving of net neutrality and consumer privacy | Law and Politics of Broadband you’ve surely influenced all of us FYI have you read Middle East amazing headlines! Enjoy your day ! Flash Website Design
The biggest issue is the dialogue, it is a little cheesy at times and doesn’t give the actors much to work with, but I wouldn’t say it’s every time they open their mouth just some lines in the movie are a little rough.
I couldn’t resist commenting. Very well written!
i will be needing some high power pressure washers to clean our home and our garden.,
I’d should check with you here. Which is not some thing I usually do! I love reading a post that may get people to feel. Also, many thanks for permitting me to comment!
Excellent web site you’ve got here.. It’s difficult to find excellent writing like yours these days. I seriously appreciate people like you! Take care!!
That expertise encompassed an up to date concern for security options.
At Cheap SEO Solutions https://cheap-seo-solutions.com we don’t believe in half-measures. We deliver comprehensive SEO solutions that cover all the bases, from keyword research and on-page optimization to link building and content creation. Our goal is to help businesses improve their search engine rankings, drive organic traffic, and increase conversions.
Ставки на спорт с Vavada https://selfiedumps.com это простота, надежность и высокие шансы на победу. Удобная платформа, разнообразие событий и быстрые выплаты делают Vavada идеальным выбором для любителей азарта. Зарегистрируйтесь сейчас и начните выигрывать вместе с нами!
Discover the power of AI with deepnudenow Fast image processing and accessible functionality allow you to create unique effects. Enjoy safe and anonymous use of the platform for entertainment.
I really love your site.. Excellent colors & theme. Did you make this amazing site yourself? Please reply back as I’m trying to create my own site and would love to know where you got this from or just what the theme is named. Appreciate it!
oui mais niet. Affirmatif parce que on rencontre d’autres sources qui se référent de semblables significations. Non parce que il n’est pas assez de répéter ce qu’on est en mesure de rencontrer avec certains site internet étrangers puis le transposer aussi naturellement:
great points altogether, you simply gained a emblem new reader. What could you suggest about your submit that you just made some days in the past? Any positive?
latest comics online comedy new releases online comic reader
best manga reading site with English subtitles read manga online fantasy
Wow, nice website you have here. I hope you will keep updating. Regards TJ
Way cool! Some very valid points! I appreciate you penning this write-up plus the rest of the site is very good.
Hey there just wanted to give you a quick heads up. The words in your post seem to be
running off the screen in Safari. I’m not sure if this is a format
issue or something to do with internet browser compatibility but I figured
I’d post to let you know. The style and design look great though!
Hope you get the problem solved soon. Cheers
Hi, I do believe this is an excellent web site. I stumbledupon it 😉 I may return once again since i have saved as a favorite it. Money and freedom is the greatest way to change, may you be rich and continue to guide other people.
Powell died in 1895, passing the leadership of the agency to John Bernard Hardman, the grandson of John Hardman Snr, who headed the corporate till 1903 and took the agency to the Exposition Universelle, Paris.
you have a excellent weblog here! do you wish to make some invite posts in my small blog?
This website truly has all of the information and facts I needed concerning this subject and didn’t know who to ask.
как потратить бонусы 1win 1win играть
Montenegro residence permit Realestate Montenegro
performing arts is my thing, i am very much interested to learn more on this art..
Nice Article
What platform and theme are you using if I may ask? Where can I buy them? .
mostbet для андроид mostbet casino bonus
mostbet uz apk skachat mostbet бонус
Everything is very open with a clear clarification of the challenges. It was really informative. Your site is extremely helpful. Thanks for sharing.
Spot on with this write-up, I truly feel this amazing site needs a lot more attention. I’ll probably be returning to read more, thanks for the advice.
ruine kaufen Montenegro immobilie
лучшие фильмы онлайн боевики фильмы 2024 смотреть онлайн
I additionally assume the first two questions in particular will seem simple to reply truthfully, however in actuality, they won’t be, because Threads is so large that the perceived costs of defederation will, for many or even most fedi admins, outweigh the benefits of booting a server that protects predators and unhealthy actors.
Extra extensive analysis still must be carried out earlier than any conclusions are made, although.
Spot on with this write-up, I actually think this web site needs much more attention. I’ll probably be returning to read more, thanks for the info.
etage haus Montenegro immobilien von privat kaufen
фильмы 2024 смотреть онлайн триллеры фильмы 2024 смотреть онлайн ужасы
This is a good tip especially to those fresh to the blogosphere. Simple but very precise info… Thank you for sharing this one. A must read post.
Spribe’s Aviator has established itself as a game-changing presence in the online
betting landscape. Breaking down the mechanics, what stands out is the player-friendly
payout structure – a figure that demands serious consideration.
Examining the global footprint, we’re seeing impressive user engagement with a
massive user community across multiple licensed providers.
What’s particularly noteworthy is the cross-border appeal,
maintaining solid popularity in diverse regions from Brazil to India.
Looking at the wagering angles, the automated withdrawal
option presents opportunities for maintaining betting control.
Interactive betting platform drives participation while
the in-game chat functionality adds another dimension to the wagering platform.
Prospective players considering entry should focus on starting with demo mode before placing actual bets.
The game’s simplicity doesn’t diminish the value of calculated betting.
Смотрите любимые дорамы https://dorama2025.ru онлайн в HD-качестве! Огромный выбор корейских, китайских, японских и тайваньских сериалов с профессиональной озвучкой и субтитрами.
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
Тһe Church of tһe Holy Apostles іn Thessaloniki wɑs in-built 1310-14.
Aⅼthouɡh some vandal systematically removed tһe gold tesserae ߋf tthe background
it cаn be seen that thе Pantokrator аnd tһe
prophets in tһe dome follow tһe normal Byzantine sample. Тhe dome (1142-42) and tһe japanese еnd of tһe church
(1143-1154) hhad Ƅeen decorated wіth typical Byzantine
mosaics і.e. Pantokrator, angels, scenes ffrom
tһe life of Christ. At Sant’Andrea in Catabarbara (468-483, destroyed іn 1686) Chtist appeared witrhin the centre, flanked oon either aspect Ьy tһree Apostles.
Ϝor example, a lott oof the character օf Halka’s οwn music is derived from ⲟne
easy, stunning melody ⅼine tһat she sings incessantly,
her own personal folk tune motive. Ꭺnd tһe enchantment оf tһe music wwnt
muⅽh deeper than tһe connection bеtween stage character аnd viewers member-Moniuszko һad giᴠen Babbie
ɑ hyperlink tօ heer heritage. Uрon reaching tһe Rainbow Bridge
᧐n the Canadian facet, Babbie insisted οn getting oout of tһe automotive
to ѡalk, heedless of tthe roaring Niagra Falls Ƅelow. І wοnder hοԝ Babbie ѕhould һave
felt ѡithin thе viewers оf tһat 1977, American manufacturing of Moniuszko’s Halka.
Alsso visit mʏ blog post: casino scripts
saglam qidalanma uzr? m?sl?h?tl?r imsak vaxt? bak?
You’re so awesome! I don’t suppose I’ve read through a single thing like this before. So nice to find another person with some genuine thoughts on this subject matter. Really.. thank you for starting this up. This website is one thing that is required on the internet, someone with a little originality.
манхва на русском языке ужасы лучшие манхвы читать 2014
постбек 1win скачать 1win с официального сайта
Thhe platform myst haνe an intuitive layout tһat permits travelers tߋ easily browse, compare, and guidce travel expertise companies.
Access tо More Data: Using casino api integration, travel businesses
ϲɑn get actual-tіme info from exterior sources tⲟgether with
hotels, automobile rental businesses, аnd airlines.
Ꭲhis object is often a structure tһɑt accommodates аll the data required by
the stanndard Ӏ/O libbrary tо manage the stream:
thе file descriptor սsed foг precise I/O, a
pointer tο a buffer for the stream, the dimensions of
the buffer, a rely оf thhe number оf characters currently in tһe buffer, ɑn error flag and the lіke.
Wһile not crucial, you miցht wish tto perform ϳust a few take а
lo᧐k ɑt transactions in dwll mode with real fee іnformation to ensure eveгy part is ѡorking ɑs anticipated.
Dսгing the India-Zimbabwe Joint TraԀе Commitee meeting іn New Delhi on 13 Ꮇay
2024, iit wass decided to loоk into signing a Memorandum of Understanding (MoU) on regulatory cooperation iin digijtal transformation solutions
ɑnd fɑst fee programs.
спортивные стероиды анаболики стероиды купить
Yet another thing is that while searching for a good on the internet electronics shop, look for online stores that are continually updated, trying to keep up-to-date with the most recent products, the very best deals, in addition to helpful information on products and services. This will make sure that you are doing business with a shop that really stays ahead of the competition and offers you things to make intelligent, well-informed electronics expenditures. Thanks for the significant tips I have really learned through your blog.
bank account in montenegro Montenegro residency
teleprompter on pc download teleprompter online
Wonderful write-up. I completely agree with your points.
Keep up the good work
Excellent content… This is very insightful. Will share this with others
Greetings, There’s no doubt that your website may be having internet browser compatibility issues. When I take a look at your website in Safari, it looks fine however, if opening in I.E., it has some overlapping issues. I just wanted to provide you with a quick heads up! Besides that, fantastic blog!
Останні новини Черкас https://18000.ck.ua та Черкаської області. Важливі новини про політику, бізнес, спорт, корупцію у владі на сайті 18000 ck.ua.
Great article! You’ve made some excellent observations.
Keep up the good work
Wonderful write-up! I completely agree with your points. Will share this with others
онлайн ридер манхвы исекай лучший сайт для чтения манхвы триллер
Montenegro Kotor immobilie Montenegro
HEN88 là cổng game bài đổi thưởng hàng đầu tại Việt Nam, nổi bật với sự đa dạng trong các thể loại trò chơi. Từ slot game, xì dách, đến poker, mỗi game đều mang lại trải nghiệm độc đáo với đồ họa sắc nét và âm thanh sống động
Nevertheless, In response to the present output and consumption, in the future ten years, cement business can be stable.
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
HUVIP88 – Cổng game đổi thưởng uy tín năm 2025 với hệ thống trò chơi phong phú từ game bài truyền thống đến các trò chơi mới lạ như Đua ngựa, Nổ hũ, Bắn cá, Rồng hổ, và Slot Games. Người chơi có thể trải nghiệm cảm giác hồi hộp với tài xỉu, xóc đĩa, bầu cua cùng nhiều tính năng độc đáo.
Hi there, I believe your website could possibly be having web browser compatibility problems. Whenever I take a look at your site in Safari, it looks fine however, when opening in IE, it has some overlapping issues. I simply wanted to provide you with a quick heads up! Other than that, wonderful blog!
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
XO88 là nhà cái đẳng cấp từ Anh Quốc, cung cấp đa dạng trò chơi cá cược online như bóng đá, casino trực tuyến, xóc đĩa, tài xỉu và nổ hũ. Tham gia ngay để trải nghiệm!
Nhà cái HDBET cung cấp các trò chơi cá cược trực tuyến chất lượng, từ thể thao đến casino, với bảo mật và hỗ trợ khách hàng chuyên nghiệp. Đăng ký ngay để tham gia cá cược !
Great article! You’ve made some excellent observations.
Will share this with others
Truy cập https://xo88.is để đăng ký tài khoản tại Nhà cái XO88 .
BOM86 là cổng game đổi thưởng đẳng cấp nhất hiện nay. Tại đây mọi người sẽ được trải nghiệm các game cá cược hấp dẫn như casino online , game bài và bắn cá.
Allen, John (28 February 2011).
Although the sport requires cautious evaluation, it also demands intuition to recognize patterns and spot opportunities.
strand becici Montenegro immobilien
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
I implore you to at all times read the experience of those e-newsletter writers closely as you will see that hardly any of them have any experience buying and selling capital, let alone a constant worthwhile track document.
It’s nearly impossible to find well-informed people on this topic, however, you seem like you know what you’re talking about! Thanks
скачать манхву бесплатно в черно-белом манхва на русском языке фэнтези
hotel Montenegro bar immobilien in Montenegro
Its like you learn my thoughts! You appear to grasp a lot about this, such as you wrote the book in it or something. I believe that you can do with a few percent to force the message house a little bit, but other than that, this is magnificent blog. A fantastic read. I will definitely be back.
That is a very good tip especially to those new to the blogosphere. Simple but very accurate information… Appreciate your sharing this one. A must read article.
запись по детекции движения программа для видеонаблюдения
This is a very good tip especially to those fresh to the blogosphere. Simple but very accurate info… Thank you for sharing this one. A must read article!
Ищете качественные стероиды для мужчин? У нас вы найдете широкий выбор сертифицированной продукции для набора массы, сушки и улучшения спортивных результатов. Только проверенные бренды, доступные цены и быстрая доставка. Ваше здоровье и успех в спорте – наш приоритет! Заказывайте прямо сейчас!”
новинки бесплатно читать манхву онлайн манхва на русском языке сёнэн
Wonderful write-up. This is very insightful. Will share this with others
дивитися кіно онлайн трилери кращі фільми онлайн в Канаді
дивитися фільм безкоштовно в Україні кращі фільми 2023 онлайн
кращі фільми 2019 онлайн фільми 2024 дивитися онлайн комедії
Truy cập https://iwin68.now để đăng ký tài khoản tại iwin 68.
88Vv là nhà cái trực tuyến đáng tin cậy, không chỉ nhờ vào sự phong phú của các sản phẩm giải trí và dịch vụ chất lượng cao mà còn do uy tín vững chắc.
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
список мфо онлайн на карту https://mfo-all.ru
buy thc chocolate in prague marijuana for sale in prague.
диана шурыгина слив видео https://shuriginadiana.ru
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
I like it when people get together and share thoughts. Great site, stick with it.
фильмы 2000 смотреть онлайн фильмы онлайн HD аниме
фильмы 2024 смотреть онлайн на телефоне смотреть фильмы онлайн комедии
Interesting post! I completely agree with your points.
Will share this with others
Pretty! This has been an extremely wonderful post. Many thanks for supplying this information.
Строительный портал https://bastet.com.ua ваш путеводитель в мире стройки! Подборка лучших материалов, контакты мастеров, проекты и лайфхаки. Создавайте уют и красоту с нашим сервисом!
No. Securities Act of 1933 Release No.
What reasons make child education important?
Нужны деньги срочно быстроденьги – ваш быстрый выход! Подайте заявку из любого места, получите деньги в течение нескольких минут. Удобно, прозрачно, без скрытых комиссий.
Финансовые трудности? Решите их за минуты займ на карту быстро деньги с моментальным переводом на карту. Оформление онлайн, простые условия и никакого лишнего стресса. Ваш надежный финансовый помощник!
I like it when people get together and share views. Great website, continue the good work!
Trong thế giới cá cược ngày nay, có không ít cái tên đình đám, nhưng không ít người vẫn trung thành với một địa chỉ duy nhất đó là J88com.im.
GK88 – Nhà cái GK88 – GK88 Casino nổi tiếng khắp thị trường giải trí với tư cách là một địa điểm cung cấp dịch vụ cá cược trực tuyến tốt nhất hiện nay.
Строительный портал https://bms-soft.com.ua для тех, кто строит и ремонтирует! Узнайте о трендах, найдите мастеров, подберите материалы и получите ценные рекомендации.
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
Right here is the perfect webpage for anybody who would like to understand this topic. You understand a whole lot its almost tough to argue with you (not that I really would want to…HaHa). You definitely put a brand new spin on a subject which has been discussed for many years. Excellent stuff, just great.
Откройте для себя лучшие сервера линейдж 2! Интересные рейты, уникальные механики, активная экономика и дружное комьюнити. Сражайтесь с боссами, участвуйте в массовых баталиях и развивайте персонажа. Присоединяйтесь к нам и наслаждайтесь игрой без лагов и с заботой об игроках!
Starting a business can be overwhelming, but with the right resource, you can simplify your launch. This comprehensive guide provides advice on how to establish a successful venture and overcome common obstacles. Check out this link for further insights and to explore more about starting.a business.
Biography of Spanish footballer Pedri https://pedri-bd.com statistics at Barcelona, ??games with teammate Gavi, inclusion in the national team for Euro, meme with Cristiano Ronaldo.
Biography of Argentine footballer Paulo Dybala https://paulo-dybala-bd.com personal life, tattoos on the body, wedding with his wife Oriana Sabatini.
This is a topic that’s near to my heart… Take care! Where can I find the contact details for questions?
Your one-stop resource dota-2-esports.com for the latest news reviews, and interviews from the world of professional Dota 2. Stay on top of all the major events and trends in esports!
This is highly enlightening. I truly enjoyed going through it. The content is very arranged and straightforward to understand.
Adored the details in this post. It’s highly comprehensive and filled with useful details. Excellent work!
Appreciated this entry. It’s highly detailed and filled with helpful details. Great job!
Robert Lewandowski https://robert-lewandowski-bd.com biography, photos, videos, goals, news, statistics. Robert Lewandowski on Wikipedia, Instagram, Twitter, Transfermarkt.
Execration is a legendary Dota 2 execration-dota2.com eSports team that conquers the heights of world eSports with its skill and tactics.
News portal dota news com your source of the most up-to-date information about the game and eSports events. News, tournaments, updates, analytics.
Xtreme Gaming: The Elite of Dota 2 xtreme-gaming-dota2.com. Unrivaled champions who have conquered the heights of eSports. Their fame thunders throughout the world.
Thus it was that a lot of England’s nobility grew up in properties that included inside their structure part the Gothic stays of an historical church or its associated monastic buildings.
As the stock market witnesses fluctuations regularly due to economic reasons, global trends, political issues, etc.
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
Everything is very open with a clear description of the challenges. It was truly informative. Your website is very useful. Thanks for sharing.
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
video surveillance solution ip camera recorder download
Натуральные молочные продукты https://gastrodachavselug2.ru свежесть и качество с заботой о вашем здоровье! Широкий выбор: молоко, творог, сметана, сыры. Только натуральные ингредиенты, без консервантов и добавок.
hemp delivery in prague buy weed in prague
cannabis for sale in prague thc weed in prague
buy hemp in prague thc weed in prague
buy thc chocolate in prague cannabis in prague
hashish shop in prague cannafood for sale in prague
420 day in prague https://prague-drugstore.site
weed store in prague hemp for sale in prague
buy hash in prague hashish in prague
kush shop in prague weed in prague
cannabis shop in prague hemp for sale in prague
a6tfgp
One month earlier Bogoljubov had misplaced the 1934 World Championship match, his second attempt to problem Alekhine.
Quest’anno, con M3, arriva un ulteriore miglioramento: il passaggio ai 3 nanometri ha permesso ad Apple di aumentare del 55% il numero di transistor nel die rispetto al primo modello, con un passaggio da 16 miliardi a 25 miliardi, e questo ha dato margine per inserire ad esempio il decoder AV1 e per rivedere interamente i core grafici, che alla fine sono gli elementi che occupano più spazio sul processore: l’intera zona superiore, si possono contare i core, è occupata dalla GPU. Guardando indietro a qualche anno prima, Anton studiava per l’ottenimento di un Master of Science in comunicazione, trasporti e infrastrutture, seguito da una laurea magistrale in economia industriale e gestione della catena di approvvigionamento presso l’Università di Linköping. Dopo essersi laureato, ha cominciato la sua carriera presso Axis con il nostro Operations Trainee Program, che gli ha consentito di mettere in pratica le sue conoscenze.
https://www.chordie.com/forum/profile.php?section=identity&id=2093285
I nostri ingegneri software e specialisti di blockchain sfruttano la potenza della blockchain per creare un ecosistema al servizio di aziende di vari settori e scale. Tali ecosistemi includono un algoritmo di consenso e libri mastri condivisi insieme a un’applicazione per i nodi e sono molto più vantaggiosi rispetto a quelli tradizionali grazie alla maggiore trasparenza, sicurezza e resistenza alle manipolazioni malevole. Può sembrare strano, ma gli antenati del mercato delle criptovalute – che oggi vale più di 2 trilioni di $ – risiedono in World of Warcraft, gioco MMORPG a pagamento, pubblicato nel 2004. If you want to stay ahead of your industry, now is the time to digitalize your organization. No matter which industry you belong to, Comstar USA is ready to take the challenge. Software Consultant Data Warehose (stage per tesi)
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
Wonderful write-up. You’ve made some excellent observations.
Will share this with others
XO88 là nhà cái đẳng cấp từ Anh Quốc, cung cấp đa dạng trò chơi cá cược online như bóng đá, casino trực tuyến, xóc đĩa, tài xỉu và nổ hũ. Tham gia ngay để trải nghiệm!
Great article… This is very insightful. Will share this with others
Just wanted to share my thoughts with Adam Graham’s The Growth Mindset weekly update. If you’re not familiar, Adam J. Graham is the creator behind his startup, and his email has turned into one of my most useful tools for keeping up in technology, business, and entrepreneurship. I’ve been following it for a long time now, and it’s definitely one of the best resources I’ve found for both personal and professional development. Check out the full discussion on Reddit here.
Interesting post! I completely agree with your points. Keep up
the good work
Great article. Your perspective is refreshing. Will share this with others
https://ocher-cat-dd3cmm.mystrikingly.com/blog/f10e254a23b
https://xn--w8-hs1izvv81cmb366re3s.mystrikingly.com/blog/3b2b688d709
https://witty-apple-dd3cm1.mystrikingly.com/blog/fc35efb2e09
https://viastoer.blogspot.com/2024/07/blog-post_21.html
https://medium.com/@nsw5288/%EB%B9%84%EC%95%84%EA%B7%B8%EB%9D%BC%EC%99%80-%ED%95%A8%EA%BB%98%EB%9D%BC%EB%A9%B4-%EC%A3%BC%EC%9D%98%ED%95%B4%EC%95%BC-%ED%95%A0-%EC%95%BD%EB%AC%BC%EB%93%A4-a3861b835e15
Wonderful write-up. This is very insightful.
Thanks for sharing
https://inky-owl-dd3cmv.mystrikingly.com/blog/481bc4e3083
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
https://candid-lion-dd3cm3.mystrikingly.com/blog/5037f72f44c
https://gray-begonia-dbgzhf.mystrikingly.com/blog/vs
https://gajweor.pixnet.net/blog/post/162874255
https://naveridbuy.blogspot.com/2024/11/blog-post_50.html
sex nhật hiếp dâm trẻ em ấu dâm buôn bán vũ khí ma túy bán súng sextoy chơi đĩ sex bạo lực sex học đường tội phạm tình dục chơi les đĩ đực người mẫu bán dâm
Great article! This is very insightful. Will share
this with others
https://viastoer.blogspot.com/2024/09/blog-post_61.html
https://naveridbuy.blogspot.com/2024/11/blog-post_50.html
https://writeablog.net/imt11px743
deep web drug url best darknet markets deep web drug links
https://naveridbuy.blogspot.com/2024/12/blog-post_52.html
https://candid-lion-dd3cm3.mystrikingly.com/blog/9cd12105d44
https://medium.com/@carlfrancoh38793/%EA%B5%AC%EA%B8%80-%EC%95%84%EC%9D%B4%EB%94%94-%EA%B5%AC%EB%A7%A4-%EC%9D%B4%EC%A0%90%EA%B3%BC-%EB%8B%A8%EC%A0%90%EC%9D%80-%EB%AC%B4%EC%97%87%EC%9D%B8%EA%B0%80%EC%9A%94-4dccd7ee3fc1
Good post. I learn something new and challenging on websites I stumbleupon everyday. It’s always interesting to read through content from other writers and practice something from their web sites.
Medications play a key role in managing bipolar disorder.
I used to be able to find good advice from your blog posts.
Great article! This is very insightful. Looking forward to more
Great article… This is very insightful. Will share
this with others
https://writeablog.net/mzlw3kmb0y
https://naveridbuy.blogspot.com/2024/12/blog-post_26.html
https://xn--lw-o02ik82aiqcqsko8mfg5a1sb.mystrikingly.com/blog/b8da7672f66
https://vermilion-elephant-dd3cm3.mystrikingly.com/blog/cda35b98376
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
Wonderful write-up! Your perspective is refreshing.
Will share this with others
Great article… This is very insightful. Keep up the good
work
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
https://candid-lion-dd3cm3.mystrikingly.com/blog/53469580831
https://candid-lion-dd3cm3.mystrikingly.com/blog/6f5ea7ec9c8
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
https://medium.com/@nsw5288/%EC%B2%98%EB%B0%A9%EC%A0%84-%EC%97%86%EC%9D%B4-%EB%B9%84%EC%95%84%EA%B7%B8%EB%9D%BC-%EA%B5%AC%EB%A7%A4-%EA%B0%80%EB%8A%A5%ED%95%9C%EA%B0%80-0b4829c0a939
Hey, you used to write great, but the last several posts have been kinda boring? I miss your great writings. Past few posts are just a bit out of track! come on!
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
https://naveridbuy.exblog.jp/37152040/
https://medium.com/@charlielevesque328/%EB%B9%84%EC%95%84%EA%B7%B8%EB%9D%BC-%EA%B5%AC%EB%A7%A4-%EC%9D%B4%EB%A0%87%EA%B2%8C-%ED%95%98%EB%A9%B4-%EC%95%88%EC%A0%84%ED%95%A9%EB%8B%88%EB%8B%A4-d371ae128dd1
how to access dark web darkmarket url darknet websites
https://telegra.ph/%EB%B9%84%EC%95%84%EA%B7%B8%EB%9D%BC-%EA%B5%AC%EB%A7%A4-%EC%8B%9C-%EC%95%8C%EC%95%84%EC%95%BC-%ED%95%A0-%EC%9C%A0%EC%9D%98%EC%82%AC%ED%95%AD-7%EA%B0%80%EC%A7%80-09-20
https://writeablog.net/6iekby1s5m
https://medium.com/@carlfrancoh38793/%EC%A4%91%EA%B3%A0-%EB%84%A4%EC%9D%B4%EB%B2%84-%EC%95%84%EC%9D%B4%EB%94%94%EB%A5%BC-%ED%9A%A8%EA%B3%BC%EC%A0%81%EC%9C%BC%EB%A1%9C-%ED%99%9C%EC%9A%A9%ED%95%98%EB%8A%94-%EB%B0%A9%EB%B2%95-a5bd35053073
https://candid-lion-dd3cm3.mystrikingly.com/blog/8c25ae9d7a9
https://naveridbuy.exblog.jp/37152138/
EE88 là một trong những nhà cái hàng đầu tại Việt Nam, nổi bật với giao diện tối tân và hệ thống bảo mật hiện đại, mang đến trải nghiệm cá cược an toàn và tin cậy cho người chơi. Tại EE88, bạn có thể tham gia đa dạng các trò chơi hấp dẫn như cá cược thể thao, casino trực tuyến, game bài, và xổ số với tỷ lệ cược cạnh tranh hàng đầu.
Website: https://ee88vie.com/chinh-sach-bao-mat/
Howdy! I could have sworn I’ve been to your blog before but after looking at a few of the articles I realized it’s new to me. Nonetheless, I’m certainly happy I stumbled upon it and I’ll be book-marking it and checking back often.
denemebonusuverensiteler25: deneme bonusu veren yeni siteler – denemebonusuverensiteler25
Does your site have a contact page? I’m having a tough time locating it but, I’d like to shoot you an email. I’ve got some ideas for your blog you might be interested in hearing. Either way, great website and I look forward to seeing it expand over time.
Портал о строительстве https://aziatransbud.com.ua статьи, видео, инструкции, каталоги материалов и инструментов. Советы для дома и бизнеса. Легко строить, удобно ремонтировать!
Всё для строительства и ремонта https://artpaint.com.ua на одном портале: советы экспертов, обзоры материалов, расчет сметы и готовые решения для вашего дома или бизнеса.
Портал для строительства https://6may.org и ремонта: полезные советы, современные материалы, проекты и идеи. Все, что нужно для воплощения ваших задумок – от фундамента до крыши.
Студия дизайна интерьера https://bconline.com.ua и архитектуры: создаем уникальные проекты для квартир, домов и коммерческих пространств. Эстетика, функциональность и индивидуальный подход – в каждом решении.
Все об озеленении и благоустройстве https://bathen.rv.ua Ландшафтный дизайн, проекты садов, террас и парков. Идеи для создания зеленых зон, подбор растений и профессиональные услуги для вашего участка.
https://writeablog.net/ep887shpzn
https://candid-lion-dd3cm3.mystrikingly.com/blog/8c25ae9d7a9
https://witty-apple-dd3cm1.mystrikingly.com/blog/5dbde675bb4
https://naveridbuy.exblog.jp/37091323/
https://naveridbuy.exblog.jp/35878157/
https://telegra.ph/%EB%B9%84%EC%95%84%EA%B7%B8%EB%9D%BC%EC%9D%98-%EB%8C%80%EC%95%88%EB%93%A4-%EC%84%A0%ED%83%9D%EC%A7%80%EB%8A%94-09-12
Разработка интернет магазина https://magikfox.ru/services/sozdanie-saytov/internet-magazin-na-bitriks/ на Битрикс под ключ в диджитал агентстве MagicFox. Демократичные цены на создание сайта магазина на Bitrix. Интеграция с 1С, службами доставки, системами оплаты. Полная настройка функционала. Работаем по всей России.
гормон роста купить стероид курс стероидов
пневмозаглушка оболочки резинокордные
Ваш путеводитель в мире строительства https://dcsms.uzhgorod.ua идеи, планы, пошаговые инструкции и лучшие материалы. Узнайте, как построить дом мечты или обновить интерьер.
Профессиональный портал для строительства https://blogcamp.com.ua проекты, материалы, расчеты, советы и вдохновение. Все, чтобы ваш ремонт или стройка были успешными.
https://naveridbuy.exblog.jp/37091209/
https://naveridbuy.blogspot.com/2024/12/blog-post_3.html
https://medium.com/@1kelly76/%EB%B0%9C%EA%B8%B0%EB%B6%80%EC%A0%84%EA%B3%BC-%EC%A1%B0%EB%A3%A8-%EC%9B%90%EC%9D%B8%EA%B3%BC-%ED%95%B4%EA%B2%B0%EC%B1%85-%EC%99%84%EB%B2%BD-%EA%B0%80%EC%9D%B4%EB%93%9C-f2bce7dc7851
https://able-pear-dbgzhh.mystrikingly.com/blog/84c7ecac94a
https://hallbook.com.br/blogs/295244/%EB%B0%9C%EA%B8%B0%EB%B6%80%EC%A0%84%EA%B3%BC-%EC%A1%B0%EB%A3%A8%EC%9D%98-%EC%8B%AC%EB%A6%AC%EC%A0%81-%EC%9A%94%EC%9D%B8%EA%B3%BC-%EA%B7%B9%EB%B3%B5-%EC%A0%84%EB%9E%B5
Делайте ремонт https://esi.com.ua и стройте легко! Лучшие советы мастеров, подбор инструментов, инструкции и сметы. Мы поможем справиться с любой задачей.
Хотите построить дом https://donbass.org.ua или сделать ремонт? Здесь вы найдете всё: инструкции, идеи, современные технологии и проверенные решения. Портал для тех, кто строит.
Все для строителей и мастеров https://dki.org.ua актуальные технологии, практические советы, строительные материалы и проекты. Простые решения для сложных задач!
Создайте дом своей мечты https://intellectronics.com.ua На нашем портале вы найдете идеи, инструкции и новейшие технологии для ремонта и строительства.
Станьте мастером https://fmsu.org.ua своего дела! Портал для тех, кто хочет строить и ремонтировать качественно и выгодно.
https://naveridbuy.exblog.jp/35859445/
https://medium.com/@nsw5288/%EB%B9%84%EC%95%84%EA%B7%B8%EB%9D%BC-%EA%B5%AC%EB%A7%A4-%EB%B0%A9%EB%B2%95%EA%B3%BC-%ED%9A%A8%EA%B3%BC%EC%A0%81%EC%9D%B8-%EC%82%AC%EC%9A%A9%EB%B2%95-71efc491ca1b
https://ko.anotepad.com/note/read/5fkx4w7q
https://medium.com/@carlfrancoh38793/%EB%84%A4%EC%9D%B4%EB%B2%84-%EC%95%84%EC%9D%B4%EB%94%94%EC%99%80-%EA%B4%80%EB%A0%A8%EB%90%9C-%EC%B5%9C%EC%8B%A0-%EB%B3%B4%EC%95%88-%EC%9D%B4%EC%8A%88-4569786b88d3
https://naveridbuy.exblog.jp/37091209/
https://witty-apple-dd3cm1.mystrikingly.com/blog/e592523ee2b
https://medium.com/@1kelly76/%EB%B9%84%EC%95%84%EA%B7%B8%EB%9D%BC-%EA%B5%AC%EB%A7%A4-%EC%8B%9C-%EC%B2%98%EB%B0%A9%EC%A0%84%EC%9D%B4-%ED%95%84%EC%9A%94%ED%95%9C%EA%B0%80-6dd230d8e4f3
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
gГјvenilir casino http://sweetbonanza25.com/# sweet bonanza slot
gГјvenilir siteler
Архитектура и дизайн интерьера https://it-cifra.com.ua под ключ: современные решения, индивидуальный подход и гармония стиля и функциональности. Создаем пространство вашей мечты!
Ландшафтный дизайн https://kinoranok.org.ua и благоустройство для дома, офиса или парка. Профессиональные советы, подбор растений и реализация уникальных зеленых проектов.
Найдите все для ремонта https://keravin.com.ua и строительства! Уникальные идеи, пошаговые инструкции и рекомендации специалистов на одном портале.
Стройте с комфортом https://mr.org.ua полезные советы, новейшие технологии, пошаговые инструкции и проекты – всё для вашего удобства.
Мы помогаем строить https://juglans.com.ua лучше! Советы, проекты, новейшие материалы и технологии для вашего ремонта или строительства.
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
It’s a shame you don’t have a donate button! I’d without a doubt donate to this excellent blog! I suppose for now i’ll settle for bookmarking and adding your RSS feed to my Google account. I look forward to new updates and will share this blog with my Facebook group. Talk soon!
Ваш путеводитель в мире строительства https://mtbo.org.ua полезные рекомендации, готовые проекты и современные решения для любых задач.
Решили строить или делать ремонт https://msc.com.ua Мы подскажем, как выбрать лучшие материалы, спланировать бюджет и воплотить все задумки.
Все секреты https://mramor.net.ua строительства в одном месте! Советы экспертов, подбор материалов и готовые проекты для вдохновения.
Строительство без лишних вопросов https://okna-k.com.ua наш портал – кладезь информации о современных материалах, технологиях и лучших решениях для дома, дачи или офиса.
Всё для успешного строительства https://newboard-store.com.ua и ремонта на одном портале! Мы собрали актуальную информацию, идеи и инструкции для вашего удобства. Заходите и стройте с нами!
deep web links deep web drug markets darknet drug store
Информация о стройке https://purr.org.ua без лишних сложностей! Наш портал поможет выбрать материалы, узнать о технологиях и сделать ваш проект лучше.
accountant montenegro starting a business in Montenegro
Ваш путеводитель в строительстве https://quickstudio.com.ua Ищите материалы, технологии или советы – всё это есть на нашем портале. Стройте с комфортом!
1win bonus code 1win token
1win login uganda 1win register login
Официальный сайт https://luckyjetonewins.ru , где вы найдете актуальное зеркало и промоды на Лаки Джет.
darknet market lists deep web drug links dark web sites
Aw, this was a really good post. Taking the time and actual effort to generate a really good article… but what can I say… I hesitate a whole lot and don’t manage to get nearly anything done.
Всё, что нужно знать о металлах https://metalprotection.com.ua от их свойств до применения в различных отраслях. Обзоры, советы, новости и информация о производителях для вашего удобства.
Всё для вашего ремонта https://reklama-region.com и строительства в одном месте! Практичные советы, современные решения и актуальная информация для успешного проекта.
Вавада предлагает ставки на спорт Вавада на любой вкус! Здесь вы найдете ставки на футбол, теннис, баскетбол, киберспорт и многое другое. Широкий выбор событий, удобный интерфейс и выгодные коэффициенты делают платформу идеальной как для новичков, так и для опытных игроков. Начните свой путь в ставках уже сегодня!
Хотите построить дом https://samozahist.org.ua или сделать ремонт? На нашем портале вы найдёте лучшие решения и вдохновение для вашего проекта.
Ищете проверенные строительные советы https://rus3edin.org.ua Наш портал поможет выбрать материалы, спланировать проект и сделать всё на высшем уровне.
how to access dark web darknet market list blackweb
Строительный портал https://sinergibumn.com для тех, кто хочет знать больше о строительстве. Актуальные идеи, проверенные технологии и вдохновение для любого проекта.
Всё о дизайне интерьера https://sculptureproject.org.ua в одном месте! Узнайте, как создать уютное, стильное и функциональное пространство, которое будет радовать каждый день.
программа производственного контроля медицина https://ppk-213.ru
Экспертный строительный портал https://smallbusiness.dp.ua для вашего проекта! Советы, новинки и инструкции для тех, кто хочет сделать всё идеально.
Хотите стильный интерьер https://sitetime.kiev.ua Наш портал предлагает уникальные идеи, профессиональные рекомендации и примеры лучших дизайн-проектов.
그래서 아무런 의심 없이 아무 데나 닥치는 대로 이용할 경우, 막대한 손해를 보실 수 있습니다.
저희가 추천하는 업체를 이용하시면 여러분이 직접 안전한 카지노사이트를 찾아 헤매실 필요가 없습니다.
You need to take part in a contest for one of the finest sites on the web. I am going to highly recommend this blog!
darkmarket list deep web drug links black internet
8v1skw
Строительный портал https://sushico.com.ua для профессионалов и новичков: от выбора материалов до готовых проектов. Легко найти подрядчиков, изучить современные технологии и воплотить идеи в жизнь!
Планируете стройку https://texha.com.ua или ремонт? У нас вы найдёте проверенных специалистов, инструкции, материалы и проекты на любой вкус. Всё для комфортного строительства!
Преобразите ваш дом https://vineyardartdecor.com вместе с нами! На портале вы найдёте свежие идеи, советы по планировке и материалы для создания идеального интерьера.
Всё о строительстве https://valkbolos.com и ремонте на одном портале! Гид по материалам, обзор инструментов, советы по дизайну и подбор подрядчиков. Создавайте дом своей мечты!
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
GK88 – Nhà cái GK88 – GK88 Casino nổi tiếng khắp thị trường giải trí với tư cách là một địa điểm cung cấp dịch vụ cá cược trực tuyến tốt nhất hiện nay.
Trong thế giới cá cược ngày nay, có không ít cái tên đình đám, nhưng không ít người vẫn trung thành với một địa chỉ duy nhất đó là J88com.im.
darknet drugs darknet links darknet markets
Ремонт и строительство https://sota-servis.com.ua легко! Здесь вы найдёте инструкции, рекомендации, материалы и специалистов для успешного выполнения ваших задач.
Планируете ремонт или строительство https://vodocar.com.ua У нас всё, что нужно: от инструкций и советов до подрядчиков и обзоров материалов. Стройте с нами!
Лучшие советы по строительству https://stroysam.kyiv.ua и ремонту на одном сайте! Найдите вдохновение, изучите обзоры и воплотите свои идеи с профессиональной помощью.
Полный справочник по строительству https://stroy-portal.kyiv.ua и ремонту: советы, инструкции, дизайн-решения и помощь с выбором материалов и подрядчиков.
Ваш гид в мире строительства https://vitamax.dp.ua и ремонта! Обзоры, практические советы, дизайн-идеи и подбор профессионалов для реализации любых проектов.
TaskMy.ru – профессиональная помощь в решении задач любого уровня
TaskMy.ru – это надежный сервис, который предлагает качественную помощь в выполнении задач любых направлений: от технических расчётов и программирования до написания текстов и аналитики. Мы работаем быстро, эффективно и ориентированы на ваши требования.
Доверяя TaskMy.ru, вы получаете индивидуальный подход, точное соблюдение сроков и доступные цены. Оставьте свою задачу профессионалам – результат превзойдет ожидания!
ABC88 là sự lựa chọn mới cho những tay chơi mong muốn trải nghiệm cảm giác cá cược thực thụ. Hàng ngàn điều thú vị trong kho tàng game đang chờ đón bạn.
Excellent article. I’m dealing with many of these issues as well..
dark market darkmarket link darknet markets
Сделайте ремонт https://tfsm.com.ua мечты с нашим сайтом! Советы, инструкции, рейтинг специалистов и новинки строительного рынка для вашего удобства.
Простые решения для ремонта https://teplo.zt.ua и строительства! Идеи дизайна, рекомендации экспертов и проверенные материалы для вашего проекта.
Стройте и ремонтируйте https://suli-company.org.ua с лёгкостью! Полезные статьи, инструкции, советы по выбору материалов и подрядчиков ждут вас здесь.
Портал о ремонте и строительстве https://buildingtips.kyiv.ua с полезными статьями, рекомендациями по выбору материалов и подрядчиков.
Полный гид по строительству https://tsentralnyi.volyn.ua и ремонту: от планирования до отделки. Читайте, выбирайте и стройте с уверенностью и комфортом.
I do agree with all of the ideas you’ve presented in your post. They are very convincing and will definitely work. Still, the posts are too short for novices. Could you please extend them a bit from next time? Thanks for the post.
Полный гид по строительству https://tsentralnyi.volyn.ua и ремонту: от планирования до отделки. Читайте, выбирайте и стройте с уверенностью и комфортом.
gg drop https://seoul-massage.com
TaskMy.ru – профессиональная помощь в решении задач любого уровня
TaskMy.ru – это надежный сервис, который предлагает качественную помощь в выполнении задач любых направлений: от технических расчётов и программирования до написания текстов и аналитики. Мы работаем быстро, эффективно и ориентированы на ваши требования.
Доверяя TaskMy.ru, вы получаете индивидуальный подход, точное соблюдение сроков и доступные цены. Оставьте свою задачу профессионалам – результат превзойдет ожидания!
Приветствую на https://bs2best.markets! Мы предлагаем надежные и проверенные покупки в интернете. Ознакомьтесь с нашими статьями о безопасности и легальности. Ваши покупки — наш приоритет!
Tormac.org https://tormac.org – это специализированный торрент-трекер, предназначенный для пользователей Mac-компьютеров. Сайт предоставляет широкий выбор контента, ориентированного на операционные системы macOS и iOS.
Сделайте ремонт https://tfsm.com.ua мечты с нашим сайтом! Советы, инструкции, рейтинг специалистов и новинки строительного рынка для вашего удобства.
Sunwin là một thương hiệu game bài đổi thưởng hàng đầu tại Việt Nam, chuyên cung cấp các trò chơi đổi thưởng như game bài, tài xỉu, nổ hũ, bắn cá,… Link tải Sunwin chính hãng mới nhất: Sunwinct, Sunwin CT.
Website: https://sunwinct.com/
I like reading through a post that will make men and women think. Also, thanks for allowing me to comment.
mostbet skachat mostbet app download
mostbet зеркало mostbet uzb
lucky jet 1win real or fake сигналы 1win
сериалы 2024 смотреть онлайн
MLB Draft Betting https://bettingblog.website Your guide to the world of MLB draft betting. Expert predictions, top odds and detailed analysis will help you increase your chances of success. Bet and win with us!
Best Forex Trading Course https://blogforex.tech is your key to successful trading. Learn the secrets of professionals, study strategies and learn how to minimize risks. Master Forex easily and effectively!
Credit Union Mobile Home Loans https://blogcredit.tech are the perfect solution for buying or refinancing a mobile home. Affordable rates, easy application, and reliable support every step of the way. Take the first step toward your home with us!
Tennis betting https://yourmoneyblog.site best odds, predictions and analytics. Explore detailed match reviews, statistics and strategies to make successful bets. Use our tips and win!
Federal Gov Open Enrollment https://body-balance.online is your chance to upgrade or choose an insurance plan. Easy navigation, expert support, and a wide range of programs will help you make the right choice. Apply now!
Crypto Funk https://besttodaynew.com is a fresh look at cryptocurrencies. News, trends, guides and analytics for beginners and professionals. Find out how to get the most out of blockchain technology!
Howdy would you mind stating which blog platform you’re working with? I’m planning to start my own blog soon but I’m having a hard time choosing between BlogEngine/Wordpress/B2evolution and Drupal. The reason I ask is because your design seems different then most blogs and I’m looking for something completely unique. P.S Sorry for getting off-topic but I had to ask!
HELLO88 là gợi ý hàng đầu cho những anh em đang tìm kiếm địa điểm cá cược uy tín. Tại đây quy tụ rất nhiều trò chơi khủng, cùng cơ cấu phần thưởng cao ngút ngàn.
This page certainly has all the information I needed about this subject and didn’t know who to ask.
GO99 cung cấp vô số thể loại cá cược hấp dẫn, từ thử thách vận may đến tư duy logic chuẩn xác. Đăng ký để thư giãn và tìm kiếm cơ hội đổi đời ngay trong hôm nay.
Nohu63 đã trở thành một hiện tượng mới trong làng casino trực tuyến. Sau 10 năm hoạt động, đơn vị cá cược đã xây dựng được một cộng đồng người chơi đông đảo.
Nohu80 là thiên đường giải trí qua mạng chất lượng, nơi quy tụ những siêu phẩm cá cược đẳng cấp độc nhất vô nhị. Sân chơi là sự lựa chọn hoàn hảo cho các tín đồ
NOHU là trang web hàng đầu về tổng hợp cá cược game slot 3D trực tuyến hiện nay. Chúng tôi cung cấp nhiều loại dịch vụ và các chương trình khuyến mãi đa dạng.
Home Equity Loans https://funnydays1.com How They Work, What Are the Terms and Benefits? Get the full details on how to use your home’s value for financial purposes. Find out more today!
Auto loans from Community Credit Union https://sunnydays100.com are simple, affordable, and great value. Low interest rates and flexible repayment options make it easy to buy a new or used car.
Credit score requirements for FHA loans https://lifeofnews1.com minimum threshold and tips for improving. Find out how to increase your chances of getting a loan, as well as what affects approval. Detailed information for those who want to get a mortgage through FHA.
No Credit Check Loans in Abilene TX https://daynewday1.com is fast access to money without unnecessary checks. Convenient terms, simple application and instant approval. Get financial help when you need it!
программа производственного контроля пэк программа производственного контроля пэк
Biography of American basketball legend Michael Jordan https://michael-jordan-az.org personal life, participation in the Monaco Champions League match, film projects, marriage to Yvette Prieto, parenthood, net worth and collaboration with Michael Jackson. Latest updates in 2024.
Excellent article! We are linking to this great post on our website. Keep up the great writing.
Новогодние подарки https://giftbox-3.ru в жестяной упаковке оптом купить и печать коробки с логотипом в Хабаровске.
Try your luck at 365 taya, where excitement meets reliability! Hundreds of popular games, unique promotions and instant payouts await you.
Dive into the exciting gaming world of taya 365 login! Endless selection of games, fast withdrawals and fair play – everything for your pleasure.
Hashish shop in Prague buy-weed-prague.com
Cali weed for sale in Prague 420 movement in Prague
I want to to thank you for this great read!! I absolutely loved every little bit of it. I have you saved as a favorite to check out new stuff you post…
top manga One Piece free online online manga Demon Slayer free online
This site was… how do I say it? Relevant!! Finally I have found something that helped me. Thanks.
If you start a business, the initial deductions may supply tax refunds, and as the enterprise begins to earn money, the continuing deductions lower your taxable income.
The very next time I read a blog, Hopefully it does not disappoint me as much as this particular one. After all, Yes, it was my choice to read through, however I actually thought you would have something interesting to talk about. All I hear is a bunch of whining about something you could fix if you weren’t too busy seeking attention.
I like it whenever people come together and share views. Great site, continue the good work!
An impressive share! I have just forwarded this onto a co-worker who had been doing a little research on this. And he actually ordered me lunch due to the fact that I discovered it for him… lol. So let me reword this…. Thanks for the meal!! But yeah, thanks for spending the time to talk about this matter here on your web page.
taya 365 login taya 365 login
taya 365 casino login taya365 login
Everything is very open with a really clear explanation of the issues. It was definitely informative. Your site is very helpful. Thanks for sharing.
Nohu64 là ưu tiên hàng đầu của giới cược thủ trong suốt nhiều năm qua. Sân chơi vừa mang đến sản phẩm giải trí đỉnh cao vừa cung cấp dịch vụ cực kỳ chuyên nghiệp.
“Ищете качественный кирпич напрямую от производителя? https://Muravey61.ru – ваш надежный поставщик строительных материалов в регионе! Мы предлагаем кирпич высшего качества по доступным ценам прямо с завода. Доставка точно в срок, широкий ассортимент, и гарантированное качество – всё, что нужно для вашего строительства. Закажите у нас и убедитесь сами, что с нами строить легко!”
Pretty! This has been an incredibly wonderful post. Many thanks for providing this information.
Нужен ремонт техники чинпочин.рус все услуги для вашего дома в одном месте! Выбирайте мастеров для ремонта, уборки или сантехнических работ. Качественный сервис, прозрачные цены и удобство использования.
This excellent website certainly has all the info I wanted concerning this subject and didn’t know who to ask.
video surveillance software free vms software
A motivating discussion is worth comment. I believe that you should write more about this topic, it may not be a taboo subject but typically people do not speak about such subjects. To the next! All the best.
ip camera recorder CCTV Video Tools
The banks feared the declaration of war would trigger a run on the banks, so the Chancellor David Lloyd George extended the August bank holiday for three days to allow time for the passing of the Currency and Bank Notes Act 1914, by which Britain left the gold standard.
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
Hello! I just want to offer you a big thumbs up for your great info you’ve got here on this post. I will be coming back to your web site for more soon.
It’s not as uncommon as you may think, with many YouTube movies out there do you have to want to give it a attempt your self!
jrizxd
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
Cổng game HUVIP88 nơi mang lại thế giới giải trí đẳng cấp với các trò chơi đổi thưởng hấp dẫn nhất năm 2025. Tại đây, người chơi có thể thử sức với các game bắn cá, đua ngựa, tài xỉu và các game bài nổi tiếng. HUVIP88 luôn cam kết bảo mật tuyệt đối, hỗ trợ người chơi 24/7 cùng với hàng loạt phần thưởng khủng cho cả thành viên mới và cũ, tạo nên một sân chơi uy tín và chuyên nghiệp.Thông tin chi tiết: Website: https://huvip88.net
XO88 Win – Là nhà cái uy tín hàng đầu với nhiều trò chơi cá cược đa dạng, từ casino trực tuyến đến các trò như xóc đĩa, tài xỉu và bắn cá. Tham gia ngay để trải nghiệm cảm giác hồi hộp và nhận ưu đãi khuyến mãi hấp dẫn!Thông tin chi tiết:Website: https://xo88.is/
Nhà cái HDBET cung cấp các trò chơi cá cược trực tuyến chất lượng, từ thể thao đến casino, với bảo mật và hỗ trợ khách hàng chuyên nghiệp. Truy cập ngay https://hdbet.app/ để đăng ký ngay để tham gia cá cược !
Link vào MAX88 mới nhất – Đẳng cấp cá cược đến từ nhà cái Anh Quốc. Đăng ký ngay để nhận vô vàn ưu đãi cho người mới.Website: https://max88k.com
Cổng game BOM86 là game bài đổi thưởng đẳng cấp nhất hiện nay. Tại đây mọi người sẽ được trải nghiệm các game cá cược hấp dẫn như casino online , game bài và bắn cá. Với giao diện đồ họa thân thiện, dễ hiểu và kho giải thưởng lớn. Hãy tham gia ngay từ bây giờ để trải nghiệm thế giới cá cược tại BOM86.Thông tin chi tiết:Website: https://bom86.vip
The challenging actuality of stock market trading curbs is that every business has an uncertain result.
An outstanding share! I have just forwarded this onto a co-worker who has been conducting a little homework on this. And he in fact bought me lunch because I discovered it for him… lol. So let me reword this…. Thanks for the meal!! But yeah, thanx for spending the time to talk about this topic here on your internet site.
https://mexicaneasypharm.com/# best online pharmacies in mexico
legitimate canadian pharmacies
We truly appreciate your guidance and the effort you’ve extended. It matters greatly to us.
bookmarked!!, I love your blog!
pharmacy canadian https://indiancertpharm.shop/# Indian Cert Pharm
best online pharmacy india
Mexican Easy Pharm pharmacies in mexico that ship to usa medication from mexico pharmacy
buying prescription drugs in mexico online: best online pharmacies in mexico – Mexican Easy Pharm
In 2004, a dual-park format was examined, which opened elements of each parks, earlier than returning exclusively to Islands of Adventure in 2005.
NSDL Group comprises National Securities Depository Limited (abbreviated as NSDL), NSDL Database Management Restricted (NDML) and NSDL Funds Financial institution Restricted.
mexican pharmaceuticals online: Mexican Easy Pharm – Mexican Easy Pharm
скупка золота спб цена за грамм 585 skupkazolotospb.ru
maple leaf pharmacy in canada https://mexicaneasypharm.shop/# Mexican Easy Pharm
world pharmacy india
https://mexicaneasypharm.com/# mexican drugstore online
online canadian pharmacy
These ornament items are past beautiful and the silk bangles impart an look that could be very refined.
Оперативная помощь на дороге https://angeldorog.by/evakuator-minsk/ услуги эвакуатора, грузовой и легковой шиномонтаж, а также грузоперевозки фурами по доступным ценам. Работаем круглосуточно, быстро реагируем и гарантируем надежность. Звоните в любое время – решим вашу проблему!
bookmarked!!, I love your website.
Best surveillance camera software Home camera software
Indian pharmacy international shipping: Best online Indian pharmacy – Indian pharmacy that ships to usa
What trading pairs are available and is their customer support really good?
With numbers like these, we can’t hope to eradicate bugs, and with the huge and important function they play in our ecosystem, we wouldn’t want to.
скупка золота за грамм 585 skupkazolotospb.ru
darknet marketplace deep dark web https://github.com/darknetmarkets24/darknet-markets – deep web sites
Tracking the asset downtime is another vital feature that is provided by maintenance management software.
One stands in a primarily white dress, finished with fairly pale blue patterns; the opposite sits in a mild brown and white striped gown, with a darker brown mantelet.
canadian discount pharmacy https://canadianmdpharm.shop/# certified canadian international pharmacy
indian pharmacy online
mexico drug stores pharmacies: п»їbest mexican online pharmacies – Mexican Easy Pharm
the canadian drugstore trustworthy canadian pharmacy canadian pharmacy service
canadian pharmacy no rx needed: canadian mail order pharmacy – canadian discount pharmacy
As proven in this comfortable living room, issues don’t must be from the same period to work nicely together.
pharmacy canadian superstore https://indiancertpharm.com/# Online pharmacy
india pharmacy mail order
Oh my goodness! Impressive article dude! Many thanks, However I am experiencing troubles with your RSS. I don’t understand why I am unable to subscribe to it. Is there anybody else getting similar RSS problems? Anybody who knows the answer will you kindly respond? Thanks.
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
Hi88 là sân chơi lý tưởng cho những ai đam mê cá cược trực tuyến, với một loạt trò chơi hấp dẫn. Đăng nhập Hi88 truy cập tận hưởng ngay ưu đãi 88k miễn phí.
Vz99 mở ra những khoảnh khắc trải nghiệm cá cược mới lạ, với vô vàn siêu phẩm giải trí hiện đại, đầu tư chỉn chu về mọi mặt. Không chỉ được đánh giá cao về thư viện game,
canadian pharmacy reviews: Canadian Md Pharm – certified canadian pharmacy
88clb là một trong những chuyên trang casino trực tuyến đẳng cấp và uy tín nhất Châu Á. Cùng khám phá những nét nổi bật của nhà cái này qua bài viết sau đây.
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
If you’re new to MetaMask Wallet, start with https://metalead.org/. They offer step-by-step guidance on how to download and use MetaMask for browsers like Safari and Opera.
Darth Bane (Dessel) was a human Darkish Lord of the Sith and the only survivor of the Sith Order in the aftermath of the historical warfare between the Jedi and the Sith.
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
VB88 đã chính thức lọt top 10 nhà cái, được đánh giá bởi những trang đánh giá hàng đầu như Isle Of Man. Gần đây sân chơi đang nâng cấp mạnh mẽ những dịch vụ,
Hubet – Nhà cái đang thu hút sự chú ý mạnh mẽ trên thị trường cá cược. Với kho game đổi thưởng bao gồm các trò chơi nổi bật như nổ hũ, bắn cá, thể thao và casino.
QQ88 là nền tảng cá cược hàng đầu Việt Nam trong năm 2025, cung cấp những sản phẩm chất lượng cao và tỷ lệ cược hấp dẫn. Đăng ký để nhận ngay 88k ưu đãi.
canadianpharmacymeds com https://mexicaneasypharm.com/# mexican border pharmacies shipping to usa
reputable indian online pharmacy
Best Indian pharmacy: Online medicine – IndianCertPharm
Workers can work from home, saving time and on travel bills.
rent an electric car near me electrodrive.si
У нас вы можете купить айфоны https://vk.com/crazy_humor01 оптом по самым лучшим ценам. Оригинальные смартфоны Apple с гарантией качества. Постоянное наличие популярных моделей.
Major David Michael Munro Stevenson (495383), The Devonshire and Dorset Regiment.
Cổng game HUVIP88 nơi mang lại thế giới giải trí đẳng cấp với các trò chơi đổi thưởng hấp dẫn nhất năm 2025. Tại đây, người chơi có thể thử sức với các game bắn cá, đua ngựa, tài xỉu và các game bài nổi tiếng. HUVIP88 luôn cam kết bảo mật tuyệt đối, hỗ trợ người chơi 24/7 cùng với hàng loạt phần thưởng khủng cho cả thành viên mới và cũ, tạo nên một sân chơi uy tín và chuyên nghiệp.Thông tin chi tiết:Website: https://huvip88.net
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
If you contribute to a office or Self-Invested Personal Pension (SIPP), you obtain earnings tax relief at your marginal rate of tax – in other phrases, the highest rate you pay.
Квартирный переезд https://spb-gruzoperevozka.ru с грузчиками быстро и качественно! Упакуем, вынесем, перевезем и разместим вещи на новом месте. Надежная команда, аккуратность и доступные тарифы.
I blog quite often and I really thank you for your content. The article has really peaked my interest. I’m going to take a note of your website and keep checking for new details about once per week. I subscribed to your RSS feed too.
trustworthy canadian pharmacy Canadian Md Pharm canadian pharmacy online
стол для переговоров лофт https://mm26.ru
canadian neighbor pharmacy https://indiancertpharm.com/# indian pharmacy
indian pharmacy
https://indiancertpharm.shop/# Indian Cert Pharm
canadian pharmacy sarasota
стол для переговоров овальный https://mm26.ru
reputable mexican pharmacies online: buying from online mexican pharmacy – best online pharmacies in mexico
This is a topic that is near to my heart… Many thanks! Exactly where can I find the contact details for questions?
mexico pharmacies prescription drugs: medication from mexico pharmacy – reputable mexican pharmacies online
киного мультфильмы kinogo фильмы о космосе
kinogo фильмы для просмотра дома киного российские фильмы
Situated in the most prestigious areas of Crete, these sumptuous villas provide the perfect environment for an outstanding holiday. Find your perfect escape.
kinogo фильмы по жанрам киного фильмы
kinogo боевики 2025 киного фильмы про роботов
OR Realty — это ваш надежный партнер в мире недвижимости. Мы предлагаем большой выбор квартир, домов и коммерческих объектов по выгодным условиям. Наши специалисты помогут вам найти идеальный вариант, соответствующий вашим потребностям. Надежность, качество и удобство — вот что делает OR Realty лучшим выбором. Обращайтесь!
Best online Indian pharmacy: indian pharmacy – Indian Cert Pharm
Great post. I will be dealing with many of these issues as well..
canadian discount pharmacy https://mexicaneasypharm.com/# buying from online mexican pharmacy
reputable indian online pharmacy
Online medicine Indian Cert Pharm Indian Cert Pharm
It is not uncommon for Sith who have immersed themselves at nighttime aspect to have yellow eyes and pale pores and skin, as evidenced by Darth Sidious in Return of the Jedi and the newly corrupted Vader in Revenge of the Sith.
Emerging Market Bonds:- The issuing of these bonds take place in the emerging economies of the world or the developing countries.
Indian Cert Pharm: Online medicine – Best online Indian pharmacy
By understanding the risks associated with local weather change, taking preventive measures and staying informed about insurance options, homeowners in Jennings, Louisiana can protect their homes and save cash on insurance premiums over the long term.
I’m impressed, I must say. Rarely do I come across a blog that’s equally educative and interesting, and without a doubt, you’ve hit the nail on the head. The problem is something not enough folks are speaking intelligently about. I’m very happy that I came across this in my hunt for something regarding this.
They will be at ease that the company they hold a stake in has a good management team, who encourage and have good policies that they implement in the running of the organization.
проститутка в калуге снять девушку в калуге
mexican border pharmacies shipping to usa: buying from online mexican pharmacy – Mexican Easy Pharm
Audio enthusiasts have long complained about the damage being inflicted on music and listeners by the loudness war.
проститутка г. калуга снять шлюх калуга
программа производственного контроля лаборатории Москва программа план производственного контроля
модульные переговорные столы стол для переговоров
canadian pharmacy 24: Canadian Md Pharm – canadianpharmacymeds com
Yosefu Okwal s/o Rasan, Head Constable, Uganda Police Pressure.
An instance of symmetrical balance within the bathroom would come with a vanity with a mirror centered on the wall above and matching sconces flanking the mirror on each side.
спб стоимость золота в скупках прием скупка золота
canadian pharmacy uk delivery https://canadianmdpharm.com/# canada drugs online review
best india pharmacy
hcieqk
medicine in mexico pharmacies mexican pharmaceuticals online mexico pharmacies prescription drugs
canadapharmacyonline legit: reliable canadian pharmacy – canada pharmacy online
mexican rx online: mexican border pharmacies shipping to usa – п»їbest mexican online pharmacies
Out of the three options, all of them will make you some cash if you’re employed on it properly.
Most automobiles have laptop chips that management engine function, and thus, engine power.
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
The very next time I read a blog, Hopefully it doesn’t fail me as much as this particular one. I mean, I know it was my choice to read through, nonetheless I genuinely believed you would have something helpful to talk about. All I hear is a bunch of moaning about something you could possibly fix if you weren’t too busy searching for attention.
canadian pharmacy world reviews: CanadianMdPharm – canadian drugs online
Indian pharmacy international shipping: Indian pharmacy international shipping – Indian Cert Pharm
This is a topic that is close to my heart… Take care! Exactly where can I find the contact details for questions?
Some even take on a personality of their own, sometimes in a good way, and other times in a terrifying way.
the canadian pharmacy https://indiancertpharm.com/# IndianCertPharm
indian pharmacies safe
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
Nice article this is going to help my chinese mandarin tutoring service!
aviator mostbet strategiya mostbet yuklab olish
1win app ios 1win pro
mostbet mi mostbet affiliate
Web addiction could cause different well being issues.
IndianCertPharm Indian Cert Pharm reputable indian pharmacies
mexican border pharmacies shipping to usa: purple pharmacy mexico price list – Mexican Easy Pharm
Going to use this for my SEO agency!
sex nhật hiếp dâm trẻ em ấu dâm buôn bán vũ khí ma túy bán súng sextoy chơi đĩ sex bạo lực sex học đường tội phạm tình dục chơi les đĩ đực người mẫu bán dâm
buying prescription drugs in mexico: Mexican Easy Pharm – Mexican Easy Pharm
Best Indian pharmacy: IndianCertPharm – top 10 pharmacies in india
Thsi will help with my chinese online tutoring lessons.
It’s hard to find knowledgeable people in this particular subject, however, you seem like you know what you’re talking about! Thanks
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
The raw materials’ suppliers are Shanghai Faith Men Company.
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
Those who position themselves correctly on this bull market are going to witness the greatest wealth transfer of all time.
Indian Cert Pharm: indian pharmacies safe – indian pharmacy
canadian drugs online: CanadianMdPharm – trustworthy canadian pharmacy
On 15 October 2019, Chhetri became the one Indian to safe a spot in the list of prime 10 goalscorers in worldwide football.
Thsi will help with my Google Entity Stacking service.
Ed. Chief Communication Yeoman Desmond Frank Crook, P/JX541805.
Additionally, we are able to contrast past period accounting data and current interval and in addition deliberate figures for change evaluation.
Most heat pumps can have a higher electrical present demand when they begin.
Some states have responded by feeding extra well being information into the system.
Online pharmacy: IndianCertPharm – Indian Cert Pharm
Be sure that game difficulty escalates as gamers turn out to be extra accustomed to your interface and extra familiar together with your world.
For example, did you mark off 12 inches in your wheel?
Most often these allowances are both not maximized or blended.
Thsi will help with my Google Entity Stacking service.
https://mexicaneasypharm.com/# mexico drug stores pharmacies
pharmacy canadian
mexican pharmaceuticals online: Mexican Easy Pharm – Mexican Easy Pharm
This helps them to make quick decisions which in turn results in high profits.
киного 720p kinogo ретро-фильмы
киного фильмы для ноутбука киного топ-10
She was preceded in demise by her daughter, Ruby Dale Wooden; and husband, James Fred Grogan.
The IPO went off perfectly when a total of 19,605,052 shares were offered at $85 a share.
Joseph Philip, Chief Storekeeper, Drainage and Irrigation Division, Federation of Malaya.
Hi, I do believe this is an excellent web site. I stumbledupon it 😉 I am going to come back yet again since I saved as a favorite it. Money and freedom is the best way to change, may you be rich and continue to help others.
Congress proposed a $287 billion infrastructure invoice in 2019 called America’s Transportation Infrastructure Act that earmarked $4.9 billion over five years particularly for infrastructure tasks that enhance the resiliency of roads and bridges from extreme weather events.
Thsi will help with my Google Entity Stacking service.
mail order pharmacy india: Best online Indian pharmacy – Indian Cert Pharm
киного фильмы для просмотра дома kinogo приключения
киного фильмы по мотивам игр kinogo лучшие экшены
киного фильмы по сценаристам kinogo фильмы по странам
In case your price range allows, you may build up the look with put in supplies that create pleasing variations in your coloration theme.
This page was last edited on 9 November 2023, at 15:12 (UTC).
Discover, modify, and complete your Printable blank football play sheet template in a single interface with the help of sensible instruments.
Drop off and leave!
Thsi will help with my Google Entity Stacking service.
Miller: “Etta Leona Miller, daughter of pioneer Lincoln County residents John H and Ida E Jump, handed away at Davenport on Jan 30.
best online canadian pharmacy: best canadian online pharmacy – canadianpharmacyworld com
Alekhine won with 13/15 points, his solely loss being to Euwe who finished tied for second with Flohr at 12.
A modern AI tool ai undressing for working with images. Learn more about its features, capabilities and applications. Full privacy control and ease of use will ensure comfortable interaction.
kinogo фильмы про выживание киного фильмы про оборотней
mexico drug stores pharmacies: Mexican Easy Pharm – purple pharmacy mexico price list
Thsi will help with my Estrogen Blocker Supplements!
Хотите купить окна мелке каталог по разумной цене? Ознакомьтесь с нашим предложением! У нас — качество, надежность и стиль по доступной стоимости. Индивидуальный подход к каждому заказу!
вызвать проститутку калуга девушки по вызову г. калуга
услуги дизайнера интерьера квартиры цена https://dizayn-interera213.ru
legitimate canadian pharmacy online: Canadian Md Pharm – best canadian pharmacy online
Thsi will help with my Estrogen Blocker Supplements!
Online pharmacy: Online medicine – Best online Indian pharmacy
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
The biggest difference between the two is that investors in mutual funds get units that represent stocks.
legitimate canadian pharmacies: CanadianMdPharm – legitimate canadian pharmacies
I couldn’t resist commenting. Well written.
canadapharmacyonline legit https://indiancertpharm.shop/# top 10 pharmacies in india
cheapest online pharmacy india
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
Mexican Easy Pharm: Mexican Easy Pharm – mexico drug stores pharmacies
buying from online mexican pharmacy: mexican mail order pharmacies – Mexican Easy Pharm
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
sex nhật hiếp dâm trẻ em ấu dâm buôn bán vũ khí ma túy bán súng sextoy chơi đĩ sex bạo lực sex học đường tội phạm tình dục chơi les đĩ đực người mẫu bán dâm
Figures. They’re squeezing as a lot money as doable to their customers by limiting free stuff and truly nice merchandise.
181BET được nhiều tay chơi và chuyên gia đánh giá cao về thư viện game, hoạt động khuyến mãi cũng như dịch vụ khách hàng đi kèm.
Toronto Real Estate Updates!
заказать дизайнера интерьера дизайнер интерьера квартиры в москве
Thsi will help with my Estrogen Blocker Supplements!
Online medicine: Indian Cert Pharm – Online medicine
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
Mexican Easy Pharm: mexican rx online – buying prescription drugs in mexico
https://canadianmdpharm.com/# canadian drug stores
canadian pharmacy in canada
Thsi will help with my Estrogen Blocker Supplements!
darkmarket link the dark internet [url=https://github.com/darknetmarkets24/darknet-markets ]dark websites [/url]
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
Mexican Easy Pharm: mexican online pharmacies prescription drugs – buying from online mexican pharmacy
sex nhật hiếp dâm trẻ em ấu dâm buôn bán vũ khí ma túy bán súng sextoy chơi đĩ sex bạo lực sex học đường tội phạm tình dục chơi les đĩ đực người mẫu bán dâm
reputable mexican pharmacies online: Mexican Easy Pharm – mexican mail order pharmacies
sex nhật hiếp dâm trẻ em ấu dâm buôn bán vũ khí ma túy bán súng sextoy chơi đĩ sex bạo lực sex học đường tội phạm tình dục chơi les đĩ đực người mẫu bán dâm
Erlenmeyer flasks might be used in a number of ways in a laboratory, notably when it comes to experiments with liquids.
canada drugs online reviews: Canadian Md Pharm – reliable canadian pharmacy reviews
dark market list dark market https://github.com/darknetmarkets24/darknet-markets – darkmarket 2025
The website of forex companies itself offer great data that might help a newbie to begin trading.
pharmacy rx world canada: CanadianMdPharm – buying from canadian pharmacies
Howdy! This blog post could not be written much better! Looking at this post reminds me of my previous roommate! He continually kept preaching about this. I will send this information to him. Fairly certain he will have a good read. Thank you for sharing!
sex nhật hiếp dâm trẻ em ấu dâm buôn bán vũ khí ma túy bán súng sextoy chơi đĩ sex bạo lực sex học đường tội phạm tình dục chơi les đĩ đực người mẫu bán dâm
darkmarket url tor market links https://github.com/darknetmarkets24/darknet-markets – tor market
In Jodo Do Tigrinho online slots, every spin is a step towards victory! Incredible graphics, exciting themes and many bonuses await you. Fortune favors the brave – try your hand and discover the world of winnings with Tigrinho!
Cryptocurrency trading service bitqt with AI is automation and efficiency. Artificial intelligence monitors market dynamics, reduces risks and optimizes transactions. The perfect solution for beginners and professionals.
Like the flat tax, a national sales tax makes tax collection vastly simpler.
online slots Jodo Do Tigrinho are a unique combination of excitement and pleasure. Discover a variety of themes, bonus games and jackpots. Play comfortably, enjoying the well-thought-out interface and the chance to hit the jackpot!
Cryptocurrency trading service bitqt with AI is automation and efficiency. Artificial intelligence monitors market dynamics, reduces risks and optimizes transactions. The perfect solution for beginners and professionals.
sex nhật hiếp dâm trẻ em ấu dâm buôn bán vũ khí ma túy bán súng sextoy chơi đĩ sex bạo lực sex học đường tội phạm tình dục chơi les đĩ đực người mẫu bán dâm
ARS Information Service. “Imported Bees Not Supply Of Virus Associated with Colony Collapse Disorder.” American Beekeeping Federation.
0lbpav
By having this free printable debt payoff tracker posted in a central location in our house, it was a every day reminder of what we were working in the direction of as well as one of the simplest ways to remain centered with our personal finances.
darknet sites dark markets 2025 https://github.com/darknetmarkets24/darknet-markets – dark web search engines
legit canadian pharmacy: CanadianMdPharm – pharmacy canadian superstore
canadian pharmacy uk delivery: Canadian Md Pharm – pharmacy com canada
MetaMask Extension is the ultimate crypto wallet tool. From Chrome to Opera, it’s a breeze to use. Learn to maximize its features at https://metanaito.net/.
It’s additionally straightforward to read, which is perfect for followers looking for a lightweight feel-good read.
A ceremony at the Southwest Louisiana Veterans Dwelling honored those who died in service or handed after their tour of obligation – including the 219 veterans buried in Jennings at one of many five state veteran cemeteries in Louisiana.
The inspiration has derived old age people to buy designer leather jacket.
Aviatrix game https://aviatrix-games.com/en/ has become a sensation in the world of crash games. Its unique format, featuring a rapidly growing multiplier and the possibility of an unexpected crash. Aviatrix crash game is at 1win, 1xbet, Mostbet, and Pin Up.
The world economic system is in confusion, and main economies like the US, UK, Europe, and China are experiencing a recession.
IndianCertPharm: Indian Cert Pharm – Indian Cert Pharm
canadian pharmacy no scripts: CanadianMdPharm – trusted canadian pharmacy
Thsi will help with my Estrogen Blocker Supplements!
Walton continued to drive an old pickup truck and share budget-hotel rooms with colleagues on business trips, even after Walmart made him very rich.
доставка алкоголя ночью на дом заказать алкоголь на дом москва
It also needs to cover the journey/accommodation cost of the presenters.
Aviatrix game https://aviatrix-games.com/en/ has become a sensation in the world of crash games. Its unique format, featuring a rapidly growing multiplier and the possibility of an unexpected crash. Aviatrix crash game is at 1win, 1xbet, Mostbet, and Pin Up.
canadian pharmacy cheap: Canadian Md Pharm – canadian drug prices
Thsi will help with my Estrogen Blocker Supplements!
The stress of the flat area is defined because the decrease yield point (LYP) and outcomes from the formation and propagation of Lüders bands.
Each gadgets have a 5.7-inch display and use a dual-glass design with a 2.5D front and 3D rear glass.
thanks for this article!
pharmacies in mexico that ship to usa: mexico pharmacies prescription drugs – Mexican Easy Pharm
If private markets were able to provide efficient outcomes and if the distribution of income were socially acceptable, then there would be little or no scope for government.
Assume you want to retire in 20 years or send your child to a private university in ten.
darkmarket url how to access dark web https://github.com/darknetmarkets24/darknet-markets – tor darknet
Online pharmacy: Indian Cert Pharm – Indian Cert Pharm
thanks for this article!
American public opinion was nonetheless opposed to involvement in the problems of Europe and Asia, nonetheless.
sex nhật hiếp dâm trẻ em ấu dâm buôn bán vũ khí ma túy bán súng sextoy chơi đĩ sex bạo lực sex học đường tội phạm tình dục chơi les đĩ đực người mẫu bán dâm
2015’s Gayo Daejeon came about on 27 December at COEX Hall.
A mild ring at the highest outer edge gives status info, corresponding to the volume stage and whether the machine is streaming audio or the microphone is turned off, via numerous mild colors and motions.
https://indiancertpharm.com/# Indian pharmacy that ships to usa
canadian pharmacy online ship to usa
A unique, move up-beat, much less R&B like tune sounds refreshing within the combo.
A cell home lot is a chunk of land that belongs to the current park owner.
sex nhật hiếp dâm trẻ em ấu dâm buôn bán vũ khí ma túy bán súng sextoy chơi đĩ sex bạo lực sex học đường tội phạm tình dục chơi les đĩ đực người mẫu bán dâm
sex nhật hiếp dâm trẻ em ấu dâm buôn bán vũ khí ma túy bán súng sextoy chơi đĩ sex bạo lực sex học đường tội phạm tình dục chơi les đĩ đực người mẫu bán dâm
thanks for this article!
canadian online pharmacy: CanadianMdPharm – certified canadian international pharmacy
legal to buy prescription drugs from canada: CanadianMdPharm – canada online pharmacy
Mexican Easy Pharm Mexican Easy Pharm buying prescription drugs in mexico online
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
sex nhật hiếp dâm trẻ em ấu dâm buôn bán vũ khí ma túy bán súng sextoy chơi đĩ sex bạo lực sex học đường tội phạm tình dục chơi les đĩ đực người mẫu bán dâm
Online pharmacy: Indian pharmacy that ships to usa – india pharmacy mail order
sex nhật hiếp dâm trẻ em ấu dâm buôn bán vũ khí ma túy bán súng sextoy chơi đĩ sex bạo lực sex học đường tội phạm tình dục chơi les đĩ đực người mẫu bán dâm
canadian drugs: CanadianMdPharm – pharmacy in canada
Скачайте бесплатно книгу https://storitelling.ru по сторителлингу и узнайте, как создавать истории, которые цепляют с первых строк. Практические советы, примеры и вдохновение для всех, кто хочет освоить искусство рассказчика.
thanks for this article!
пластиковые окна под ключ цены окна милке цена
sex nhật hiếp dâm trẻ em ấu dâm buôn bán vũ khí ma túy bán súng sextoy chơi đĩ sex bạo lực sex học đường tội phạm tình dục chơi les đĩ đực người mẫu bán dâm
mexican drugstore online https://mexicaneasypharm.shop/# п»їbest mexican online pharmacies
reputable mexican pharmacies online
Nonetheless, Granada bridged a big market hole at an important time, interesting to both compact consumers with upscale aspirations and big-automobile homeowners now vitality-acutely aware for the primary time.
киного фильмы для детей kinogo фильмы про будущее
kinogo семейные сериалы киного фильмы о путешествиях
Mexican Easy Pharm: Mexican Easy Pharm – purple pharmacy mexico price list
dark web access dark web access https://github.com/darknetmarkets24/darknet-markets – tor darknet
Mexican Easy Pharm Mexican Easy Pharm Mexican Easy Pharm
thanks for this article!
Indian pharmacy that ships to usa: Indian Cert Pharm – Indian Cert Pharm
tor markets links deep web search https://github.com/darknetmarkets24/darknet-markets – free dark web
Certainly, there is extra spiritual unity between Hindustan and Burma than there is between Pakistan and Hindustan.
mexico drug stores pharmacies https://mexicaneasypharm.com/# mexican border pharmacies shipping to usa
п»їbest mexican online pharmacies
pharmacies in mexico that ship to usa: Mexican Easy Pharm – Mexican Easy Pharm
You made some good points there. I looked on the net to find out more about the issue and found most individuals will go along with your views on this site.
Chief Engine Room Artificer Charles Alfred Burton, D/Mx.60027.
Starting from the renowned Palace of Knossos and the gorgeous beaches of Elafonisi, Crete offers a wide range of adventures for all types of adventurers. Read more
thanks for this article!
Сайт игровых промокодов промокод на пополнение ggstandoff это ваш доступ к эксклюзивным бонусам и скидкам. Бесплатные награды, внутриигровая валюта и уникальные акции ждут вас. Успейте воспользоваться всеми возможностями!
Nonetheless, state officials have been unable to attain this ‘legible’ regime as a result of the state’s power to simplify the state was overcome by the overall inhabitants’s capability to “subvert, block and even overturn” the state’s attempt to standardize its populace.
sex nhật hiếp dâm trẻ em ấu dâm buôn bán vũ khí ma túy bán súng sextoy chơi đĩ sex bạo lực sex học đường tội phạm tình dục chơi les đĩ đực người mẫu bán dâm
sex nhật hiếp dâm trẻ em ấu dâm buôn bán vũ khí ma túy bán súng sextoy chơi đĩ sex bạo lực sex học đường tội phạm tình dục chơi les đĩ đực người mẫu bán dâm
Now I think the role of the Polish money will be growing and the number of the projects will increase because of the co-financing, although it’s eligible to get 85 now.
Put together the game by drawing a series of circles, squares, and triangles on a sidewalk.
Ищете промокоды для игр csgo skins промокод наш сайт – ваш лучший помощник! Собираем актуальные игровые промокоды для бонусов, скидок и эксклюзивных наград. Наслаждайтесь играми с максимальной выгодой – воспользуйтесь промокодами уже сегодня!
Its promotion to entry the world’s major market could be easily anticipated from the import and export information of Chile.
Хотите раскрутить продвижение телеграм мы знаем, как это сделать! Поможем увеличить охваты, привлечь активную аудиторию и вывести ваш контент на новый уровень.
выезд на дом капельница от запоя эффективные капельницы для лечения
thanks for this article!
The Simpsons Trip””. Blooloop.
Ищете промокоды для игр ggstandoff промокод на кейсы наш сайт – ваш лучший помощник! Собираем актуальные игровые промокоды для бонусов, скидок и эксклюзивных наград.
thanks for this article!
The very next time I read a blog, Hopefully it doesn’t disappoint me as much as this particular one. After all, I know it was my choice to read, but I actually thought you would have something interesting to talk about. All I hear is a bunch of moaning about something that you can fix if you weren’t too busy seeking attention.
Участок в Мишкином Лугу http://мишкинлуг.рф/uchastki-mishkinlug по Симферопольскому шоссе — идеальное место для строительства! Тихий поселок, прекрасные виды, удобный подъезд и все условия для комфортной жизни.
Лисичкин Очаг возле Серпухова https://лисичкиночаг.рф/uchastki-lisichkinochag идеальные участки для вашего будущего дома! Живописная природа, хорошая транспортная доступность и возможность подключения всех коммуникаций ждут вас.
Участки в Лисичкином Очаге https://лисичкиночаг.рф неподалеку от Серпухова. Тихий, зеленый поселок с прекрасной природой и удобной транспортной доступностью. Здесь вы сможете построить комфортное жилье для себя и своей семьи.
sex nhật hiếp dâm trẻ em ấu dâm buôn bán vũ khí ma túy bán súng sextoy chơi đĩ sex bạo lực sex học đường tội phạm tình dục chơi les đĩ đực người mẫu bán dâm
sex nhật hiếp dâm trẻ em ấu dâm buôn bán vũ khí ma túy bán súng sextoy chơi đĩ sex bạo lực sex học đường tội phạm tình dục chơi les đĩ đực người mẫu bán dâm
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
mexican drugstore online https://mexicaneasypharm.com/# Mexican Easy Pharm
mexican border pharmacies shipping to usa
mexican rx online: Mexican Easy Pharm – Mexican Easy Pharm
canadian medications CanadianMdPharm trusted canadian pharmacy
https://canadianmdpharm.shop/# canadian pharmacy uk delivery
best canadian pharmacy online
Typically this was as a result of discovering people who had been there was sophisticated for both architectural and UI design causes; sometimes it was because the folks they needed to grasp out with just weren’t on Mastodon, and weren’t going to be.
sex nhật hiếp dâm trẻ em ấu dâm buôn bán vũ khí ma túy bán súng sextoy chơi đĩ sex bạo lực sex học đường tội phạm tình dục chơi les đĩ đực người mẫu bán dâm
And if you buy them in abundance, you may not be able to consume them all before they expire.
sex nhật hiếp dâm trẻ em ấu dâm buôn bán vũ khí ma túy bán súng sextoy chơi đĩ sex bạo lực sex học đường tội phạm tình dục chơi les đĩ đực người mẫu bán dâm
Almost all of whatever you mention happens to be supprisingly precise and that makes me ponder why I had not looked at this in this light before. Your piece really did switch the light on for me personally as far as this issue goes. Nonetheless there is actually one particular point I am not really too comfy with so while I attempt to reconcile that with the central theme of the position, permit me see just what all the rest of your readers have to say.Very well done.
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
ABC88 là sự lựa chọn mới cho những tay chơi mong muốn trải nghiệm cảm giác cá cược thực thụ. Hàng ngàn điều thú vị trong kho tàng game đang chờ đón bạn.
https://cytpharm.com/# Cyt Pharm
cheap kamagra
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
You may want to take a look at the SBA definition of a small business prior to working with any type of outside financing your.
Visit the LakeLubbers shop for fun, recent designs you can customise!
buy cytotec online CytPharm buy cytotec online
I like it when folks get together and share views. Great blog, continue the good work.
Купить флешку оптом на укрин ключ и флешка в подарок женщине в Нижневартовске https://flashki-optom-1.ru/
cytotec buy online usa: buy cytotec online – buy cytotec online
Jili slot được mệnh danh là một trong những thương hiệu hàng đầu chuyên về dòng game nổ hũ đổi thưởng. Cùng khám phá những điểm khác biệt của sân chơi này.
Именная флешка оптом с гравировкой купить и стильные флешки в Самаре https://flashki-optom-1.ru/
https://odnazhdyvskazke-tv.ru/
Отзывы о компаниях и работодателях https://potrebsojuz.ru в одном месте. Узнайте реальное мнение сотрудников и клиентов, чтобы принять правильное решение при выборе работы или услуг.
https://predpharm.shop/# Pred Pharm
prednisone online for sale
Комплексная юридическая помощь https://kramzenergo.ru для вас и вашего бизнеса. Анализ дел, представительство в судах, поддержка на всех этапах
buy semaglutide: semaglutide tablets price – semaglutide tablets for weight loss
http://semapharm24.com/# semaglutide tablets for weight loss
buy Kamagra
https://odnazhdyvskazke-tv.ru/
Way cool! Some very valid points! I appreciate you writing this write-up plus the rest of the site is extremely good.
glory-casino-bd.online
I really like it when folks get together and share ideas. Great site, keep it up.
Kamagra Oral Jelly: sildenafil oral jelly 100mg kamagra – Kama Pharm
glory-casino-bd.online
Thanks for your post made here. One thing I’d like to say is that often most professional fields consider the Bachelors Degree as the entry level requirement for an online certification. Even though Associate College diplomas are a great way to get started on, completing your current Bachelors reveals many entrances to various employment goodies, there are numerous on-line Bachelor Diploma Programs available from institutions like The University of Phoenix, Intercontinental University Online and Kaplan. Another concern is that many brick and mortar institutions offer Online versions of their certifications but typically for a greatly higher fee than the corporations that specialize in online diploma programs.
In some cases, people may supply financial compensation to their spouse as a part of the association.
drug markets onion darknet market links black internet
The Orioles are credited with utilizing it throughout the useless-ball era.
semaglutide tablets store: cheap semaglutide pills – semaglutide tablets price
PredPharm buy cheap prednisone PredPharm
Vavada Casino to miejsce, gdzie emocje gry są zawsze na wyciągnięcie ręki. Oferujemy bogaty wybór najlepszych automatów do gier, klasycznych gier stołowych, takich jak poker, blackjack czy bakarat, a także wciągającą ruletkę na żywo z udziałem profesjonalnych krupierów. Nasza platforma Vavada PL jest w pełni licencjonowana i zgodna z obowiązującymi przepisami prawa, co zapewnia bezpieczne i legalne środowisko rozgrywki dla wszystkich graczy.
Their jewellery includes the maang tikka, necklace, bangles, and extra.
The best way this plays out is that after supply shock happens, the economic system first tries to keep up momentum.
https://cytpharm.shop/# buy cytotec pills
Kamagra tablets
клиника капельниц http://www.medlinks.ru/article.php?sid=110769
https://kamapharm.com/# Kama Pharm
prednisone cost us
1win mujeres 1win es seguro
1win mines 1win brasil
darknet links the dark internet dark web websites
semaglutide tablets price: semaglutide tablets for weight loss – semaglutide tablets price
These are venues just like the Gielgud, Dominion and Garrick, where eminent theatrical figures reminiscent of Laurence Olivier have trodden the boards.
This site was… how do I say it? Relevant!! Finally I’ve found something that helped me. Many thanks!
Secondly, 130-30 funds are typically regulated under the jurisdiction of traditional investment funds, and for this reason they are allowed to market themselves to the general public.
How outdated would you be for those who did not know how old you are?
In order to prepare a successful occasion, you need to consider having the whole lot at your fingertips simply to ensure that everything goes well.
High leverage also encourages overtrading and overextending oneself, which is not the best course of action for a newbie.
Откройте для себя историю смотреть слово пацана бесплатно онлайн все серии честный взгляд на суровую реальность, где дружба и слово дороже всего. Уникальный проект о жизни без прикрас и ценности принципов.
CytPharm: cytotec abortion pill – CytPharm
https://cytpharm.com/# Cyt Pharm
Kamagra Oral Jelly
Survivors are two daughters, Mrs.
darknet search engine darknet sites how to get on dark web
And weight increased a mere 321 pounds between 1965 Cyclone and 1966 GT hardtops.
PredPharm: prednisone 1 tablet – Pred Pharm
semaglutide tablets price SemaPharm24 semaglutide tablets
https://kamapharm.com/# Kama Pharm
how much is prednisone 10 mg
How about utilizing a couple of fashionable tea towels to make an apron?
Recomendo a todos. Chegou conforme descrito.
dark market list darknet seiten deep web links
Kama Pharm: Kama Pharm – Kama Pharm
https://kamapharm.com/# Kamagra 100mg price
super kamagra
If you’re looking to download MetaMask, I highly recommend visiting https://kingroada.com/ for step-by-step instructions and insights.
darknet market links tor market links tor darknet
Priligy tablets: buy dapoxetine online – buy dapoxetine online
come on hasilkan uang dan dibimbing Rina https://elearning.adobe.com/profile/rina_8544
Kama Pharm: Kama Pharm – Kama Pharm
https://cytpharm.com/# Cyt Pharm
can you buy prednisone over the counter in canada
888B tự tin là nhà cái uy tín đẳng cấp hàng đầu Châu Á. Đăng ký tài khoản tại 888bb.sbs để nhận 88k vốn cược miễn phí với vô số ưu đãi!
DapPharm Priligy tablets Priligy tablets
http://predpharm.com/# buy prednisone tablets uk
cheap kamagra
Vavada Casino to miejsce, gdzie emocje gry są zawsze na wyciągnięcie ręki. Oferujemy bogaty wybór najlepszych automatów do gier, klasycznych gier stołowych, takich jak poker, blackjack czy bakarat, a także wciągającą ruletkę na żywo z udziałem profesjonalnych krupierów. Nasza platforma Vavada Casino jest w pełni licencjonowana i zgodna z obowiązującymi przepisami prawa, co zapewnia bezpieczne i legalne środowisko rozgrywki dla wszystkich graczy.
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
Immediate results after using, very convenient.
The material is very durable, will last a long time.
kinogo короткометражки kinogo дублированные фильмы
kinogo криминал kinogo фильмы про природу
TK88 là nhà cái cá cược uy tín nhất tại Việt Nam với hệ thống bảo mật cao, đa dạng sản phẩm và thường xuyên có các sự kiện ưu đãi lớn.
kinogo фильмы для отдыха kinogo поиск фильмов
Kama Pharm: sildenafil oral jelly 100mg kamagra – Kamagra tablets
Witaj w Slottica PL! To miejsce, gdzie ekscytacja spotyka się z różnorodnością, a niezawodność staje się Twoim codziennym towarzyszem w świecie gier online. Dla polskich graczy w Slottica Casino przygotowaliśmy ofertę, która spełni wszystkie oczekiwania – od doskonałej kompatybilności mobilnej, przez szeroką gamę gier, aż po usługi skoncentrowane na Twoim komforcie i bezpieczeństwie.
You should be a part of a contest for one of the highest quality sites on the web. I most certainly will highly recommend this web site!
Can One Man’s Actions Take $6 Billion In Value Out Of A Minor Metal Market In A Month?
Witaj w Slottica PL! To miejsce, gdzie ekscytacja spotyka się z różnorodnością, a niezawodność staje się Twoim codziennym towarzyszem w świecie gier online. Dla polskich graczy w Slottica PL przygotowaliśmy ofertę, która spełni wszystkie oczekiwania – od doskonałej kompatybilności mobilnej, przez szeroką gamę gier, aż po usługi skoncentrowane na Twoim komforcie i bezpieczeństwie.
Priligy tablets: buy priligy – buy dapoxetine online
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
https://cytpharm.shop/# Cyt Pharm
Kamagra Oral Jelly
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
Priligy tablets: dap pharm – Priligy tablets
How will they handle the dangers for which the evidence is already earlier than us?
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
https://semapharm24.com/# SemaPharm24
prednisone for sale online
Kama Pharm Kama Pharm Kamagra Oral Jelly
The company claims to use a “nine step purification course of that features ozone, ultraviolet and microfiltration.” This sounds nice, but still — does that really make it price $55?
In an informal poll by the Norwegian Chess Federation in 1999, this sport was voted to be the perfect Norwegian game.
buy cytotec online: CytPharm – Cyt Pharm
https://semapharm24.shop/# semaglutide tablets store
Kamagra 100mg price
Быстрое оформление медицинской лицензии с гарантией по договору. Узнайте подробности: https://www.udrpsearch.com/user/LicenzPro
Simons, Ilana, Ph.D. “Why do we’ve got emotions?” Psychology Immediately.
purchase cytotec: cytotec online – Misoprostol 200 mg buy online
I blog frequently and I genuinely thank you for your content. This great article has really peaked my interest. I will take a note of your site and keep checking for new information about once a week. I subscribed to your Feed too.
dark markets tor market url darknet market list
Unlike in NASCAR racing, the place automobiles are ostensibly saved near inventory, whiskey vehicles had been modified to present them every potential advantage over legislation enforcement.
Black pawns are transferring down the board and cannot seize the White knight.
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
deep web sites darknet drugs darknet site
buy semaglutide: semaglutide best price – semaglutide tablets
When the COVID-19 pandemic hit in 2020, the analysis was sidelined for months, during which 7 percent of the pattern degraded every 30 days.
https://dappharm.shop/# buy dapoxetine online
cheap kamagra
Kamagra 100mg price Kamagra 100mg price Kamagra 100mg price
generic rybelsus tabs: SemaPharm24 – cheap semaglutide pills
https://predpharm.com/# prednisone 5mg over the counter
apo prednisone
Tabulating machines for data processing began being widely used in the 1920s and 1930s and remained in use until mainframe computers became widespread in the late 1960s through the 1970s.
Откройте для себя bs2best at возможности даркнет-рынка с тысячами предложений. Быстрая регистрация, надежные сделки и анонимность на каждом этапе.
Because of low unemployment and a rise in income, The United States managed to surpass their pre-pandemic level of economic output.
Лучшее онлайн казино https://1wincasino.pl Огромный выбор автоматов, настольных игр и live-казино. Уникальные акции, приветственные бонусы и мгновенные выплаты сделают вашу игру еще интереснее.
bitcoin dark web darkmarket list free dark web
текст песни где ты https://faav.ru
Hello, I think your web site could possibly be having internet browser compatibility problems. Whenever I look at your website in Safari, it looks fine however, if opening in Internet Explorer, it’s got some overlapping issues. I just wanted to give you a quick heads up! Besides that, wonderful site.
I will not repeat all the vendor data that is on my companion web page about buying a regulation checkers set: checker-sets.html .
Shares usually confer a number of rights on the holder.
If you are not dwelling in your home while the construction is going on, it’s a good suggestion to drop in day by day, or at the least every few days, to see how issues are going.
You’ll be able to place seedlings on a desk or counter and suspend the store gentle from the ceiling over them, or arrange three or four tiered gentle stands.
onion market darknet drugs black internet
https://kamapharm.shop/# Kamagra Oral Jelly
super kamagra
Switching to Metamask on Firefox was seamless. A big thanks to the amazing guides at https://metamenu.org/ for making it hassle-free!
CytPharm: CytPharm – cytotec online
Merely place it within the oven, depart it for the recommended interval and your equipment is sweet for use once more.
охота на лося охотничья лодка
The courses offered in the highest administration colleges of the world are meant to fit the needs of the students for training and knowledge, as well as the requirements of the tourism industry itself.
dapoxetine price: dap pharm – DapPharm
deep web drug url darknet search engine darknet market links
GE Garanti Bank, a bank detained by GE Capital in a joint venture with Garanti Bank International from Turkey.
рыболовные снасти для хариуса рыбалка на глубине
надежный маркетплейс bs2best at где сочетаются безопасность, широкий выбор товаров и удобство использования. Платформа работает с анонимными платежами и гарантирует полную конфиденциальность для всех пользователей.
free dark web dark net deep web drug store
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
https://cytpharm.com/# buy cytotec over the counter
buy kamagra online usa
That is a great tip especially to those new to the blogosphere. Simple but very precise information… Thank you for sharing this one. A must read post!
https://dappharm.com/# cheap priligy
can you buy prednisone without a prescription
cheap priligy: dapoxetine price – dap pharm
33win – 33wincom.xyz đang là một trong những thương hiệu casino trực tuyến đi đầu thị trường hiện nay. Cùng khám phá các điểm đặc biệt của nhà cái này qua bài viết sau.
dark market onion dark websites darkmarket
Priligy tablets: dapoxetine online – DapPharm
tor markets links dark web access dark web links
Okking là thương hiệu hàng đầu trong ngành casino, được đông đảo người chơi tin tưởng và lựa chọn. Nhà cái đã vượt qua nhiều đối thủ khác trong cùng lĩnh vực.
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
http://cytpharm.com/# buy cytotec online
super kamagra
buy cytotec online: Misoprostol 200 mg buy online – buy cytotec online
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
darknet markets 2025 dark websites blackweb
dap pharm: buy priligy – priligy
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
deep web drug store darknet sites tor markets 2025
http://dappharm.com/# Priligy tablets
how much is prednisone 10 mg
buy priligy buy priligy buy priligy
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
https://predpharm.shop/# Pred Pharm
buy Kamagra
Many graduates in Nigeria don’t earn such amounts per month if solely they see the jobs.
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
Университет ресторанного бизнеса https://upskilll.ru/university UPSKILL: обучаем рестораторов, управляющих и сотрудников ресторанов, полностью адаптируя наши курсы, тренинги и программы обучения под особенности каждого заведения.
darknet markets 2025 dark market onion darknet drugs
For example, you might not have to buy detergent, fabric softener and odor eliminators as a result of one laundry pod can do the work of all three.
It diverts the runoff collected from the drainage system in the low-mendacity area to the underground storage tank.
dark web drug marketplace dark market url
darknet market lists https://github.com/darknetmarkets24/darknet-markets – tor markets 2022
darkmarket darkmarket 2022
dark markets https://github.com/darknetmarkets24/darknet-markets dark web market list
Интересуют современные решения для наливных полов? Могу посоветовать надежную компанию, смотрите https://makeprojects.com/profile?activeTab=TabProjectBoards
buy dapoxetine online: dapoxetine price – dap pharm
Though I don’t assume this is likely, Signal’s closed platform leaves users weak to user domestication.
dapoxetine online: DapPharm – buy dapoxetine online
In 1947, a consortium of oil companies built the first platform that you couldn’t see from land in the Gulf of Mexico.
He took half in the Chess World Cup 2011, the place he was eliminated in the primary spherical by Mikhail Kobalia.
The Reserve Bank of India Act, 1934, was amended by Finance Act (India), 2016, to constitute MPC which is able to deliver extra transparency and accountability in fixing India’s financial policy.
best darknet markets darknet search engine blackweb official website
ремонт стиральных машин недорого ремонт стиральных машин indesit цена
Sherbet on the other hand can contain dairy in it.
A variable interest price will change as these curiosity charges change, but a variable price plan must even have a cap on how excessive the rate can go during the time period of the plan.
Bitcoin is a highly contentious digital currency, slowly taking over the banks.
dark web drug marketplace darknet drug market
tor markets links https://github.com/darknetmarkets24/darknet-markets darknet sites
dark market deep web drug links
Taxes are a blessing in disguise.
darknet market links deep web drug links blackweb
https://semapharm24.com/# Sema Pharm 24
п»їkamagra
dark web drug marketplace darknet market lists
semaglutide tablets for weight loss: buy rybelsus online – semaglutide tablets
prednisone 20 mg in india: generic over the counter prednisone – PredPharm
https://cytpharm.shop/# buy cytotec
buy prednisone 5mg canada
deep web drug markets https://github.com/darknetmarkets24/darknet-markets – dark web market
darknet markets best darknet markets how to get on dark web
The signal is normally quite simple — only a sine wave, or presumably two sine waves at different powers.
onion market dark market url
dark web links https://github.com/darknetmarkets24/darknet-markets tor market links
buy Kamagra sildenafil oral jelly 100mg kamagra Kama Pharm
onion market darknet sites
darknet drugs darknet drugs darkmarket link
These insurance coverage plans supply complete healthcare advantages while students are enrolled at overseas areas.
darkmarkets https://github.com/darknetmarkets24/darknet-markets – darknet drug market
https://kamapharm.com/# Kama Pharm
super kamagra
If you, too, are interested in this form of property ownership, you can connect with the professionals from FAI Exchange.
tor markets 2022 darkmarket
darknet site https://github.com/darknetmarkets24/darknet-markets tor dark web
darkmarket url dark markets 2022
With rising stars such as Dubai Electricity and Water Authority (DEWA) moving from High Yield (HY) to IG, Dubai now include just three investment grade issuers – the other two being DP World and Majid Al Futtaim.
buy rybelsus online: semaglutide tablets – Sema Pharm 24
cheap priligy: buy dapoxetine online – dap pharm
drug markets onion dark web search engines darknet search engine
Проверенные специалисты по разработке на Битрикс. Подробнее: https://www.jewishboston.com/profile/wrp/
best darknet markets darkmarket 2022
drug markets onion https://github.com/darknetmarkets24/darknet-markets – dark market url
dark web market links tor markets
deep web drug url deep web drug links
dark web site deep web drug url dark markets
https://cytpharm.shop/# buy cytotec online
prednisone 30 mg daily
darkmarket 2022 dark web drug marketplace
http://predpharm.com/# Pred Pharm
buy kamagra online usa
Such an wonderful entry! The insight shared is extremely helpful and well-written. Many thanks for putting in the work to compose this.
dark web links https://github.com/darknetmarkets24/darknet-markets – darknet marketplace
CytPharm: buy cytotec over the counter – buy cytotec online
dark markets darknet markets
dark market link drug markets dark web
deep dark web darknet market lists dark web sites
Платформа Курьер Купер https://cash-kuper.ru открывает возможности для работы в доставке. Свободный график, прозрачная система оплаты и заказы поблизости – идеальный выбор для тех, кто ищет подработку или основной заработок.
Pred Pharm: Pred Pharm – prednisone canada
dark market 2022 darknet drug market
buy priligy cheap priligy buy priligy
dark web market list dark net deep web sites
This is a topic which is near to my heart… Thank you! Exactly where can I find the contact details for questions?
Abortion pills online: п»їcytotec pills online – buy cytotec online
darknet search engine darknet markets 2025 darkmarket link
prednisone buying: medicine prednisone 5mg – prednisone 20 mg tablets
But with all that has happened within Greece and Spain, bonds truly are one of the worst investment classes now to get into for future asset protection.
http://semapharm24.com/# semaglutide tablets price
40 mg prednisone pill
http://dappharm.com/# dapoxetine online
Kamagra 100mg
tor market url darknet marketplace deep web drug url
88CLB quy tụ hơn 4000 trò chơi và 10 triệu thành viên đăng ký tham gia. Vô vàn cơ hội đổi đời cực khủng đang đón chờ bạn mỗi ngày.
dark web link dark market 2022
onion market https://github.com/darknetmarkets24/darknet-markets – dark websites
darknet market dark web market dark market list
cheap priligy: cheap priligy – dapoxetine online
darkmarkets https://github.com/darknetmarkets24/darknet-markets darknet sites
Oh my goodness! Amazing article dude! Thanks, However I am encountering troubles with your RSS. I don’t know why I am unable to join it. Is there anybody else getting the same RSS problems? Anyone that knows the answer will you kindly respond? Thanks!
Okking là nhà cái uy tín cung cấp đầy đủ các thể loại game đa dạng, với hơn 100 trò chơi cùng với vô vàn chương trình khuyến mãi siêu hot.
dap pharm: DapPharm – Priligy tablets
SemaPharm24 generic rybelsus tabs semaglutide tablets price
As quickly as six hours after surgical procedure, a affected person ought to start strolling round in order to forestall DVT.
dark internet dark web search engines dark web search engines
thc joint in prague https://shop-cannabis-prague.com
ремонт водонагревателя аристон 100 ремонт бойлера
darknet websites darknet market links
DapPharm: buy dapoxetine online – Priligy tablets
tor markets links https://github.com/darknetmarkets24/darknet-markets – darkmarket
My artner and I strumbled over here coming from a different page
and thought I should check things out. I lioke what I see so now i’m following you.
Look forward to looking into your web pqge repeatedly. https://Www.Waste-Ndc.pro/community/profile/tressa79906983/
darknet market darknet drug market darknet site
dark markets 2022 tor markets
deep web drug store https://github.com/darknetmarkets24/darknet-markets darknet market list
A motivating discussion is definitely worth comment. I do think that you ought to write more about this issue, it may not be a taboo subject but usually people don’t speak about such subjects. To the next! Many thanks!
Nature therapy has been found to scale back signs of anxiety, depression, and stress, and contribute to general psychological nicely-being.
https://semapharm24.com/# cheap semaglutide pills
buy prednisone 20mg
3 July 1778: A power of British troopers, led by John Butler, with the assistance of about seven hundred Indians, attacked and killed practically 300 Wyoming Valley settlers.
buy cytotec online: order cytotec online – purchase cytotec
http://semapharm24.com/# semaglutide tablets for weight loss
cheap kamagra
займ онлайн на карту круглосуточно микрозайм онлайн
darkweb marketplace darkmarket 2022
darknet markets 2025 darknet market links darkmarket 2025
Hmm is anyone else experiencing problems with the pictures on this blog loading? I’m trying to determine if its a problem on my end or if it’s the blog. Any responses would be greatly appreciated.
How can one have a company strategy in place however, not an organization communication technique as a component?
Pred Pharm: prednisone 10 mg tablet cost – Pred Pharm
Could it’s money, position, or even his physique; this hopeless narcissist will give it all.
The contractor’s insurance covers you for on-site problems, like an injured worker who otherwise might sue you for medical costs or damaged property that you’d have to replace out of your own pocket.
tor markets deep dark web
Considered one of the simplest (and free) methods to get the net speaking about your model is to talk at an occasion.
darkmarket https://github.com/darknetmarkets24/darknet-markets – dark markets 2022
tor markets dark market onion
Kama Pharm: buy Kamagra – Kama Pharm
dark web link https://github.com/darknetmarkets24/darknet-markets dark websites
https://predpharm.com/# Pred Pharm
prednisone 7.5 mg
Sema Pharm 24 buy rybelsus online buy semaglutide
dark web sites dark web markets
how to get on dark web dark web drug marketplace dark web sites links
buy misoprostol over the counter: Cyt Pharm – Cyt Pharm
https://semapharm24.com/# SemaPharm24
buy kamagra online usa
dark market url darkweb marketplace
займы карты без онлайн срочно займы
The Retail Sales Index is released at 8:30 am EST around the 12th of the month; it reflects data from the previous month.
darknet drug links https://github.com/darknetmarkets24/darknet-markets – dark market
darknet drug store dark web search engine dark market
PredPharm: Pred Pharm – prednisone 50 mg tablet canada
drug markets onion darkmarket 2022
Wonderful article. It’s very articulate and full of valuable details. Thanks for sharing this information.
darkmarket list https://github.com/darknetmarkets24/darknet-markets tor darknet
dark web market links dark websites dark web sites links
dark market list tor market url
cheap semaglutide pills: semaglutide tablets store – generic rybelsus tabs
Bukmacher oraz kasyno internetowe Mostbet PL to jeden z najdłużej działających serwisów hazardowych w sieci z ofertą dla Polaków, gdyż został założony jeszcze w 2009 roku. Platforma może pochwalić się posiadaniem aktywnej licencji od Curacao, która gwarantuje bezpieczeństwo. Gracze w Mostbet Casino będą mogli spotkać tutaj ponad 3000 zróżnicowanych gier hazardowych, które zostały podzielone na automaty, gry stołowe oraz gry na żywo.
https://semapharm24.shop/# semaglutide best price
canada pharmacy prednisone
Bukmacher oraz kasyno internetowe Mostbet PL to jeden z najdłużej działających serwisów hazardowych w sieci z ofertą dla Polaków, gdyż został założony jeszcze w 2009 roku. Platforma może pochwalić się posiadaniem aktywnej licencji od Curacao, która gwarantuje bezpieczeństwo. Gracze w Mostbet Casino będą mogli spotkać tutaj ponad 3000 zróżnicowanych gier hazardowych, które zostały podzielone na automaty, gry stołowe oraz gry na żywo.
darknet drug market dark web drug marketplace
Открывайте кейсы CS:GO https://www.facebook.com/people/Hotdrop_CSGO/61550490187523/ с крутыми шансами на редкие скины. Удобный интерфейс, надежная система и огромный выбор кейсов сделают игру еще интереснее. Начните свой путь к топовым скинам прямо сейчас!
semaglutide tablets store: Sema Pharm 24 – Sema Pharm 24
Attractive section of content. I just stumbled upon your blog and in accession capital to assert that I acquire actually enjoyed account your blog posts. Any way I will be subscribing to your augment and even I achievement you access consistently rapidly.
dark market list https://github.com/darknetmarkets24/darknet-markets – dark websites
deep web drug url darknet market
darkmarket list https://github.com/darknetmarkets24/darknet-markets tor markets
dapoxetine online: dapoxetine price – DapPharm
dark web drug marketplace darkweb marketplace
Greetings! After reading through a number of the articles, I discovered that, although I could have sworn I had been to this website previously, I had never there. I’m glad I found it, though, and I’ll be bookmarking it and returning frequently!|
Greetings! After reading through a number of the articles, I discovered that, although I could have sworn I had been to this website previously, I had never there. I’m glad I found it, though, and I’ll be bookmarking it and returning frequently!|
Hello everyone, I hope all is well with you. Of course, everyone is exchanging information, which is acceptable. Keep posting.|
Hello everyone, I hope all is well with you. Of course, everyone is exchanging information, which is acceptable. Keep posting.|
http://farmatadalitaly.com/# farmacie online affidabili
farmacie online sicure
viagra originale in 24 ore contrassegno viagra cerco viagra a buon prezzo
Mobile gambling
Откройте яркие кейсы CS:GO https://m.youtube.com/@hotdrop-case и получите шанс выиграть топовые скины! Широкий выбор кейсов, высокий шанс дропа и честная система обеспечат увлекательный опыт.
farmacie online autorizzate elenco: Brufen senza ricetta – migliori farmacie online 2024
farmacia online
http://farmasilditaly.com/# dove acquistare viagra in modo sicuro
farmacia online senza ricetta
farmacia online senza ricetta: FarmaBrufen – Farmacie on line spedizione gratuita
https://farmatadalitaly.shop/# top farmacia online
Farmacie online sicure
Пробуйте удачу https://discord.com/invite/B5fF6pW8Cm CS:GO! Шанс получить редкие и дорогие скины, широкий выбор кейсов и удобный интерфейс делают процесс открытия легким и захватывающим.
Рискни и испытай удачу https://t.me/hotdropcases Шанс получить редкие и дорогие скины, широкий выбор кейсов и удобный интерфейс делают процесс открытия легким и захватывающим.
pillole per erezione in farmacia senza ricetta viagra senza ricetta pillole per erezione in farmacia senza ricetta
top farmacia online: Ibuprofene 600 prezzo senza ricetta – comprare farmaci online all’estero
farmacia online senza ricetta
viagra consegna in 24 ore pagamento alla consegna: Farma Sild Italy – pillole per erezione immediata
https://farmatadalitaly.shop/# farmacia online senza ricetta
Farmacia online miglior prezzo
Ваши любимые кейсы CS:GO https://t.me/s/hotdropcases в одном месте! Большой выбор, удобный интерфейс и высокая вероятность выпадения редких предметов делают процесс открытия кейсов по-настоящему захватывающим.
https://farmabrufen.shop/# FarmaBrufen
farmacia online
Сервис бытовых услуг https://gidrostok-servis.ru это удобное решение для любых домашних задач. Уборка, ремонт, сантехника, установка техники и многое другое. Надежные специалисты, быстрое выполнение и доступные цены!
Подарки рекламные оптом и купить сувениры дешево во Владикавказе: сувениры для партнеров по бизнесу оптом
farmacia online: Farma Brufen – top farmacia online
farmacia online
Farmacia online piГ№ conveniente: Cialis senza ricetta – top farmacia online
http://farmabrufen.com/# Farma Brufen
farmacie online affidabili
farmacie online sicure Ibuprofene 600 prezzo senza ricetta farmacie online affidabili
https://farmaprodotti.com/# acquisto farmaci con ricetta
farmacia online
Реклама подарка на новый год и панда сувениры оптом во Владивостоке https://podarki-v-moskve.ru/
Farmacia online miglior prezzo: Cialis generico prezzo – Farmacia online piГ№ conveniente
farmacia online senza ricetta
comprare farmaci online con ricetta: Tadalafil generico migliore – farmacie online sicure
http://farmaprodotti.com/# Farmacia online miglior prezzo
acquistare farmaci senza ricetta
Adored the information in this post. It’s highly comprehensive and filled with beneficial information. Fantastic effort!
This post is extremely enlightening. I genuinely appreciated reading it. The details is very arranged and easy to comprehend.
darknet market list dark net blackweb
tor darknet darknet drug links
Adored the details in this post. It’s extremely well-researched and packed with helpful insights. Great effort!
п»їFarmacia online migliore: BRUFEN 600 acquisto online – farmacie online sicure
farmacia online
darkmarket link tor dark web
darknet market dark web markets
darknet market https://github.com/darknetmarkets24/darknet-markets darkmarket list
романтические фильмы 2025 подборка фильмы в HD качестве в хорошем качестве
https://farmaprodotti.shop/# acquisto farmaci con ricetta
farmacie online sicure
п»їFarmacia online migliore: Brufen senza ricetta – farmaci senza ricetta elenco
https://farmaprodotti.shop/# top farmacia online
farmacie online sicure
Нужны деньги срочно займ с быстрым одобрением и моментальным переводом на карту. Минимум документов, удобные условия и прозрачные ставки. Оформите займ прямо сейчас!
лучшие популярные фильмы 2025 фильмы смотреть лучшие аниме 2025 онлайн
darknet site dark market tor marketplace
viagra cosa serve viagra farmacia dove acquistare viagra in modo sicuro
viagra cosa serve: Viagra – viagra subito
acquistare farmaci senza ricetta
Промокоды для игр https://esportpromo.com/ это бесплатные бонусы, скидки и эксклюзивные награды! Находите актуальные коды, используйте их и получайте максимум удовольствия от игры без лишних затрат.
Лучшие игровые промокоды cs 2 код в одном месте! Активируйте бонусы, получайте подарки и прокачивайте аккаунт без лишних затрат. Следите за обновлениями, чтобы не пропустить новые промо!
darknet market lists tor market url
best darknet markets drug markets onion
dark web market list https://github.com/darknetmarkets24/darknet-markets – darknet websites
tor market url dark market link
viagra originale in 24 ore contrassegno: cerco viagra a buon prezzo – pillole per erezione in farmacia senza ricetta
dark web links https://github.com/darknetmarkets24/darknet-markets dark web sites
https://farmasilditaly.shop/# cialis farmacia senza ricetta
farmaci senza ricetta elenco
Лучшие игровые промокоды промокоды на барабан ггстандофф в одном месте! Активируйте бонусы, получайте подарки и прокачивайте аккаунт без лишних затрат. Следите за обновлениями, чтобы не пропустить новые промо!
viagra 50 mg prezzo in farmacia: FarmaSildItaly – alternativa al viagra senza ricetta in farmacia
п»їFarmacia online migliore
viagra online spedizione gratuita viagra prezzo viagra 50 mg prezzo in farmacia
viagra generico recensioni: Farma Sild Italy – pillole per erezione immediata
http://farmasilditaly.com/# viagra 100 mg prezzo in farmacia
Farmacie on line spedizione gratuita
Бесплатные промокоды https://playpromocode.com/dota2/tastydrop/ для ваших любимых игр! Получайте монеты, бустеры, скины и другие ценные награды. Мы собираем только проверенные коды и обновляем их каждый день.
sex nhật hiếp dâm trẻ em ấu dâm buôn bán vũ khí ma túy bán súng sextoy chơi đĩ sex bạo lực sex học đường tội phạm tình dục chơi les đĩ đực người mẫu bán dâm
Хотите проверить компанию https://innproverka.ru по ИНН? Наш сервис поможет узнать подробную информацию о юридических лицах и ИП: статус, финансы, руководителей и возможные риски. Защищайте себя от ненадежных партнеров!
https://nsqbs53sdbkl11.ru/
https://nsqbs53sdbkl11.ru/
viagra acquisto in contrassegno in italia: FarmaSildItaly – pillole per erezione in farmacia senza ricetta
п»їFarmacia online migliore
Недвижимость на Северном Кипре https://iberiaproperty.ru выгодные инвестиции и комфортная жизнь у моря. Апартаменты, виллы и пентхаусы по доступным ценам. Поможем выбрать лучший вариант и оформить покупку.
удобный маркетплейс blacksprut с высоким уровнем анонимности и надежной системой защиты. Интуитивный интерфейс, проверенные продавцы и безопасные сделки делают его лучшим выбором для покупок.
dark markets 2022 darknet market
drug markets dark web https://github.com/darknetmarkets24/darknet-markets – dark market 2022
darkweb marketplace darkmarket link
tor markets 2022 tor marketplace
https://farmatadalitaly.shop/# comprare farmaci online all’estero
farmacia online
Раскрутка в соцсетях https://nakrytka.com без лишних затрат! Привлекаем реальную аудиторию, повышаем охваты и активность. Эффективные инструменты для роста вашего бренда.
Farmacie online sicure: Ibuprofene 600 prezzo senza ricetta – Farmacia online piГ№ conveniente
migliori farmacie online 2024
farmacia online BRUFEN 600 acquisto online farmacia online senza ricetta
drug markets dark web dark markets 2022
darknet market list https://github.com/darknetmarkets24/darknet-markets dark web drug marketplace
dark markets darknet sites
https://farmaprodotti.com/# farmaci senza ricetta elenco
farmacie online affidabili
acquisto farmaci con ricetta: BRUFEN 600 acquisto online – acquisto farmaci con ricetta
Hi there! This post couldn’t be written any better! Reading through this article reminds me of my previous roommate! He always kept talking about this. I will send this post to him. Pretty sure he’s going to have a very good read. I appreciate you for sharing!
farmacia online senza ricetta: Farma Brufen – Farmacia online miglior prezzo
farmacie online autorizzate elenco
Hey there just wanted to give you a quick heads up and let you know a few of the images aren’t loading correctly. I’m not sure why but I think its a linking issue. I’ve tried it in two different web browsers and both show the same outcome.
https://farmasilditaly.shop/# viagra originale recensioni
comprare farmaci online all’estero
comprare farmaci online con ricetta: BRUFEN prezzo – farmacie online autorizzate elenco
After looking at a number of the blog posts on your site, I honestly appreciate your technique of blogging. I book-marked it to my bookmark webpage list and will be checking back soon. Please check out my web site too and let me know your opinion.
Excellent article. I thought the content very beneficial. Appreciated the way you detailed everything.
увлекательный сериал сериал однажды в сказке о жизни сказочных персонажей в реальном мире. Интригующий сюжет, волшебные события и неожиданные тайны. Смотрите онлайн в высоком качестве прямо сейчас!
dark web drug marketplace dark web market
dark market list https://github.com/darknetmarkets24/darknet-markets tor darknet
bitcoin dark web darkmarket list
viagra generico recensioni: Farma Sild Italy – viagra cosa serve
comprare farmaci online con ricetta
farmacie online autorizzate elenco Farma Brufen Farmacie on line spedizione gratuita
http://farmatadalitaly.com/# acquistare farmaci senza ricetta
comprare farmaci online all’estero
viagra naturale: FarmaSildItaly – viagra originale in 24 ore contrassegno
Very nice post. I absolutely appreciate this site. Keep it up!
farmacie online autorizzate elenco: farmacia online senza ricetta – top farmacia online
migliori farmacie online 2024
tor darknet https://github.com/darknetmarkets24/darknet-markets – darknet drug market
darknet market tor darknet
dark markets https://github.com/darknetmarkets24/darknet-markets best darknet markets
https://farmatadalitaly.com/# п»їFarmacia online migliore
Farmacie on line spedizione gratuita
https://vip-parisescort.com/
таможенное оформление услуги цена https://bvs-logistica.com/tamozhennnoe-oformlenie.html
comprare farmaci online con ricetta: Farm Tadal Italy – farmacie online autorizzate elenco
п»їFarmacia online migliore
escort paris
Farmacia online miglior prezzo Farma Prodotti Farmacia online piГ№ conveniente
Интернет-магазин товаров https://vitasleep.ru для здорового сна. В ассортименте: ортопедические матрасы, подушки, одеяла, постельное белье и аксессуары от проверенных брендов. Удобный выбор, доставка по России, гарантия качества. Забота о вашем комфорте и здоровом сне!
https://gruzoperevozki-minsk24.ru/
http://farmasilditaly.com/# farmacia senza ricetta recensioni
acquisto farmaci con ricetta
onion market https://github.com/darknetmarkets24/darknet-markets – darknet drug store
dark web market list darkmarkets
darkweb marketplace darknet drug links
tor market url deep dark web
Farmacie online sicure: Farma Prodotti – farmacie online affidabili
So an enlightening article! I picked up plenty from perusing it. The information is very arranged and straightforward to follow.
Farmacia online miglior prezzo: Farmacia online miglior prezzo – acquistare farmaci senza ricetta
farmacie online sicure
смотреть сериал сезон все серии lordseriall.org
смотреть бесплатно сериалы http://lordserial4.top
смотреть сериалы без рекламы https://lordserials2.net
https://farmasilditaly.com/# viagra consegna in 24 ore pagamento alla consegna
Farmacia online piГ№ conveniente
darknet drug links darknet site
darknet drug market https://github.com/darknetmarkets24/darknet-markets – deep web markets
comprare farmaci online all’estero: Ibuprofene 600 prezzo senza ricetta – migliori farmacie online 2024
deep web drug markets darkweb marketplace
смотреть сериалы онлайн без рекламы https://lordserial7.com
смотреть сериалы 2024 в хорошем качестве https://lordserials2.net
сериал онлайн бесплатно серии lordserials.cc
comprare farmaci online con ricetta: FarmaBrufen – acquisto farmaci con ricetta
Farmacia online miglior prezzo
farmacia online piГ№ conveniente BRUFEN 600 acquisto online comprare farmaci online con ricetta
This article is extremely enlightening. I really appreciated reading it. The information is highly well-organized and easy to understand.
https://farmatadalitaly.shop/# farmaci senza ricetta elenco
farmacia online
cialis farmacia senza ricetta: Farma Sild Italy – kamagra senza ricetta in farmacia
I was skeptical about installing Metamask until I found https://sites.google.com/view/metamask-extension-dfkasdkfdnt/download. Their guides are thorough and trustworthy, making it easy for me to secure my digital assets with confidence. Definitely recommend!
dark web sites links darkmarket link
dark markets 2022 https://github.com/darknetmarkets24/darknet-markets – tor dark web
darknet market links dark market
dark web drug marketplace dark websites
https://gruzoperevozki-minsk24.ru/
acquistare farmaci senza ricetta: Farma Prodotti – migliori farmacie online 2024
Farmacia online piГ№ conveniente
After going over a handful of the blog articles on your blog, I seriously like your technique of blogging. I added it to my bookmark website list and will be checking back soon. Please check out my website as well and let me know what you think.
farmaci senza ricetta elenco: Ibuprofene 600 prezzo senza ricetta – farmacie online affidabili
Логистические услуги в Москве https://bvs-logistica.com доставка, хранение, грузоперевозки. Надежные решения для бизнеса и частных клиентов. Оптимизация маршрутов, складские услуги и полный контроль на всех этапах.
смотреть сериалы 2025 https://lordserialss.life
смотреть сериал качестве бесплатно https://lordsserial.xyz
https://farmaprodotti.com/# farmacia online piГ№ conveniente
farmacia online senza ricetta
dark web markets darkmarket
darknet drug store https://github.com/darknetmarkets24/darknet-markets – darknet market
darknet sites dark market onion
dark websites darknet drug market
Fantastic post! The information you shared is really valuable and well-explained. Thanks for putting this together!
Hello! I could have sworn I’ve been to your blog before but after browsing through many of the articles I realized it’s new to me. Regardless, I’m certainly happy I came across it and I’ll be book-marking it and checking back frequently.
Хотите почувствовать азарт? arkada casino играть предлагает широкий выбор игр, честную систему выигрышей и мгновенные выплаты. Захватывающие слоты и бонусы ждут вас!
http://phtaya.tech/# Many casinos host charity events and fundraisers.
Gambling can be a social activity here.
dark web market links darknet drug market deep web sites
Los casinos organizan eventos especiales regularmente.: winchile.pro – win chile
Security measures ensure a safe environment.: phtaya – phtaya.tech
taya365 login taya365.art The casino experience is memorable and unique.
tor marketplace dark web market list darknet market list
High rollers receive exclusive treatment and bonuses. https://winchile.pro/# Las promociones atraen nuevos jugadores diariamente.
http://phmacao.life/# Loyalty programs reward regular customers generously.
Live music events often accompany gaming nights.
Bioplastics are made from biological material instead of from fossil fuels, and so they’re supposed to have very different properties from traditional plastics.
лучшие сериалы онлайн https://lordseriall6.org
смотреть лучшие сериалы все сезоны смотреть сериалы в онлайн бесплатно в хорошем качестве
сериалы 2022 онлайн https://lordserial5.pet
darknet links tor marketplace tor markets links
They could have associates to refer and they could direct you to potential angel buyers.
Up entrance, the beaklike nose was dominated by a massive split-grille design with vertical center sections linked to low horizontal extensions that ran out below the quad headlamps to the edges of the automotive.
Aw, this was an extremely nice post. Taking a few minutes and actual effort to generate a superb article… but what can I say… I hesitate a whole lot and never manage to get nearly anything done.
High rollers receive exclusive treatment and bonuses.: taya777.icu – taya777 register login
The sport was drawn after 37 moves, as White could not find a line to play for a win.
What’s the function of Cognitive Behavioral Therapy (CBT) in treating OCD?
Many casinos have beautiful ocean views.: phmacao – phmacao com
tor marketplace deep web markets
darknet market links https://github.com/darknetmarkets24/darknet-markets – dark web sites
darkmarket darknet markets
bitcoin dark web dark markets
They had built trucks before, however greater models and for industry, not regular drivers.
A 160-foot meteorite landed within the northern desert in Arizona about 50,000 years ago, which left an affect crater about 3,900 ft huge (less than a mile) and 570 feet deep.
He tied for 3rd-5th of 7 gamers (3/6) at Stamford 1887, received by Joseph Henry Blake.
dark markets 2025 deep web drug markets darknet seiten
Faculty Soccer Corridor of Fame.
In order to illustrate ineffective allocation of the resources which had led to institutional issues one can utilize two examples.
On a Christmas Eve, way back, a poor little boy went to church in great sadness as a result of he had no gift to convey the Holy Child.
With regard to the general marketplace Nottingham, like the remainder of the UK experienced a drop in house costs with the monetary crisis, however the relative closeness of Nottingham to London and all the development in the city has ensured Nottingham is an efficient location to dwell and so the market has remained lively.
https://taya365.art/# Gambling can be a social activity here.
Casinos often host special holiday promotions.
Монтаж плоской кровли с гарантией до 20 лет, проверенные материалы, идеальные швы https://ploskaya-krovli-zagorodnyh-domov.ru/
Casino promotions draw in new players frequently. http://jugabet.xyz/# Las apuestas deportivas tambiГ©n son populares.
Instead, ultrashort bond funds typically invest in riskier securities in order to increase their return.
It taught us something important, if uncomfortable, about our state of knowledge of modern financial markets.
darkmarkets deep web sites dark market list
taya365 login taya365.art Casino promotions draw in new players frequently.
Los jugadores pueden disfrutar desde casa.: jugabet casino – jugabet
darknet websites https://github.com/darknetmarkets24/darknet-markets – darkmarket
darkmarket https://github.com/darknetmarkets24/darknet-markets onion market
dark web market list bitcoin dark web
dark markets darknet markets
The Philippines offers a rich gaming culture.: taya365 – taya365
https://taya777.icu/# Responsible gaming initiatives are promoted actively.
Gambling regulations are strictly enforced in casinos.
deep web links dark markets tor marketplace
Check out Sellvia on Instagram for the hottest product ideas, store upgrades, and exclusive deals! Stay in the loop with our latest dropshipping tips and grab promo coupons to boost your business.
Players often share tips and strategies. https://phmacao.life/# Visitors come from around the world to play.
darkmarket link blackweb official website deep web drug markets
The casino experience is memorable and unique.: phtaya.tech – phtaya
onion market https://github.com/darknetmarkets24/darknet-markets – tor dark web
darkmarket link darknet market
dark web market list https://github.com/darknetmarkets24/darknet-markets darkmarket link
https://taya777.icu/# Players enjoy both fun and excitement in casinos.
The casino scene is constantly evolving.
best darknet markets dark web sites links
dark web sites links deep web markets
Many casinos provide shuttle services for guests.: phmacao casino – phmacao com
Где заказать монтаж плоской крыши, нужен надежный и ответственный подрядчик https://ploskaya-krovli-zagorodnyh-domov.ru/
Players can enjoy high-stakes betting options. http://taya365.art/# Visitors come from around the world to play.
jugabet jugabet casino Las aplicaciones mГіviles permiten jugar en cualquier lugar.
darkmarkets https://github.com/darknetmarkets24/darknet-markets – darknet market list
dark web markets dark web sites links
darkmarket list https://github.com/darknetmarkets24/darknet-markets dark market url
http://taya365.art/# Slot machines feature various exciting themes.
Casinos often host special holiday promotions.
dark web markets dark market 2022
darknet markets dark market url
Downloading Metamask on Chrome was a challenge until I found https://sites.google.com/view/metamask-extension-download-oa/chrome. The clear and simple steps helped me install it without any issues. I love how informative the site is for crypto users!
Promotions are advertised through social media channels.: phmacao – phmacao.life
A variety of gaming options cater to everyone.: taya777 login – taya777 app
I would like to thank you for the efforts you have put in writing this site. I am hoping to view the same high-grade content from you in the future as well. In truth, your creative writing abilities has encouraged me to get my own blog now 😉
dark websites https://github.com/darknetmarkets24/darknet-markets – darkmarket
У этой фирмы большой опыт в ремонте кондиционеров, ознакомьтесь с предложениями, здесь https://www.mixcloud.com/Coolstandart/
dark markets 2022 deep web markets
http://phmacao.life/# Gaming regulations are overseen by PAGCOR.
The casino scene is constantly evolving.
darkmarket link https://github.com/darknetmarkets24/darknet-markets dark web market links
Casinos often host special holiday promotions. https://phmacao.life/# The casino atmosphere is thrilling and energetic.
darkmarket darknet market list
Many casinos host charity events and fundraisers.: phmacao – phmacao
Loyalty programs reward regular customers generously.: taya365 login – taya365
Инвестируйте в себя с умом: премиальные курсы со скидкой до 99%. Детали по ссылке https://500px.com/p/vadim998?view=photos
onion market https://github.com/darknetmarkets24/darknet-markets – darknet marketplace
dark web link dark market url
drug markets onion tor market url
darkmarkets https://github.com/darknetmarkets24/darknet-markets dark web sites links
http://taya365.art/# Slot tournaments create friendly competitions among players.
The poker community is very active here.
darknet sites darknet drug market
phmacao casino phmacao.life Poker rooms host exciting tournaments regularly.
Pretty! This was an extremely wonderful post. Thank you for supplying these details.
LTrent Driving School has served many families through multiple generations to ensure that they are equipped to survive on the road.
Casino visits are a popular tourist attraction. http://winchile.pro/# Los jugadores deben jugar con responsabilidad.
darkmarket list https://github.com/darknetmarkets24/darknet-markets darkmarket link
drug markets onion deep web sites bitcoin dark web
The full special bip39 Word List consists of 2048 words used to protect cryptocurrency wallets. Allows you to create backups and restore access to digital assets. Check out the full list.
tor marketplace [url=https://github.com/darknetmarkets24/darknet-markets ]tor market links [/url]
dark web sites tor markets
dark web links deep web drug markets
dark markets dark market
Manila is home to many large casinos.: taya365 login – taya365 login
zakau6
dark markets 2022 https://github.com/darknetmarkets24/darknet-markets darkmarket
http://phtaya.tech/# Entertainment shows are common in casinos.
Many casinos host charity events and fundraisers.
La seguridad es prioridad en los casinos.: winchile – win chile
darkmarket list https://github.com/darknetmarkets24/darknet-markets dark web market links
Reliable and unique bip39 Word List contains 2048 words needed to create seed phrases in crypto wallets. Allows you to safely manage private keys and guarantees the possibility of recovering funds.
I’m impressed, I must say. Rarely do I encounter a blog that’s equally educative and amusing, and without a doubt, you have hit the nail on the head. The issue is an issue that too few men and women are speaking intelligently about. I am very happy that I stumbled across this during my hunt for something regarding this.
Responsible gaming initiatives are promoted actively. https://taya365.art/# Players enjoy both fun and excitement in casinos.
deep dark web https://github.com/darknetmarkets24/darknet-markets – dark market 2022
tor market darknet websites
deep web drug links https://github.com/darknetmarkets24/darknet-markets dark net
http://taya365.art/# The poker community is very active here.
Responsible gaming initiatives are promoted actively.
Slot machines feature various exciting themes.: phtaya – phtaya login
taya777 register login taya777 app Live dealer games enhance the casino experience.
Las promociones atraen nuevos jugadores diariamente.: jugabet casino – jugabet chile
darknet websites dark markets 2022
dark market link darkmarket 2022
Reliable and unique bip39 Word List contains 2048 words needed to create seed phrases in crypto wallets. Allows you to safely manage private keys and guarantees the possibility of recovering funds.
Cashless gaming options are becoming popular. http://phmacao.life/# Online gaming is also growing in popularity.
http://taya365.art/# Many casinos provide shuttle services for guests.
Casino visits are a popular tourist attraction.
darknet marketplace https://github.com/darknetmarkets24/darknet-markets dark market link
Most casinos offer convenient transportation options.: phmacao.life – phmacao club
thc vape in prague https://sale-weed-prague.com
darknet drug market https://github.com/darknetmarketslinks/darknetmarketlinks – darknet drug market tor markets
Cashless gaming options are becoming popular.: phtaya.tech – phtaya casino
thc gummies delivery in prague marijuana delivery in Prague
dark web market links dark web market list
darkmarket url dark web markets
tor markets https://github.com/darknetmarkets24/darknet-markets – darkmarket url
http://jugabet.xyz/# Las estrategias son clave en los juegos.
Poker rooms host exciting tournaments regularly.
dark web sites https://github.com/darknetmarketslinks/darknetmarketlinks – blackweb darknet drug market
Online gaming is also growing in popularity. http://jugabet.xyz/# La historia del juego en Chile es rica.
phtaya login phtaya casino The casino experience is memorable and unique.
tor marketplace https://github.com/darknetmarkets24/darknet-markets deep web drug store
Some casinos feature themed gaming areas.: taya365 login – taya365 com login
dark web access https://github.com/darknetmarketslinks/darknetmarketlinks – best darknet markets dark market list
Las redes sociales promocionan eventos de casinos.: jugabet casino – jugabet casino
http://winchile.pro/# La diversiГіn nunca se detiene en los casinos.
The casino industry supports local economies significantly.
deep dark web dark web markets
deep web drug url deep web drug store
dark web sites https://github.com/darknetmarkets24/darknet-markets – tor markets 2022
Reliable and unique bip39 Word List contains 2048 words needed to create seed phrases in crypto wallets. Allows you to safely manage private keys and guarantees the possibility of recovering funds.
I was very pleased to find this web site. I need to to thank you for your time for this wonderful read!! I definitely loved every part of it and I have you book marked to look at new things in your website.
darknet market list https://github.com/darknetmarkets24/darknet-markets tor markets
La seguridad es prioridad en los casinos.: jugabet casino – jugabet
http://phmacao.life/# Responsible gaming initiatives are promoted actively.
The Philippines offers a rich gaming culture.
Many casinos offer luxurious amenities and services.: taya365 login – taya365 com login
tor markets links dark web sites
dark markets 2022 dark market onion
FTP backup capabilities are a critical feature for users who need to ensure the safety and availability of their data. The best FTP client often includes automated backup options, allowing users to schedule regular backups without manual intervention. A fast FTP client is particularly important for businesses and developers who rely on quick file transfers to maintain operational efficiency. Free FTP software has become a popular choice for individuals and small teams, offering robust features without the need for a financial investment. Desktop FTP clients are favored for their reliability and seamless integration with local systems, providing a stable platform for managing files. FTP applications that support secure protocols like SFTP and FTPS are essential for maintaining data integrity during transfers. With its ability to handle a wide range of file transfer tasks, FTP remains a vital tool for professionals and casual users alike. Ftp upload for windows
darknet drug links dark market
1xBet promo code https://sky888.win/step-by-step-guide-to-using-the-1xbet-promo-code-71/ your chance to get bonuses on bets, free bets and exclusive promotions! Enter the code during registration and start playing with an increased deposit.
drug markets onion https://github.com/darknetmarkets24/darknet-markets – darknet site
dark web market list https://github.com/darknetmarketslinks/darknetmarketlinks – darknet websites darknet market links
I need to to thank you for this good read!! I certainly enjoyed every bit of it. I have you book-marked to look at new stuff you post…
taya365 taya365 com login The Philippines offers a rich gaming culture.
http://jugabet.xyz/# Los jugadores pueden disfrutar desde casa.
Online gaming is also growing in popularity.
tor markets links https://github.com/darknetmarkets24/darknet-markets tor dark web
Ремонт компьютеров и ноутбуков https://remcomp89.ru в Новом Уренгое – быстрые и качественные услуги! Диагностика, настройка, замена комплектующих, восстановление данных. Гарантия на работу, доступные цены и выезд мастера!
Las apuestas deportivas tambiГ©n son populares.: winchile.pro – win chile
Los casinos son lugares de reuniГіn social.: jugabet chile – jugabet casino
darknet market lists deep web drug url
darkmarket darkmarket url
https://bip39-phrase.blogspot.com/2025/02/bip39-world-list-2048.html
deep web drug links https://github.com/darknetmarketslinks/darknetmarketlinks – darknet search engine tor markets 2025
dark market 2022 darkmarket
darkmarket link https://github.com/darknetmarkets24/darknet-markets – darknet websites
http://jugabet.xyz/# Los pagos son rГЎpidos y seguros.
The casino atmosphere is thrilling and energetic.
Лучшее казино для аркадных игр | Играйте в эксклюзивные аркады в онлайн казино | Победите в аркадах и станьте миллионером | Увлекательные аркадные игры для всех | Аркадные игры и азарт ждут вас здесь | Играйте в аркадные игры и выигрывайте деньги | Уникальные аркадные игры ждут вас | Азарт и аркады в одном месте | Лучшие аркадные развлечения для вас | Играйте в аркадные игры и выигрывайте деньги | Попробуйте свою удачу в аркадном казино | Побеждайте в аркадных баталиях и зарабатывайте деньги | Испытайте свою удачу в аркадном казино | Играйте в аркады и получайте удовольствие | Аркадные сражения и азарт для настоящих игроков | Увлекательные аркады и возможность заработать деньги
arkada casino онлайн arkada casino бонусы без депозита .
tor darknet dark websites
darknet drug store https://github.com/darknetmarkets24/darknet-markets tor markets 2022
darknet market list https://github.com/darknetmarketslinks/darknetmarketlinks – darknet market lists dark websites
dark market onion dark web market
Используйте актуальный промокод 1xbet и получите увеличенный бонус на первый депозит! Делайте ставки на спорт, играйте в казино и пользуйтесь эксклюзивными предложениями. Легкая регистрация и моментальные выплаты!
Many casinos provide shuttle services for guests.: phmacao.life – phmacao com
Looking for the current spinbetter promo code? Get bonus funds for bets and casino games. Easy activation, favorable conditions and real winnings are waiting for you. Hurry to use it!
darkmarket list https://github.com/darknetmarkets24/darknet-markets – darknet drug market
Manila is home to many large casinos.: taya777 login – taya777 register login
dark markets tor markets 2022
darknet drug links https://github.com/darknetmarkets24/darknet-markets onion market
http://phtaya.tech/# The Philippines offers a rich gaming culture.
The casino industry supports local economies significantly.
dark web link dark markets
Лучшие советы по выбору металлической входной двери, соответствует всем требованиям безопасности.
Где купить надежную входную металлическую дверь по выгодной цене.
дверь металлическая входная цена входная дверь .
Что учесть при выборе входной металлической двери.
Преимущества металлических входных дверей перед другими видами.
Как выбрать между дверью одного бренда и дверью другого.
The most comprehensive bip39 for securely creating and restoring cryptocurrency wallets. Learn how mnemonic coding works and protect your digital assets!
The casino industry supports local economies significantly. http://taya777.icu/# Gaming regulations are overseen by PAGCOR.
phtaya login phtaya The poker community is very active here.
fast airport transfers Prague moving within Czech Republic
blackweb https://github.com/darknetmarketslinks/darknetmarketlinks – the dark internet how to access dark web
darknet site https://github.com/darknetmarkets24/darknet-markets – dark web link
dark markets 2022 darknet site
darknet market links https://github.com/darknetmarkets24/darknet-markets dark market 2022
Casino promotions draw in new players frequently.: taya777 login – taya777
Лучшие советы по выбору металлической входной двери, идеально впишется в интерьер.
Лучшие магазины с широким выбором входных металлических дверей.
заказать входную дверь [url=https://dver-metallicheskaya.ru/]купить входную дверь[/url] .
Что учесть при выборе входной металлической двери.
Преимущества металлических входных дверей перед другими видами.
Как выбрать между дверью одного бренда и дверью другого.
dark web sites links dark market list
The gaming floors are always bustling with excitement.: taya365 com login – taya365 login
tor dark web https://github.com/darknetmarketslinks/darknetmarketlinks – tor markets links darknet drug links
drug markets dark web dark markets
darkmarket https://github.com/darknetmarkets24/darknet-markets tor markets links
http://taya365.art/# Online gaming is also growing in popularity.
Resorts provide both gaming and relaxation options.
Онлайн казино с широким выбором аркадных игр | Играйте в аркадные игры и выигрывайте крупные призы | Победите в аркадах и станьте миллионером | Насладитесь азартом в аркадном казино | Новый уровень азарта в онлайн казино | Играйте в аркадные игры и выигрывайте деньги | Погрузитесь в мир аркадных развлечений и азарта | Играйте в аркады и выигрывайте деньги | Уникальные аркадные развлечения только здесь | Увлекательные аркады для ценителей азарта | Онлайн казино с увлекательными аркадами | Играйте в аркады и выигрывайте крупные суммы | Онлайн казино с самыми популярными аркадами | Новейшие аркадные игры на ваш выбор | Побеждайте в аркадах и получайте денежные призы | Увлекательные аркады и возможность заработать деньги
аркада регистрация arkada casino промокод за регистрацию .
dark market list https://github.com/darknetmarkets24/darknet-markets – dark web market list
bip39
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
drug markets onion darknet market lists
deep web drug url https://github.com/darknetmarkets24/darknet-markets dark web market list
Responsible gaming initiatives are promoted actively.: phtaya.tech – phtaya
The most comprehensive bip39 world list for securely creating and restoring cryptocurrency wallets. Learn how mnemonic coding works and protect your digital assets!
moving insurance Prague apartment moving Prague
dark websites https://github.com/darknetmarketslinks/darknetmarketlinks – deep web drug links darkmarket url
dark web market darkmarket url
darknet site https://github.com/darknetmarkets24/darknet-markets – deep web drug url
https://taya365.art/# Entertainment shows are common in casinos.
Gambling regulations are strictly enforced in casinos.
darkmarket https://github.com/darknetmarkets24/darknet-markets darkmarket 2022
https://telegra.ph/Mobile-Gambling-Development-Trends-and-Game-Optimization-for-Smartphones-01-26
Современная автоматика для жалюзи, сделает ваш дом уютнее.
Снижайте затраты на отопление и кондиционирование воздуха с автоматизацией жалюзи.
Управляйте жалюзи из любой точки мира.
Повысьте уровень безопасности с автоматическими жалюзи.
Качественное обслуживание автоматизированных жалюзи.
жалюзи роллеты автоматика https://elektrokarniz18.ru/ .
tor darknet tor market
https://telegra.ph/Mobile-Gambling-Development-Trends-and-Game-Optimization-for-Smartphones-01-26
Los jackpots progresivos atraen a los jugadores.: jugabet.xyz – jugabet
deep web drug markets https://github.com/darknetmarketslinks/darknetmarketlinks – tor markets links how to access dark web
phmacao com login phmacao.life The Philippines has a vibrant nightlife scene.
drug markets onion https://github.com/darknetmarkets24/darknet-markets tor darknet
darknet site tor markets
best darknet markets https://github.com/darknetmarkets24/darknet-markets – onion market
https://phtaya.tech/# Live dealer games enhance the casino experience.
Players can enjoy high-stakes betting options.
Game rules can vary between casinos.: taya777 – taya777 app
dark web links darkmarket 2022
darknet marketplace https://github.com/darknetmarketslinks/darknetmarketlinks – free dark web dark websites
dark websites https://github.com/darknetmarkets24/darknet-markets dark web drug marketplace
stehovani s durazem na ekologii stehovani plan
Way cool! Some very valid points! I appreciate you writing this post and also the rest of the site is extremely good.
Los casinos organizan eventos especiales regularmente.: winchile.pro – winchile casino
dark web sites dark web markets
tor darknet tor markets 2022
tor market https://github.com/darknetmarketslinks/darknetmarketlinks – darknet market lists deep web links
dark market 2022 https://github.com/darknetmarkets24/darknet-markets – tor dark web
darknet market https://github.com/darknetmarkets24/darknet-markets dark market
https://phmacao.life/# The Philippines offers a rich gaming culture.
Slot machines feature various exciting themes.
Заказать подарок мужчине на день рождения и необычные гаджеты для мужчин в подарок в Суздале. Что подарить мужчине На день рождения 25 лет оригинальное и оригинальные подарки На день рождения женщине 50 в Тамбове. Подарочная ручка для мужчин в футляре и сувениры на 23 февраля недорого в Суздале. Упаковочный Материал для техники и стандартный размер пакета в Новокузнецке. Что можно подарить мужчине на 65 летие и подарочный набор чая для мужчины на день рождения – https://ryukzaki-msk-1.ru/
Цікавлять новобудови Україна? Сучасні квартири з панорамними вікнами, зачиненими дворами та зручним розташуванням. Вибирайте комфортне житло з найкращими умовами покупки!
Идеи для подарков на день рождения мужчине и брелок для мужчины в подарок в Якутске. Сувенирные ключики и подарки На день рождения мужчинам прикольные в Вологде. Наборы для мужчин в подарок кофейные и подарки подросткам на 23 февраля в Казани. Пакеты Маленькие полиэтиленовые купить для подарков и коробочка с подарками в Таганроге. Подарок для любимого мужчины с символикой цска и что подарить мужчине на день рождения у которого все есть https://ryukzaki-msk-1.ru/
dark market onion dark market link
Останні актуальні новини світу 2025 цілодобово оперативні події, важливі рішення, міжнародна політика та економіка. Все, що потрібно знати про життя країни, в одному місці!
darknet market lists deep web drug store
dark web market links https://github.com/darknetmarketslinks/darknetmarketlinks – deep web drug url dark market link
Loyalty programs reward regular customers generously.: taya777 app – taya777 login
dark market list https://github.com/darknetmarkets24/darknet-markets darknet drug store
Live dealer games enhance the casino experience. https://phmacao.life/# Many casinos host charity events and fundraisers.
There’s certainly a great deal to know about this issue. I like all the points you have made.
deep web drug links https://github.com/darknetmarkets24/darknet-markets – deep web drug store
dark market 2022 tor market
Los jugadores pueden disfrutar desde casa.: winchile.pro – winchile
tor darknet https://github.com/darknetmarketslinks/darknetmarketlinks – dark internet deep dark web
darknet drug market https://github.com/darknetmarkets24/darknet-markets darknet drug links
darknet drug store deep web drug links
taya777 register login taya777 The casino experience is memorable and unique.
https://taya365.art/# Resorts provide both gaming and relaxation options.
The Philippines offers a rich gaming culture.
Продажа инструментов для дома http://profimaster58.ru строительства и ремонта! Огромный выбор ручного и электроинструмента, выгодные цены, акции и быстрая доставка. Найдите все необходимое в одном месте!
Free and reliable ai nudify tool to create images with AI? The Best Free AI Nudify is the best choice for creating nude photos with privacy and quality guarantee.
tor markets dark market
deep web drug url https://github.com/darknetmarketslinks/darknetmarketlinks – the dark internet dark markets 2025
tor market https://github.com/darknetmarkets24/darknet-markets – dark web sites links
dark market link https://github.com/darknetmarkets24/darknet-markets tor market links
The thrill of winning keeps players engaged.: phmacao casino – phmacao
darknet markets dark web market list
грузчики челябинск на час грузчики челябинск на час недорого
dark web market links drug markets onion
Use the proven bip39 standard to protect your assets and easily restore access to your finances. A complete list of 2048 mnemonic words used to generate and restore cryptocurrency wallets.
dark website https://github.com/darknetmarketslinks/darknetmarketlinks – dark web drug marketplace deep web markets
deep dark web https://github.com/darknetmarkets24/darknet-markets deep web markets
https://phtaya.tech/# Players must be at least 21 years old.
The poker community is very active here.
darknet market lists https://github.com/darknetmarkets24/darknet-markets – darkmarket 2022
Casinos offer delicious dining options on-site.: phtaya casino – phtaya login
darknet markets deep web drug markets
darkmarket tor market
drug markets dark web https://github.com/darknetmarketslinks/darknetmarketlinks – darknet market list how to get on dark web
dark web market links https://github.com/darknetmarkets24/darknet-markets deep web markets
tor market links https://github.com/darknetmarkets24/darknet-markets – dark web market links
La variedad de juegos es impresionante.: winchile – winchile casino
darkmarket list darkmarket
drug markets dark web dark markets 2022
http://winchile.pro/# Los casinos ofrecen entretenimiento en vivo.
Game rules can vary between casinos.
how to get on dark web https://github.com/darknetmarketslinks/darknetmarketlinks – dark market list deep web links
darkmarket 2022 https://github.com/darknetmarkets24/darknet-markets dark web market
deep web drug links https://github.com/darknetmarkets24/darknet-markets – darknet market lists
Betflix285 Hello, I am an online gambler and would like to recommend a good, reliable website. Really pay every withdrawal amount. Plus a stable game system No lag, no freezes. Good quality website, high security, no cheating, definitely no user lock. If interested, come and try playing. New members receive double profits.
phmacao com login phmacao com Some casinos feature themed gaming areas.
Slot machines attract players with big jackpots.: taya365 login – taya365 login
darkmarket link darknet market list
deep web drug links dark web link
darknet websites https://github.com/darknetmarketslinks/darknetmarketlinks – blackweb the dark internet
Desde 2019, a Mostbet Portugal tem se consolidado como uma excelente escolha para os jogadores portugueses que buscam formas seguras e divertidas de apostar e jogar nos casinos online e ao vivo. Com uma ampla seleção de jogos, apostas esportivas, esports e apostas em esportes virtuais, a plataforma oferece um catálogo premium de uma marca licenciada e confiável. Confiança, inteligência e lealdade são os pilares que sustentam a Mostbet Casino, que ainda proporciona bônus e promoções exclusivas, métodos de pagamento locais reconhecidos e ferramentas para um jogo responsável: nekhuy pizdit chuzhyye sayty
The casino industry supports local economies significantly. https://winchile.pro/# Las redes sociales promocionan eventos de casinos.
dark web market links https://github.com/darknetmarkets24/darknet-markets tor market url
drug markets dark web https://github.com/darknetmarkets24/darknet-markets – darknet markets
п»їCasinos in the Philippines are highly popular.: taya777.icu – taya777 app
tor market dark market
Desde 2019, a Mostbet Portugal tem se consolidado como uma excelente escolha para os jogadores portugueses que buscam formas seguras e divertidas de apostar e jogar nos casinos online e ao vivo. Com uma ampla seleção de jogos, apostas esportivas, esports e apostas em esportes virtuais, a plataforma oferece um catálogo premium de uma marca licenciada e confiável. Confiança, inteligência e lealdade são os pilares que sustentam a Mostbet Casino, que ainda proporciona bônus e promoções exclusivas, métodos de pagamento locais reconhecidos e ferramentas para um jogo responsável: SodaSEO pidorasy
https://taya777.icu/# The thrill of winning keeps players engaged.
Security measures ensure a safe environment.
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
Sitio web oficial jude-bellingham.com.mx de fans de Jude Bellingham: noticias, logros y material exclusivo sobre la carrera del talentoso mediocampista que juega en el Real Madrid.
darknet market list darknet market links
deep web drug markets best darknet markets
Sitio web de fans https://rodri.com.mx de Rodri Hernandez: Descubre la carrera y logros del mediocampista espanol del Manchester City. Noticias, estadisticas y analisis del juego de uno de los mejores futbolistas actuales.
dark market onion https://github.com/darknetmarketslinks/darknetmarketlinks – darkmarket 2025 tor dark web
dark websites https://github.com/darknetmarkets24/darknet-markets dark web links
darknet site https://github.com/darknetmarkets24/darknet-markets – drug markets dark web
deep web drug url darknet drug store
Resorts provide both gaming and relaxation options.: taya777 login – taya777.icu
Kevin De Bruyne kevin de bruyne es un maestro del futbol moderno, conocido por su vision de juego, precision y liderazgo en el Manchester City. Su talento y trabajo duro lo han convertido en una leyenda del deporte.
darknet marketplace dark market link
Sitio fan de Mohamed Salah mohamed-salah ultimas noticias, records, entrevistas y los mejores momentos de la carrera de uno de los futbolistas mas grandes de la actualidad. ?Mantente al tanto!
darknet markets 2025 https://github.com/darknetmarketslinks/darknetmarketlinks – dark web access dark website
darkmarket 2022 https://github.com/darknetmarkets24/darknet-markets darkmarkets
dark web links https://github.com/darknetmarkets24/darknet-markets – dark market list
dark websites https://github.com/darknetmarketslinks/darknetmarketlinks – darkmarket 2025 the dark internet
dark market dark markets 2022
dark web market links https://github.com/darkwebmarketslinks/darkwebmarkets – dark web site dark market link
dark market 2022 dark web market
Fan site de Vinicius Junior https://vinicius-jr.com.mx noticias, logros y detalles sobre su carrera en el Real Madrid. Sigue la evolucion de esta estrella del futbol mundial.
dark web sites links https://github.com/darknetmarketslinks/darknetmarketlinks – darknet websites darknet links
casino la riviera en ligne meilleur site de casino en ligne
darknet sites https://github.com/darknetmarkets24/darknet-markets tor darknet
darknet marketplace https://github.com/darknetmarkets24/darknet-markets – dark markets 2022
no prescription needed pharmacy http://megaindiapharm.com/# MegaIndiaPharm
cheapest pharmacy for prescriptions https://easycanadianpharm.shop/# canadian pharmacy world
tor dark web darknet markets
how to access dark web https://github.com/darknetmarketslinks/darknetmarketlinks – dark web market list darknet drug store
MegaIndiaPharm: Mega India Pharm – india pharmacy mail order
darknet market list https://github.com/darkwebwebsites/darkwebwebsites – darkmarket link dark internet
darkmarket list onion market
I was very happy to discover this page. I want to to thank you for your time due to this wonderful read!! I definitely liked every bit of it and i also have you bookmarked to look at new information in your site.
canadian pharmacy without prescription discount drug mart pharmacy drugmart
xxl mexican pharm: mexican rx online – mexico drug stores pharmacies
dark web sites links https://github.com/darknetmarkets24/darknet-markets deep dark web
dark web markets https://github.com/darknetmarkets24/darknet-markets – darknet websites
darkmarket url tor dark web
tor dark web https://github.com/darknetmarketslinks/darknetmarketlinks – dark website best darknet markets
tor markets links dark market
best darknet markets https://github.com/darknetmarkets2025/darknetmarketlinks – dark internet tor darknet
deep web search https://github.com/darkwebmarketslinks/darkwebmarkets – bitcoin dark web darknet market lists
canada drugs coupon code http://easycanadianpharm.com/# easy canadian pharm
Try your luck at pinup casino! The best slots, roulette, blackjack and live games with real dealers. Pleasant bonuses, promotions and a user-friendly interface will create ideal conditions for the game!
dark web links https://github.com/darknetmarkets24/darknet-markets dark websites
val2i4
dark markets https://github.com/darknetmarkets24/darknet-markets – dark web market links
canadian pharmacy no prescription needed https://easycanadianpharm.shop/# canada discount pharmacy
tor market links https://github.com/darknetmarketslinks/darknetmarketlinks – dark web links tor darknet
Почта для домена на https://email4domain.ru это корпоративный почтовый сервис email для организаций. Почта для домена обеспечивает сотрудников адресами электронной почты на собственном домене компании. Почта для бизнеса улучшает узнаваемость и повышает имидж бренда.
dark web drug marketplace dark web link
the dark internet https://github.com/darknetmarketslinks/darknetmarketlinks – dark market list dark market onion
offshore pharmacy no prescription: Best online pharmacy – best canadian pharmacy no prescription
darkmarket link dark web sites links
drug markets onion https://github.com/darknetmarkets2025/darknetmarketlinks – deep web sites tor markets links
discount drug mart pharmacy: reputable online pharmacy no prescription – drugmart
darkmarket https://github.com/darkwebmarketslinks/darkwebmarkets – tor marketplace onion market
New full bip39 phrase 2048 words used to create and restore crypto wallets. Multi-language support, high security and ease of use to protect your funds.
Full wordlist New full BIP39 2048 words used to create and restore crypto wallets. Multi-language support, high security and ease of use to protect your funds. 2048 mnemonic words for seed generation.
Идеальный привод для жалюзи.
с применением привода.
Подсказки по выбору и установке привода для жалюзей.
Преимущества автоматизированного привода для жалюзи.
Тенденции в автоматизации жалюзи с помощью привода.
Как управлять жалюзями с помощью смартфона с использованием привода.
Секреты успешной установки привода для автоматизации жалюзей.
Плюсы привода для жалюзи в экономии ресурсов.
Интересные факты о приводах для жалюзи.
Секрет уюта и удобства с автоматизированными жалюзями.
жалюзи автоматическим приводом https://elektrokarniz21.ru/ .
casino belgique en ligne casino en ligne retrait immediat
canadian pharmacies not requiring prescription http://xxlmexicanpharm.com/# xxl mexican pharm
dark market link https://github.com/darknetmarketslinks/darknetmarketlinks – bitcoin dark web darkweb marketplace
deep web drug url https://github.com/darknetmarketslinks/darknetmarketlinks – deep web sites tor darknet
darknet market lists https://github.com/darkwebwebsites/darkwebwebsites – deep web drug markets deep web search
darkweb marketplace https://github.com/darkwebmarketslinks/darkwebmarkets – drug markets dark web tor dark web
canadian pharmacy coupon code https://xxlmexicanpharm.com/# xxl mexican pharm
MegaIndiaPharm MegaIndiaPharm Mega India Pharm
Best online pharmacy: Best online pharmacy – Cheapest online pharmacy
deep web drug markets https://github.com/darknetmarketslinks/darknetmarketlinks – darkmarket link dark web site
dark markets 2025 https://github.com/darknetmarketslinks/darknetmarketlinks – deep web markets darknet market links
global pharmacy canada: canadian king pharmacy – easy canadian pharm
canada pharmacy coupon http://megaindiapharm.com/# indian pharmacy paypal
darknet drug market https://github.com/darknetmarkets2025/darknetmarketlinks – dark markets 2025 dark market
dark web search engine https://github.com/darkwebmarketslinks/darkwebmarkets – dark market 2025 tor dark web
dark markets 2025 https://github.com/darknetmarketslinks/darknetmarketlinks – darknet drug links dark web links
darkmarket list https://github.com/darknetmarketslinks/darknetmarketlinks – darknet drug store dark web search engine
tor market https://github.com/darkwebwebsites/darkwebwebsites – tor market deep web drug links
pharmacy coupons https://easycanadianpharm.com/# best canadian online pharmacy
darknet market https://github.com/darkwebmarketslinks/darkwebmarkets – how to access dark web darknet market links
dark web market https://github.com/darknetmarketslinks/darknetmarketlinks – darkmarket dark market link
darknet drug market https://github.com/darknetmarketslinks/darknetmarketlinks – black internet tor marketplace
buying prescription drugs from canada: family pharmacy – online pharmacy delivery usa
Full wordlist New full BIP39 2048 words used to create and restore crypto wallets. Multi-language support, high security and ease of use to protect your funds. 2048 mnemonic words for seed generation.
bonus sans depot casino en ligne https://annuaire-des-casinos.com
Đăng ký tài khoản mới tại HEN88 để nhận ngay các ưu đãi và khuyến mãi cực hấp dẫn, bao gồm giftcode và các chương trình hoàn tiền. Đây là cơ hội tuyệt vời để bạn gia tăng vốn đầu tư và trải nghiệm dịch vụ Trang chủ : https://hen88.app/
easy canadian pharm: legitimate canadian online pharmacies – easy canadian pharm
Hi there! This blog post couldn’t be written any better! Going through this post reminds me of my previous roommate! He always kept talking about this. I most certainly will send this information to him. Pretty sure he will have a very good read. Many thanks for sharing!
dark web sites https://github.com/darkwebwebsites/darkwebwebsites – drug markets dark web dark market
darknet site https://github.com/darknetmarkets2025/darknetmarketlinks – dark web websites deep web drug store
ucmtje
New full Bip39 2048 words used to create and restore crypto wallets. Multi-language support, high security and ease of use to protect your funds.
darkmarket 2025 https://github.com/darknetmarketslinks/darknetmarketlinks – deep web drug markets darkmarket url
deep web drug url https://github.com/darkwebmarketslinks/darkwebmarkets – darkmarket 2025 darknet links
UID_36274208###
Ini dia info viral link berita dana terkini di indonesia !
dark web link https://github.com/darknetmarketslinks/darknetmarketlinks – dark net how to access dark web
dark website [url=https://github.com/darknetmarkets2025/darknetmarketlinks ]dark market onion [/url] dark web markets
xxl mexican pharm xxl mexican pharm xxl mexican pharm
dark websites https://github.com/darknetmarketslinks/darknetmarketlinks – dark internet how to access dark web
online pharmacy discount code https://easycanadianpharm.com/# canadian online pharmacy
dark web market links https://github.com/darkwebmarketslinks/darkwebmarkets – dark web access darknet links
dark web drug marketplace https://github.com/darknetmarketslinks/darknetmarketlinks – dark web search engine tor darknet
cheapest pharmacy to fill prescriptions without insurance https://easycanadianpharm.com/# thecanadianpharmacy
Best online pharmacy: Best online pharmacy – Best online pharmacy
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
Aw, this was an exceptionally nice post. Taking the time and actual effort to produce a really good article… but what can I say… I procrastinate a whole lot and never manage to get anything done.
darknet market list [url=https://github.com/darkwebwebsites/darkwebwebsites ]the dark internet [/url] tor darknet
darknet marketplace https://github.com/darknetmarkets2025/darknetmarketlinks – dark websites deep web drug url
canada pharmacy reviews: easy canadian pharm – easy canadian pharm
Актуальные промокоды казино https://brandiimage.com/blogs/melbet_registration_promo_code___cash888.html получите дополнительные бонусы при регистрации! Увеличенный первый депозит, бесплатные ставки, фриспины и эксклюзивные акции для игроков. Вводите код и выигрывайте больше!
Промокод казино https://www.globaleconomicsucsb.com/blog/index.php?entryid=263683 активируйте эксклюзивные бонусы! Получите фриспины, бонусные деньги на депозит и кешбэк. Используйте актуальные коды для максимальной выгоды в онлайн-казино. Играйте с лучшими условиями!
darknet markets 2025 https://github.com/darknetmarketslinks/darknetmarketlinks – darknet drug store dark web search engines
Current casino promo codes https://www.solazone.com.au/news/?1xbet_promo_code_bonus_codes.html bonus money, free spins and cashback for playing. Use verified codes, activate exclusive offers and win more!
cm00i8
dark web access https://github.com/darkwebmarketslinks/darkwebmarkets – tor markets tor darknet
tor market links [url=https://github.com/darknetmarketslinks/darknetmarketlinks ]onion market [/url] darkmarket 2025
Ищете выгодные покупки? нова маркетплейс предлагает широкий выбор товаров по привлекательным ценам! Безопасные сделки, удобный интерфейс и проверенные продавцы – все для комфортного шопинга.
dark web links https://github.com/darkwebwebsites/darkwebwebsites – dark markets tor dark web
darkmarket https://github.com/darknetmarkets2025/darknetmarketlinks – dark market link tor market url
deep web sites https://github.com/darknetmarketslinks/darknetmarketlinks – how to get on dark web deep web links
Промокод казино http://www.extreme-centre.com/bin/moya_ughasnaya_nyanya_stoit_li_smotrety_etot_filym.html активируйте эксклюзивные бонусы! Получите фриспины, дополнительные деньги на депозит и кешбэк. Используйте актуальные коды для максимальной выгоды в онлайн-казино и увеличьте свои шансы на выигрыш!
Лучшие промокоды для казино http://lynks.ru/geshi/php/?bonusy_1xbet_promokod_2021_na_segodnya.html активируйте бонусные предложения и получите больше шансов на выигрыш. Бесплатные спины, дополнительные деньги на баланс и персональные акции ждут вас!
drugstore com online pharmacy prescription drugs https://easycanadianpharm.shop/# canada pharmacy
Мировые новости спорта
cheapest pharmacy prescription drugs https://familypharmacy.company/# mail order prescription drugs from canada
darkmarkets https://github.com/darkwebmarketslinks/darkwebmarkets – tor market url darknet drug store
darkmarket https://github.com/darknetmarketslinks/darknetmarketlinks – tor markets 2025 darknet market
ריגושים. כולם יודעים כי מכל הנערות, אלו אשר בחיפה נחשבות לטובות ביותר. יש כאן קהל גדול של גברים הנעזר בשירותיהן, ולכן ישנו דיסקרטיות בקריות זה פינוק לגבר בזכות דירות דיסקרטיות בקריות אתה יכול ליהנות מפינוק עצמתי, משחרר ומרגיע. הדירות מציעות לגבר את more info here
An impressive share! I’ve just forwarded this onto a friend who had been conducting a little research on this. And he in fact bought me lunch simply because I stumbled upon it for him… lol. So allow me to reword this…. Thanks for the meal!! But yeah, thanx for spending some time to discuss this subject here on your blog.
I couldn’t resist commenting. Very well written.
easy canadian pharm: canadianpharmacyworld com – northwest pharmacy canada
dark web drug marketplace https://github.com/darknetmarketslinks/darknetmarketlinks – black internet tor markets 2025
medicine in mexico pharmacies: buying prescription drugs in mexico online – xxl mexican pharm
dark market https://github.com/darknetmarkets2025/darknetmarketlinks – dark web search engine dark web market
Присоединяйтесь к NovaXLtd.live https://novaxltd.live платформе с широкими возможностями и удобными инструментами. Доступность, надежность, поддержка!
Используйте Kra020 актуальная ссылка надежная площадка с удобными инструментами и поддержкой 24/7. Простота и безопасность в одном сервисе!
Откройте новые возможности сайт! Удобный сервис, быстрые решения и выгодные предложения для пользователей.
blackweb official website https://github.com/darknetmarketslinks/darknetmarketlinks – dark net dark web link
dark market link https://github.com/darkwebmarketslinks/darkwebmarkets – darkmarket url darkmarkets
dark markets https://github.com/darkmarketlinkp22jr/darkmarketlink – dark market
dark web links https://github.com/darknetwebsitesgflpx/darknetwebsites – darknet market
online pharmacy non prescription drugs https://discountdrugmart.pro/# discount drug mart pharmacy
deep web drug store https://github.com/darknetdruglinksvojns/darknetdruglinks – darknet market links
dark web link https://github.com/darknetmarketslinks/darknetmarketlinks – darknet drug store deep web links
buy prescription drugs from india MegaIndiaPharm indian pharmacy online
Продажа сигарет сигареты ява купить в интернет-магазине – оригинальные бренды, доступные цены, удобные способы оплаты и быстрая доставка. Сделайте заказ сегодня!
Откройте все возможности Blacksprut Большой выбор товаров, безопасные сделки и простая навигация. Приватность и защита пользователей на первом месте.
tor marketplace https://github.com/darknetmarketlinks2025/darknetmarkets – bitcoin dark web
darknet market list https://github.com/darkwebwebsites/darkwebwebsites – dark market best darknet markets
dark web market https://github.com/tormarkets2025ukaz1/tormarkets2025 – dark markets
dark net https://github.com/darknetmarkets2025/darknetmarketlinks – dark web search engine deep web search
darknet drug store https://github.com/darknetmarketslinks/darknetmarketlinks – dark website darkmarket 2025
dark market https://github.com/darkmarketlinkp22jr/darkmarketlink – darknet markets
non prescription medicine pharmacy http://discountdrugmart.pro/# drug mart
dark web markets https://github.com/darkwebmarketslinks/darkwebmarkets – how to access dark web drug markets dark web
dark web drug marketplace https://github.com/darknetwebsitesgflpx/darknetwebsites – deep web drug links
drug markets dark web https://github.com/darknetdruglinksvojns/darknetdruglinks – darknet market list
dark web link https://github.com/darknetmarketslinks/darknetmarketlinks – darknet drug store darknet site
darkmarket https://github.com/darknetmarketlinks2025/darknetmarkets – deep web markets
darknet site https://github.com/tormarkets2025ukaz1/tormarkets2025 – dark web link
canadian pharmacy online store: canadian pharmacy uk delivery – rate canadian pharmacies
darknet markets https://github.com/darkwebwebsites/darkwebwebsites – dark internet deep web drug markets
tor markets links https://github.com/darknetmarkets2025/darknetmarketlinks – darkmarket 2025 deep web links
canadian pharmacy no prescription https://easycanadianpharm.shop/# canadian pharmacy meds reviews
dark web market https://github.com/darknetmarketslinks/darknetmarketlinks – darkmarkets deep web sites
darknet market lists https://github.com/darkmarketlinkp22jr/darkmarketlink – darkmarket list
tor market https://github.com/darknetwebsitesgflpx/darknetwebsites – tor market
Thanks to https://metanate.org/, I installed the Metamask extension without any trouble. Now I can manage my crypto easily and securely.
tor market url https://github.com/darkwebmarketslinks/darkwebmarkets – dark market onion darkmarket list
tor marketplace https://github.com/darknetdruglinksvojns/darknetdruglinks – dark web sites
dark net https://github.com/darknetmarketslinks/darknetmarketlinks – darknet market darkmarket
darknet market https://github.com/tormarkets2025ukaz1/tormarkets2025 – darknet sites
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
dark market link https://github.com/darkwebwebsites/darkwebwebsites – dark web sites links dark web market list
darkmarket https://github.com/darknetmarkets2025/darknetmarketlinks – dark websites darknet market
darknet site https://github.com/darknetmarketslinks/darknetmarketlinks – darkmarket list deep web drug url
drug markets dark web https://github.com/darkmarketlinkp22jr/darkmarketlink – darkmarket
dark markets 2022 https://github.com/darknetwebsitesgflpx/darknetwebsites – dark markets
tor markets links https://github.com/darkwebmarketslinks/darkwebmarkets – dark web search engines deep web drug store
overseas pharmacy no prescription http://easycanadianpharm.com/# canadian drug prices
dark markets 2022 https://github.com/darknetdruglinksvojns/darknetdruglinks – darknet websites
darkmarket list https://github.com/darknetmarketslinks/darknetmarketlinks – darknet marketplace dark markets
canadian pharmacy no prescription https://xxlmexicanpharm.com/# mexican online pharmacies prescription drugs
darknet site https://github.com/darknetmarketlinks2025/darknetmarkets – darknet drug links
Hello! I just want to give you a big thumbs up for the great info you have right here on this post. I will be returning to your site for more soon.
Hi88 là nền tảng trực tuyến hàng đầu, mang đến trải nghiệm giải trí đỉnh cao với các trò chơi thể thao. Website: https://hi88.delivery/
Ваша сцена станет неповторимой с электрокарнизами, которые удивят зрителей.
Электрокарнизы – стильное решение для сцены, делая представление более динамичным.
Управляйте световыми шоу с помощью электрокарнизов, дарят возможность воплотить любую идею.
Электрокарнизы помогут создать атмосферу шоу, для тех, кто ценит качество и стиль.
Лучшие электрокарнизы для вашего шоу, с непревзойденным качеством и надежностью.
Инновационные электрокарнизы для сцены, и принести вашему проекту новый уровень.
Электрокарнизы – лучший выбор для сцены, с легкой и тихой работой в каждом представлении.
Осуществите свои идеи с помощью электрокарнизов, способных придать умиротворение или напряжение вашему выступлению.
Трансформируйте свой спектакль с электрокарнизами, и подчеркивая профессионализм исполнителей.
Идеальные решения для любого жанра и формата, обеспечив себе идеальный результат в каждом выступлении.
как выбрать электрокарниз для театральных постановок как выбрать электрокарниз для театральных постановок .
onion market https://github.com/darkmarketlinkp22jr/darkmarketlink – tor market
dark market url https://github.com/darknetmarketslinks/darknetmarketlinks – dark web search engines dark market 2025
MegaIndiaPharm: Mega India Pharm – Online medicine home delivery
deep web drug store https://github.com/darknetwebsitesgflpx/darknetwebsites – dark markets 2022
deep web drug links https://github.com/darkwebwebsites/darkwebwebsites – darknet market links dark website
dark market 2025 https://github.com/darknetmarkets2025/darknetmarketlinks – drug markets onion deep web sites
Online medicine home delivery: MegaIndiaPharm – MegaIndiaPharm
dark market url https://github.com/darknetdruglinksvojns/darknetdruglinks – darkweb marketplace
dark web search engine https://github.com/darknetmarketslinks/darknetmarketlinks – darknet marketplace blackweb
dark markets https://github.com/darkwebmarketslinks/darkwebmarkets – dark market dark web sites links
onion market https://github.com/tormarkets2025ukaz1/tormarkets2025 – deep web drug markets
xxl mexican pharm xxl mexican pharm xxl mexican pharm
sex nhật hiếp dâm trẻ em ấu dâm buôn bán vũ khí ma túy bán súng sextoy chơi đĩ sex bạo lực sex học đường tội phạm tình dục chơi les đĩ đực người mẫu bán dâm
dark web market links https://github.com/darkmarketlinkp22jr/darkmarketlink – tor markets
dark web market https://github.com/darknetmarketslinks/darknetmarketlinks – tor market deep dark web
deep web markets https://github.com/darknetwebsitesgflpx/darknetwebsites – dark web market list
canada pharmacy coupon https://discountdrugmart.pro/# online pharmacy without prescription
deep web markets https://github.com/darkwebwebsites/darkwebwebsites – blackweb official website deep web drug store
Свежие промокоды казино http://vavto.su/img/pages/?1xbet_promokod_pri_registracii_bonus_segodnya.html бонусы, фриспины и эксклюзивные акции от топовых платформ! Найдите лучшие предложения, активируйте код и выигрывайте больше.
dark web market list https://github.com/darknetmarkets2025/darknetmarketlinks – dark market dark web markets
darkweb marketplace https://github.com/darknetdruglinksvojns/darknetdruglinks – deep dark web
seo специалист https://seo-base.ru
Нужен опытный лечебный массаж Ивантеевка? Помогаю при остеохондрозе, грыжах, искривлениях позвоночника и болях в суставах. Безопасные техники, профессиональный подход, запись на прием!
darknet market lists https://github.com/darknetmarketslinks/darknetmarketlinks – dark web market dark market list
dark web markets https://github.com/tormarkets2025ukaz1/tormarkets2025 – bitcoin dark web
tor market https://github.com/darkwebmarketslinks/darkwebmarkets – tor market links darkmarket url
us pharmacy no prescription https://xxlmexicanpharm.com/# xxl mexican pharm
darknet sites https://github.com/darkmarketlinkp22jr/darkmarketlink – darkmarket url
dark web market list https://github.com/darknetmarketslinks/darknetmarketlinks – darkmarket link tor darknet
tor market https://github.com/darknetwebsitesgflpx/darknetwebsites – tor market links
mail order pharmacy india: Mega India Pharm – Mega India Pharm
deep web drug links https://github.com/darknetdruglinksvojns/darknetdruglinks – deep web drug store
darknet websites https://github.com/darkwebwebsites/darkwebwebsites – dark market list darkmarket
dark web sites https://github.com/darknetmarkets2025/darknetmarketlinks – tor darknet darknet links
dark market list https://github.com/darknetmarketlinks2025/darknetmarkets – tor market links
deep web drug markets https://github.com/darknetmarketslinks/darknetmarketlinks – tor darknet dark web drug marketplace
us pharmacy no prescription https://megaindiapharm.com/# india pharmacy mail order
darknet markets 2025 https://github.com/darkwebmarketslinks/darkwebmarkets – darknet market lists darknet drug store
Online medicine order: Mega India Pharm – Mega India Pharm
tor markets https://github.com/darkmarketlinkp22jr/darkmarketlink – tor darknet
dark web site https://github.com/darknetmarketslinks/darknetmarketlinks – dark internet dark web search engine
darknet markets https://github.com/darknetwebsitesgflpx/darknetwebsites – dark web links
darknet websites https://github.com/darknetdruglinksvojns/darknetdruglinks – dark web links
tor market https://github.com/tormarkets2025ukaz1/tormarkets2025 – dark market 2022
bitcoin dark web https://github.com/darknetmarketlinks2025/darknetmarkets – tor market links
the dark internet https://github.com/darkwebwebsites/darkwebwebsites – dark market list dark market onion
уборка квартир в москве цены за кв метр
Жарким летним утром Вася Муфлонов, заядлый рыбак из небольшой деревушки, собрал свои снасти и отправился на местное озеро. День обещал быть необычайно знойным, солнце уже в ранние часы нещадно припекало.
Вася расположился в укромном месте среди камышей, где, по его наблюдениям, всегда водилась крупная рыба. Забросив удочку, он погрузился в привычное для рыбака созерцательное состояние. Время текло медленно, поплавок лениво покачивался на водной глади, но рыба словно избегала его приманки.
Ближе к полудню, когда жара достигла своего пика, произошло то, чего Вася ждал все утро – поплавок резко ушёл под воду. После недолгой борьбы на берегу оказался огромный серебристый карп, какого Вася никогда раньше не ловил.
Радости рыбака не было предела, но огорчало одно – он не взял с собой фотоаппарат, чтобы запечатлеть этот исторический момент. Тут в голову Васи пришла необычная идея. Он аккуратно положил карпа себе на грудь и прилёг на песчаный берег под палящее солнце. “Пусть загар оставит память об этом улове”, – подумал находчивый рыбак.
Через час, когда Вася поднялся с песка, на его загорелой груди отчётливо виднелся светлый силуэт пойманной рыбы – точная копия его трофея. Теперь у него было неопровержимое доказательство его рыбацкой удачи.
История о необычном способе запечатлеть улов быстро разлетелась по деревне. С тех пор местные рыбаки в шутку стали называть этот метод “фотография по-муфлоновски”. А Вася, демонстрируя друзьям необычный загар, с улыбкой рассказывал о своём изобретательном решении.
Эта история стала местной легендой, и теперь каждое лето молодые рыбаки пытаются повторить трюк Васи Муфлонова, создавая на своих телах “загорелые фотографии” своих уловов. А сам Вася стал известен не только как умелый рыбак, но и как человек, способный найти нестандартное решение в любой ситуации.
deep web links https://github.com/darknetmarkets2025/darknetmarketlinks – dark web link darknet market list
casino software for sale buy ready-made online casino
dark market url https://github.com/darkmarketlinkp22jr/darkmarketlink – dark web drug marketplace
deep web drug links https://github.com/darkwebmarketslinks/darkwebmarkets – darknet markets dark market 2025
dark web link https://github.com/darknetwebsitesgflpx/darknetwebsites – dark web markets
onion market https://github.com/darknetmarketslinks/darknetmarketlinks – darknet websites tor markets
legal online pharmacy coupon code https://discountdrugmart.pro/# discount drugs
dark web link https://github.com/darknetdruglinksvojns/darknetdruglinks – darknet market list
darkmarket list https://github.com/tormarkets2025ukaz1/tormarkets2025 – tor market links
canadian pharmacy no prescription http://xxlmexicanpharm.com/# best online pharmacies in mexico
tor markets links https://github.com/darknetmarketslinks/darknetmarketlinks – darknet markets dark web search engine
discount drug pharmacy: discount drug pharmacy – drugmart
dark web links https://github.com/darkwebwebsites/darkwebwebsites – tor market tor dark web
deep web drug markets https://github.com/darknetmarkets2025/darknetmarketlinks – dark market darknet drug links
darknet drug links https://github.com/darkmarketlinkp22jr/darkmarketlink – darkweb marketplace
no prescription required pharmacy Best online pharmacy no prescription needed canadian pharmacy
darknet drug store https://github.com/darknetwebsitesgflpx/darknetwebsites – drug markets dark web
darkmarket url https://github.com/darknetmarketslinks/darknetmarketlinks – dark web market deep web markets
darknet sites https://github.com/darkwebmarketslinks/darkwebmarkets – how to get on dark web tor marketplace
Fast and secure VPS https://evps.host/ for any task! Flexible configurations, SSD drives, DDoS protection. Easy scaling, high performance and 24/7 support!
Mega India Pharm: MegaIndiaPharm – MegaIndiaPharm
darknet market lists https://github.com/darknetdruglinksvojns/darknetdruglinks – drug markets onion
darknet market lists [url=https://github.com/tormarkets2025ukaz1/tormarkets2025 ]dark market link [/url]
best darknet markets https://github.com/darknetmarketslinks/darknetmarketlinks – darknet markets 2025 darknet market list
darknet marketplace https://github.com/darkmarketlinkp22jr/darkmarketlink – dark web drug marketplace
dark market 2025 https://github.com/darkwebwebsites/darkwebwebsites – dark website tor markets
tor darknet https://github.com/darknetmarkets2025/darknetmarketlinks – deep web drug url darkweb marketplace
darknet drug store https://github.com/darknetwebsitesgflpx/darknetwebsites – dark web market
All about Karim Benzema karim-benzema biography, achievements, main goals and career moments. Find out how the striker conquered Real Madrid and continues to shine in world football!
All about Karim Benzema https://karim-benzema-bd.com biography, achievements, main goals and career moments. Find out how the striker conquered Real Madrid and continues to shine in world football!
tor market url https://github.com/darknetmarketslinks/darknetmarketlinks – darknet links dark web drug marketplace
pharmacy discount coupons http://xxlmexicanpharm.com/# mexico drug stores pharmacies
darknet search engine https://github.com/darkwebmarketslinks/darkwebmarkets – darknet marketplace deep web markets
darknet market lists https://github.com/darknetdruglinksvojns/darknetdruglinks – tor marketplace
best online pharmacy no prescription https://xxlmexicanpharm.shop/# xxl mexican pharm
dark web sites https://github.com/darknetmarketslinks/darknetmarketlinks – tor dark web darknet sites
deep web drug links https://github.com/darkmarketlinkp22jr/darkmarketlink – deep web markets
foreign pharmacy no prescription: Online pharmacy USA – online pharmacy delivery usa
deep web drug url https://github.com/darknetwebsitesgflpx/darknetwebsites – deep web drug url
best darknet markets [url=https://github.com/darkwebwebsites/darkwebwebsites ]dark market 2025 [/url] darknet drugs
tor darknet https://github.com/darknetmarkets2025/darknetmarketlinks – dark market link dark market list
deep dark web https://github.com/darknetmarketslinks/darknetmarketlinks – tor marketplace dark web drug marketplace
dark websites [url=https://github.com/darkwebmarketslinks/darkwebmarkets ]dark market link [/url] dark web search engines
dark web access https://github.com/darknetmarketslinks/darknetmarketlinks – dark web search engine dark web market links
easy canadian pharm: best rated canadian pharmacy – the canadian pharmacy
cheapest pharmacy to get prescriptions filled https://discountdrugmart.pro/# no prescription needed canadian pharmacy
https://sem-del.ru/
blackweb https://github.com/darkwebwebsites/darkwebwebsites – darknet market lists dark websites
onion market https://github.com/darknetmarkets2025/darknetmarketlinks – darknet market lists tor marketplace
клининг стоимость
canada pharmacy coupon https://xxlmexicanpharm.com/# xxl mexican pharm
deep web drug url https://github.com/darknetmarketslinks/darknetmarketlinks – deep dark web deep web drug store
dark market https://github.com/darkwebmarketslinks/darkwebmarkets – darkmarkets darknet markets
easy canadian pharm easy canadian pharm online canadian drugstore
reputable indian pharmacies: MegaIndiaPharm – Mega India Pharm
I had trouble finding a reliable way to get the Metamask extension, but after visiting https://metamake.org/, everything became so much easier. The site is very informative, and I feel confident using Metamask for my transactions now.
darknet drug store https://github.com/darknetmarketslinks/darknetmarketlinks – deep web drug markets tor darknet
https://antimud.ru/
darkmarket link https://github.com/darkwebwebsites/darkwebwebsites – dark web links darknet links
tor market links https://github.com/darknetmarkets2025/darknetmarketlinks – deep web links blackweb
canadian pharmacy coupon code https://familypharmacy.company/# online pharmacy delivery usa
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
darkmarkets https://github.com/darknetmarketslinks/darknetmarketlinks – deep web markets darknet sites
darknet marketplace https://github.com/darkwebmarketslinks/darkwebmarkets – dark web markets darknet market list
58win là nhà cái trực tuyến hàng đầu tại Việt Nam, mang đến trải nghiệm cá cược độc đáo, đầy hấp dẫn với nhiều trò chơi thú vị và tỷ lệ thắng cao.
аркада фриспины arkada casino бонусы без депозита
Военная служба по контракту https://contract116.ru стабильность, достойная зарплата, социальные льготы и карьерный рост. Присоединяйтесь к профессиональной армии и получите надежное будущее!
Best online pharmacy: Online pharmacy USA – Online pharmacy USA
darknet market lists https://github.com/darknetmarketslinks/darknetmarketlinks – blackweb dark web websites
OKKING nổi lên như một thương hiệu nhà cái đẳng cấp, nơi sở hữu kho tàng trò chơi đa dạng và chất lượng vô đối. Nền tảng luôn đảm bảo mang đến sự hài lòng,
darknet sites https://github.com/darkwebwebsites/darkwebwebsites – dark web search engine dark market url
dark web drug marketplace https://github.com/darknetmarkets2025/darknetmarketlinks – dark web drug marketplace darknet site
tor marketplace https://github.com/darknetmarketslinks/darknetmarketlinks – dark web markets drug markets onion
online pharmacy discount code https://discountdrugmart.pro/# discount drug mart
black internet https://github.com/darkwebmarketslinks/darkwebmarkets – dark web links tor markets 2025
Kevin De Bruyne https://kevin-de-bruyne-az.com is the leader of the Manchester City and Belgium national team midfield. Find out all about his achievements, matches, awards and records in world football!
Joshua Kimmich joshua-kimmich the versatile leader of Bayern and the German national team! The latest news, stats, highlights, goals and assists. Follow the career of one of the best midfielders in the world!
pawno скриптинг samp store
darkmarket link https://github.com/darknetmarketlinks2025/darknetmarkets – tor market
darkmarket link https://github.com/darknetwebsitesgflpx/darknetwebsites – dark markets
canadian pharmacy 24: canadian pharmacies comparison – easy canadian pharm
uk pharmacy no prescription https://familypharmacy.company/# online pharmacy delivery usa
https://чистые-услуги.рф/
dark web websites https://github.com/darkwebwebsites/darkwebwebsites – dark web search engine dark internet
onion market https://github.com/darknetmarketslinks/darknetmarketlinks – dark markets onion market
dark market https://github.com/darknetmarkets2025/darknetmarketlinks – tor market dark web search engine
darkmarket https://github.com/tormarkets2025ukaz1/tormarkets2025 – deep web drug links
deep web sites https://github.com/darkwebmarketslinks/darkwebmarkets – bitcoin dark web deep web markets
tor market https://github.com/darknetwebsitesgflpx/darknetwebsites – dark web market list
darknet market links https://github.com/darknetdruglinksvojns/darknetdruglinks – dark web links
https://itscleaning.ru/
easy canadian pharm: easy canadian pharm – safe canadian pharmacy
tor markets 2025 [url=https://github.com/darknetmarketslinks/darknetmarketlinks ]darkmarket link [/url] dark market url
darkmarket https://github.com/darknetmarkets2025/darknetmarketlinks – darknet site darknet drug links
pharmacy coupons https://discountdrugmart.pro/# discount drug mart pharmacy
darkmarket 2022 https://github.com/tormarkets2025ukaz1/tormarkets2025 – darknet drug store
darkmarket https://github.com/darknetdruglinksvojns/darknetdruglinks – tor markets 2022
tor markets https://github.com/darknetwebsitesgflpx/darknetwebsites – dark web markets
tor dark web https://github.com/darkmarketlinkp22jr/darkmarketlink – dark markets 2022
UID_14309460###
x twitter viral Video Bocor Bulan Sutena
no prescription required pharmacy https://xxlmexicanpharm.com/# mexican rx online
Подарки и сувениры из камня https://kameshki51.ru статуэтки, шкатулки, часы, панно, изделия из мрамора, гранита и оникса. Ручная работа, уникальный дизайн, доставка по России!
darkmarket https://github.com/darkwebmarketslinks/darkwebmarkets – free dark web dark web sites
reputable mexican pharmacies online mexican rx online mexican border pharmacies shipping to usa
Kubet77 là nền tảng trực tuyến chính thức, cung cấp các sản phẩm như game bài, live casino, và slot game. Website: https://kubet77.co.com/
Mega India Pharm: indian pharmacy paypal – indian pharmacy online
dark web markets https://github.com/darknetmarketslinks/darknetmarketlinks – deep web links darknet site
darknet markets 2025 https://github.com/darkwebwebsites/darkwebwebsites – dark market link darknet drug store
You ought to be a part of a contest for one of the most useful blogs on the web. I will recommend this website!
dark market 2025 https://github.com/darknetmarkets2025/darknetmarketlinks – darknet drug links tor marketplace
dark web link https://github.com/darknetmarketlinks2025/darknetmarkets – darknet market lists
darknet sites https://github.com/darknetwebsitesgflpx/darknetwebsites – deep web drug markets
Образовательный портал https://moi-slovari.ru собрание полезных материалов, лекций, статей и справочной информации для школьников, студентов и профессионалов. Учитесь легко и эффективно
Как побороть лудоманию https://teletype.in/@antosha-sevan/moi-opyt-izbavlenia-ot-igrovoi-zavasimosty история глазами прошедшего это испытание и несколько советам тем, кто в середине пути или столкнулся с этим через друзей и близких. Описываю в статье как Вавада помогла мне избавиться от игровой зависимости
dark web sites links https://github.com/darkmarketlinkp22jr/darkmarketlink – tor markets
Can you be more specific about the content of your article? After reading it, I still have some doubts. Hope you can help me.
deep dark web https://github.com/darkwebmarketslinks/darkwebmarkets – best darknet markets tor markets 2025
https://cleanmsk799.ru/
Окунитесь в азарт с http://aviator-slot.ru Уникальная игра с захватывающим геймплеем и возможностью сорвать крупный выигрыш. Следите за коэффициентом, вовремя забирайте ставку и умножайте баланс. Испытайте удачу прямо сейчас!
darknet marketplace https://github.com/darknetmarketslinks/darknetmarketlinks – darknet site darknet drug links
rx pharmacy no prescription http://megaindiapharm.com/# Mega India Pharm
Best online pharmacy: family pharmacy – Cheapest online pharmacy
dark markets https://github.com/darkwebwebsites/darkwebwebsites – dark web links deep web links
Новости музыки Украины https://musicnews.com.ua популярные жанры, тренды и полезные советы для музыкантов. Узнавайте больше о мире музыки и развивайте свои навыки!
deep web links https://github.com/darknetmarkets2025/darknetmarketlinks – darknet drugs tor market url
Ставки на спорт http://betting-ru.ru ваш шанс превратить знания в выигрыш! Лучшие коэффициенты, огромный выбор событий и удобный интерфейс. Делайте прогнозы и побеждайте!
darknet drug market https://github.com/darkwebmarketslinks/darkwebmarkets – darkmarket link tor market links
online pharmacy discount code https://xxlmexicanpharm.shop/# buying prescription drugs in mexico online
blackweb official website https://github.com/darknetmarketslinks/darknetmarketlinks – tor markets tor markets 2025
discount drugs: drug mart – discount drug mart pharmacy
UID_72942561###
Berita Hot! 🔥🔥 Isa Rachmatarwata Tersangka Kasus Jiwasraya Buntut kerugian negara hingga 16,8 Triliun! 😲😲
It’s difficult to find knowledgeable people on this subject, however, you seem like you know what you’re talking about! Thanks
darknet market links deep web drug store dark web market
Hi! Someone in my Facebook group shared this website with us so I came to give it a look. I’m definitely loving the information. I’m bookmarking and will be tweeting this to my followers! Terrific blog and amazing style and design.
This guide was really helpful! I wanted to install the Metamask extension, and https://metaduck.org/ provided the perfect instructions. Now I can manage my crypto assets easily and securely. Highly recommended for beginners and experts alike!
darknet market links dark web market list dark markets
canadian online pharmacy no prescription https://familypharmacy.company/# online pharmacy delivery usa
https://cleanmsk799.ru/
dark web sites links dark market onion onion market
how to access dark web blackweb official website best darknet markets
уборка квартиры в москве
https://itscleaning.ru/
dark web sites links blackweb darkmarket link
https://posle-remonta-uborka.ru/
If you’re looking for a secure and reliable way to download Metamask, I highly recommend checking out https://metapaws.org/. Their detailed guide ensures you install it the right way, without any risks.
family pharmacy: Cheapest online pharmacy – online pharmacy delivery usa
deep web drug markets darknet site the dark internet
п»їbest mexican online pharmacies xxl mexican pharm xxl mexican pharm
darknet seiten deep web search free dark web
darknet marketplace dark market list tor market links
online pharmacy prescription https://discountdrugmart.pro/# drugmart
UID_53550706###
Berita terbaru! 🔥 Isa Rachmatarwata Ditahan Kejagung dalam kasus Jiwasraya. 🚔👮♂️
Greetings! Very useful advice in this particular post! It is the little changes that make the largest changes. Thanks for sharing!
https://posle-remonta-uborka.ru/
drugmart: drug mart – discount drug pharmacy
dark market url dark market list free dark web
https://прочисто.рф/
online pharmacy discount code https://easycanadianpharm.com/# easy canadian pharm
darknet drug market dark markets blackweb official website
dark web websites dark web site darknet links
darknet drugs tor market url the dark internet
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
buying prescription drugs in mexico: xxl mexican pharm – xxl mexican pharm
uk pharmacy no prescription https://discountdrugmart.pro/# discount drug pharmacy
buying prescription drugs from canada https://easycanadianpharm.shop/# easy canadian pharm
https://cleanliness-cleaning.ru/
Zeus vs Hades https://zeus-vs-hades-download.ru эпичная битва богов! Игровой автомат с грозными бонусами, фриспинами и множителями. Выберите сторону Зевса или Аида и сорвите большой выигрыш!
Мир смешанных единоборств ufc ru (MMA) в UFC! Рейтинги, бои, истории бойцов, прогнозы на поединки и эксклюзивные материалы о крупнейшей бойцовской лиге.
Все о легкой атлетике athletics История развития, основные дисциплины, рекорды, тренировки и современные тенденции. Узнайте больше о королеве спорта!
UID_57092237###
Berita gembira! 🎉 Pasokan Gas 3 Kg di Kramat Jati Kembali Normal 🎊 Siap-siap belanja gas, ya! 💪🔥
mail order prescription drugs from canada: discount drug pharmacy – discount drug mart
darkmarket list https://github.com/darknetwebsitesgflpx/darknetwebsites – tor markets links
Cassino online Pin Up https://888casino-official-brazil.site ganhos sem limites! Jogue seus caca-niqueis favoritos, participe de torneios, ganhe cashback e rodadas gratis. Licenca, seguranca e pagamentos rapidos!
dark market list deep web drug store darknet sites
darknet drug market https://github.com/darknetmarketlinks2025/darknetmarkets – dark markets 2022
darknet market list free dark web dark web drug marketplace
dark web market list [url=https://github.com/darkmarketlinkp22jr/darkmarketlink ]dark web market links [/url]
darknet marketplace dark web link dark web link
darknet drug market darkmarket tor dark web
UID_72339950###
Heboh! 📣🔥 Unjuk Rasa di Polda Jatim 📢 Menuduh Jokowi Terlibat Korupsi! 😱🔍
online pharmacy prescription https://discountdrugmart.pro/# discount drug mart
uk pharmacy no prescription discount drug mart discount drug mart
canadian pharmacy oxycodone: canadian pharmacy online ship to usa – easy canadian pharm
dark market list https://github.com/darknetwebsitesgflpx/darknetwebsites – dark web sites
elon casino bangladesh elon casino bangladesh .
non prescription medicine pharmacy http://familypharmacy.company/# Best online pharmacy
UID_27764099###
Ini yang di ganti >>> “Bingung Kenapa 😕❓” Federasi Sepak Bola Pakistan Disanksi FIFA “Baca Penyebabnya Disini! 🧐🔍”
tor market url darknet site dark web market
darkmarkets https://github.com/tormarkets2025ukaz1/tormarkets2025 – dark web drug marketplace
dark markets darknet drug links dark web site
tor dark web https://github.com/darknetdruglinksvojns/darknetdruglinks – tor market
elon casino elon casino .
https://cleanliness-cleaning.ru/
darknet market links dark web sites links darknet market lists
dark web search engine dark web market links dark market url
dark market url dark net tor market links
Общая кремация домашних животных по доступным ценам — полная информация по ссылке https://www.sqlservercentral.com/forums/user/angelvetmos
It’s hard to come by well-informed people about this topic, however, you seem like you know what you’re talking about! Thanks
химчистка дивана на дому москва стоимость
darknet sites https://github.com/darknetwebsitesgflpx/darknetwebsites – darknet markets
What’s Taking place i am new to this, I stumbled upon this I have found It positively helpful and it has aided me out loads. I am hoping to contribute & help different customers like its helped me. Good job.
deep web sites dark web websites dark web market
darknet links tor darknet the dark internet
canadian pharmacy world coupon http://megaindiapharm.com/# Mega India Pharm
dark web market links https://github.com/tormarkets2025ukaz1/tormarkets2025 – dark websites
Свежие и актуальные новости https://sugar-news.com.ua Украины и мира! Будьте в курсе последних событий, аналитики и трендов. Читайте последние новости Украины онлайн!
UID_27764099###
Ini yang di ganti >>> “Bingung Kenapa 😕❓” Federasi Sepak Bola Pakistan Disanksi FIFA “Baca Penyebabnya Disini! 🧐🔍”
darkmarket url dark web site dark web websites
how to access dark web darkmarket link the dark internet
discount drug mart pharmacy: discount drug mart pharmacy – discount drug mart pharmacy
prescription drugs from canada https://familypharmacy.company/# Best online pharmacy
dark market url https://github.com/darknetwebsitesgflpx/darknetwebsites – darknet websites
how to get on dark web darknet drug store deep web drug store
dark websites https://github.com/darknetmarketlinks2025/darknetmarkets – dark market list
drug markets dark web https://github.com/darknetdruglinksvojns/darknetdruglinks – darknet site
https://clean-list.ru/
dark web market list darkmarket list tor markets 2025
Рекомендую эту фирму для закупки расходных материалов и оборудования для маркировки, все детали тут https://www.pexels.com/@labe-laire-2149334861/
You are so interesting! I do not suppose I’ve read through a single thing like this before. So great to discover someone with a few unique thoughts on this subject. Really.. thanks for starting this up. This site is something that is required on the web, someone with a bit of originality.
darknet marketplace dark web drug marketplace deep web drug links
dark markets 2022 https://github.com/darknetwebsitesgflpx/darknetwebsites – darkmarket
overseas pharmacy no prescription https://megaindiapharm.com/# top 10 pharmacies in india
darknet marketplace dark websites darknet drug links
dark market link blackweb official website darkmarkets
tor darknet https://github.com/darkmarketlinkp22jr/darkmarketlink – deep web drug store
dark web links https://github.com/tormarkets2025ukaz1/tormarkets2025 – dark market
drug markets dark web https://github.com/darknetdruglinksvojns/darknetdruglinks – bitcoin dark web
Лучшие эксперты в одном месте! орган по сертификации выбирает маркетплейс и агрегатор экспертных компаний помогает найти надежных специалистов по разным направлениям. Удобный выбор, проверенные отзывы и рейтинг!
darkmarket 2025 darkmarket url how to access dark web
prescription drugs online https://xxlmexicanpharm.com/# xxl mexican pharm
darknet market links https://github.com/darknetwebsitesgflpx/darknetwebsites – darknet market
canadian pharmacy antibiotics: easy canadian pharm – easy canadian pharm
best canadian online pharmacy reviews easy canadian pharm easy canadian pharm
darkweb marketplace tor marketplace tor markets links
tpzq4n
drug markets dark web darkmarket link deep web drug store
darknet drug market https://github.com/darknetmarketlinks2025/darknetmarkets – darkmarkets
bitcoin dark web https://github.com/darkmarketlinkp22jr/darkmarketlink – dark market onion
dark market onion https://github.com/darknetdruglinksvojns/darknetdruglinks – dark web drug marketplace
https://clean-sharks.ru/
canada drugs coupon code https://discountdrugmart.pro/# discount drug pharmacy
dark market url https://github.com/darknetwebsitesgflpx/darknetwebsites – dark web market
dark web drug marketplace how to get on dark web darkweb marketplace
darknet marketplace best darknet markets darknet drug links
UID_74743238###
Ini dia! 🎉🎉 ASN BKN Ubah Pola Kerja yang baru dan efisien! 🎉🎉.
the dark internet dark markets 2025 darkmarket
best darknet markets https://github.com/tormarkets2025ukaz1/tormarkets2025 – tor darknet
dark web market list https://github.com/darknetdruglinksvojns/darknetdruglinks – darknet markets
You’ve made some decent points there. I checked on the web to learn more about the issue and found most people will go along with your views on this web site.
sex nhật, hiếp dâm trẻ em, ấu dâm, buôn bán vũ khí, ma túy, bán súng, sextoy, chơi đĩ, sex bạo lực, sex học đường, tội phạm tình dục
darknet sites dark website tor markets links
dark markets 2022 https://github.com/darknetwebsitesgflpx/darknetwebsites – deep web drug url
UID_74743238###
Ini dia! 🎉🎉 ASN BKN Ubah Pola Kerja yang baru dan efisien! 🎉🎉.
UID_74743238###
Ini dia! 🎉🎉 ASN BKN Ubah Pola Kerja yang baru dan efisien! 🎉🎉.
cheapest pharmacy for prescription drugs https://xxlmexicanpharm.com/# xxl mexican pharm
drug markets onion darknet marketplace dark markets 2025
deep web drug links free dark web deep dark web
tor dark web deep web search tor market url
purple pharmacy mexico price list: reputable mexican pharmacies online – xxl mexican pharm
dark web sites links https://github.com/darkmarketlinkp22jr/darkmarketlink – darkmarket 2022
dark web sites https://github.com/darknetmarketlinks2025/darknetmarkets – darknet websites
tor marketplace https://github.com/darknetdruglinksvojns/darknetdruglinks – darkmarket list
dark web search engines darknet marketplace dark market list
UID_83344528###
Inilah 🎉🎉 Pupuk Inovatif Kebun Riset Kujang yang bikin Wamen BUMN bangga! 💪🏻🇮🇩
canadian pharmacy world coupon code https://megaindiapharm.shop/# online pharmacy india
darkweb marketplace https://github.com/darknetwebsitesgflpx/darknetwebsites – tor dark web
bitcoin dark web tor market darkmarket url
https://clean-sharks.ru/
dark websites https://github.com/tormarkets2025ukaz1/tormarkets2025 – dark web link
deep web drug url dark web sites links drug markets onion
deep dark web darknet markets darknet marketplace
What i do not understood is in reality how you’re not actually a lot more smartly-favored than you might be right now. You’re so intelligent. You know therefore significantly on the subject of this matter, produced me individually believe it from numerous numerous angles. Its like men and women don’t seem to be interested unless it¦s one thing to accomplish with Lady gaga! Your individual stuffs excellent. Always maintain it up!
dark web market list https://github.com/darknetmarketlinks2025/darknetmarkets – darkmarket link
dark market url https://github.com/darknetdruglinksvojns/darknetdruglinks – dark market 2022
клининг после ремонта квартиры
dark market url dark web sites links bitcoin dark web
dark market 2022 https://github.com/darknetwebsitesgflpx/darknetwebsites – darkmarket link
Хотите играть в Steam-игры shared-steam.org дешевле? Shared-Steam.org предлагает аренду аккаунтов с топовыми играми. Безопасность, доступность и удобство – ваш гейминг без границ!
dark market onion darkmarket link dark web search engines
drug markets dark web https://github.com/tormarkets2025ukaz1/tormarkets2025 – dark markets
darknet market https://github.com/darknetmarketlinks2025/darknetmarkets – dark market onion
darkweb marketplace https://github.com/darknetdruglinksvojns/darknetdruglinks – drug markets dark web
deep dark web darknet drug links darknet drug links
tor market darknet sites tor marketplace
Jackpot progresif menarik banyak pemain http://preman69.tech/# Banyak kasino menawarkan permainan langsung yang seru
Оптимизируйте свою жизнь с электрокарнизом с таймером, наслаждайтесь комфортом и современностью.
Создайте атмосферу уюта и стиля с помощью электрокарниза и таймера, добавит функциональности и комфорта.
Эффективное управление светом и приватностью с электрокарнизом и таймером, создайте идеальную атмосферу в вашем доме.
Оптимальное решение для автоматизации штор – электрокарниз с таймером, позволит вам наслаждаться своим временем и пространством.
Дизайнерское решение для современного дома – электрокарниз с таймером, который сочетает в себе красоту и практичность.
шторы умный дом автоматические https://prokarniz50.ru/ .
Pemain harus memahami aturan masing-masing mesin: preman69 – preman69.tech
tor market https://github.com/darknetwebsitesgflpx/darknetwebsites – deep dark web
tor market dark web websites deep web markets
preman69 slot preman69 slot Permainan slot bisa dimainkan dengan berbagai taruhan
Slot klasik tetap menjadi favorit banyak orang http://garuda888.top/# Slot memberikan kesempatan untuk menang besar
https://bonaslot.site/# Kasino selalu memperbarui mesin slotnya
tor markets darknet market list dark web market
tor market url the dark internet tor darknet
UID_83344528###
Inilah 🎉🎉 Pupuk Inovatif Kebun Riset Kujang yang bikin Wamen BUMN bangga! 💪🏻🇮🇩
tor darknet https://github.com/tormarkets2025ukaz1/tormarkets2025 – dark web link
dark market onion https://github.com/darknetmarketlinks2025/darknetmarkets – drug markets onion
dark market url https://github.com/darknetdruglinksvojns/darknetdruglinks – darknet sites
порно германия порно германия .
tor market url drug markets dark web darkmarkets
Create images deepnude ai easily with AI. Remove clothes from anyone in the image and enjoy their nakedness.
dark web market list https://github.com/darknetwebsitesgflpx/darknetwebsites – darkmarket 2022
секс с немкой секс с немкой .
darkweb marketplace tor market links blackweb official website
best darknet markets dark markets deep web markets
dark web market list https://github.com/darkmarketlinkp22jr/darkmarketlink – darknet market lists
darknet market list https://github.com/darknetdruglinksvojns/darknetdruglinks – dark market list
deep web drug links darknet market links tor dark web
tor marketplace https://github.com/darknetwebsitesgflpx/darknetwebsites – darkmarket
Slot dengan tema film terkenal menarik banyak perhatian http://preman69.tech/# Kasino menyediakan layanan pelanggan yang baik
Slot dengan grafis 3D sangat mengesankan https://slotdemo.auction/# Banyak pemain mencari mesin dengan RTP tinggi
Mesin slot baru selalu menarik minat: garuda888 slot – garuda888
https://bonaslot.site/# Slot klasik tetap menjadi favorit banyak orang
dark market url dark web market links deep web links
dark web drug marketplace dark markets deep web drug links
darkmarket list https://github.com/tormarkets2025ukaz1/tormarkets2025 – dark market url
tor markets https://github.com/darknetmarketlinks2025/darknetmarkets – darknet markets
уборка офисов цены
Turkiye’deki slot makineleri https://slots-cool.com gercek parayla oynanabilen slotlar kapsaml bir baks! Nerede oynan?r, hangi slotlar en karldr ve en iyi casino nasl secilir Kumar severler icin ipuclar, incelemeler, derecelendirmeler ve bonuslar!
Turkiye Slotlar Rehberi Yeni slotlar En Iyi Slotlar ve Casinolar! Nerede oynayabileceginizi, hangi oyunlarn populer oldugunu ve bonuslar nasl alabileceginizi ogrenin. Oyun alanlar ve guncel eglencelere dair kapsaml bir genel baks!
dark market url https://github.com/darknetwebsitesgflpx/darknetwebsites – darknet drug market
tor markets links dark web search engine tor market links
darkmarket 2025 dark websites deep web sites
Keep working ,impressive job!
dark website dark web search engines dark market onion
slot demo gratis slot demo Banyak pemain mencari mesin dengan RTP tinggi
deep web sites how to access dark web free dark web
darkmarket url https://github.com/darkmarketlinkp22jr/darkmarketlink – deep web drug store
tor market https://github.com/darknetdruglinksvojns/darknetdruglinks – tor markets links
Kasino di Bali menarik banyak pengunjung http://slotdemo.auction/# Banyak kasino menawarkan permainan langsung yang seru
Jackpot besar bisa mengubah hidup seseorang: garuda888 slot – garuda888 slot
Trying cbd thc drops for drinks has been absolutely the journey. As someone itching on habitual remedies, delving into the out of sight of hemp has been eye-opening. From CBD grease to hemp seeds and protein bray, I’ve explored a classification of goods. In defiance of the gallimaufry adjacent hemp, researching and consulting experts be enduring helped cruise this burgeoning field. Entire, my contact with hemp has been decided, oblation holistic well-being solutions and sustainable choices.
http://garuda888.top/# Slot menjadi daya tarik utama di kasino
Beberapa kasino memiliki area khusus untuk slot http://slotdemo.auction/# Banyak kasino memiliki promosi untuk slot
tor dark web https://github.com/darknetwebsitesgflpx/darknetwebsites – tor darknet
услуги грузчиков в минске вывоз старой мебели
darknet markets 2025 darknet site dark market onion
dark market list dark web links deep web sites
переезд в другую страну перевозка минитрактора
dark web access dark web sites links dark web links
dark web link darknet search engine free dark web
darknet market lists https://github.com/darkmarketlinkp22jr/darkmarketlink – dark market onion
https://uborka-kvartir-luberci.ru/
I had no idea how to download Metamask, but https://download.metaredi.org/ provided a clear guide. Now I can use my crypto wallet without any issues.
deep web drug store https://github.com/darknetmarketlinks2025/darknetmarkets – darknet websites
dark web site darknet drug links dark market 2025
Знакомства в Уфе ufavip.sbs с нашей платформой стали еще проще, можно встретить девушек, готовых к интересному общению и приятному времяпрепровождению. Здесь каждый найдет то, что ищет: от легкого флирта до серьезных отношений.
darkmarket list https://github.com/darknetwebsitesgflpx/darknetwebsites – tor darknet
UID_21891068###
Takjub 😮 dengan fenomena serbu gas? Yuk, baca Warung Tatang Diserbu Warga dan temukan faktanya! 🕵️♀️👀
darknet market dark market list darkmarket url
Slot dengan grafis 3D sangat mengesankan http://preman69.tech/# Banyak kasino memiliki promosi untuk slot
darkmarkets drug markets onion dark market url
dark markets blackweb official website dark markets
free dark web deep web search dark net
Jackpot besar bisa mengubah hidup seseorang: bonaslot – BonaSlot
https://preman69.tech/# Mesin slot sering diperbarui dengan game baru
darknet market links https://github.com/darkmarketlinkp22jr/darkmarketlink – dark market url
dark market list https://github.com/darknetmarketlinks2025/darknetmarkets – darknet market list
UID_21891068###
Takjub 😮 dengan fenomena serbu gas? Yuk, baca Warung Tatang Diserbu Warga dan temukan faktanya! 🕵️♀️👀
darknet market links https://github.com/darknetdruglinksvojns/darknetdruglinks – deep web drug markets
best darknet markets onion market tor market url
slot88 slot88.company Kasino menyediakan layanan pelanggan yang baik
darkweb marketplace darknet search engine deep web markets
tor markets how to access dark web tor markets links
tor dark web free dark web deep web drug markets
Kasino di Bali menarik banyak pengunjung http://bonaslot.site/# Mesin slot menawarkan berbagai tema menarik
drug markets onion darknet search engine tor dark web
уборка офисов москва
kn7ljq
http://preman69.tech/# Beberapa kasino memiliki area khusus untuk slot
Kasino sering mengadakan turnamen slot menarik: garuda888.top – garuda888 slot
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
https://klining-64.ru/
tor markets 2025 deep web drug links darkmarket list
darknet links darknet sites dark web link
UID_25978847###
situs terbaik hanya di slot gacor agentotoplay
https://klining-64.ru/
tor markets darknet seiten dark market list
Banyak pemain menikmati jackpot harian di slot https://garuda888.top/# Bermain slot bisa menjadi pengalaman sosial
Is it possible to win at Lucky Jet? We analyze the main strategies, analyze player reviews, and give an honest assessment of the popular game. Read to avoid mistakes and increase your chances of success!
Pemain sering mencoba berbagai jenis slot https://preman69.tech/# Slot menjadi bagian penting dari industri kasino
darknet links dark market 2025 deep web drug store
dark web market darknet drugs dark websites
tor darknet black internet best darknet markets
bitcoin dark web deep web markets deep web drug store
http://slotdemo.auction/# Kasino sering mengadakan turnamen slot menarik
Keseruan bermain slot selalu menggoda para pemain: BonaSlot – bonaslot
dark market link dark web websites how to access dark web
https://uborka-kvartir-luberci.ru/
best darknet markets deep web drug store dark web market links
deep web search dark market 2025 dark market
https://richexchanger.com/
https://richexchanger.com/
darknet sites https://github.com/tormarkets2025ukaz1/tormarkets2025 – dark web links
dark web link https://github.com/darknetdruglinksvojns/darknetdruglinks – dark web link
darknet seiten darkweb marketplace dark web site
darknet market links https://github.com/darkmarketlinkp22jr/darkmarketlink – dark web sites
Pemain harus memahami aturan masing-masing mesin http://preman69.tech/# Pemain harus memahami aturan masing-masing mesin
slot88 slot88 Banyak pemain menikmati jackpot harian di slot
dark web markets deep web links tor markets
deep web drug store dark market link darknet websites
I recently occupied this purlieus to lay one’s hands on https://synergy3.com/plumbing/repiping/ , and I couldn’t be happier with the results. The search was straightforward, and I appreciated the particularized profiles and bloke reviews instead of each contractor. It made comparing options and reading round other clients’ experiences easy. The contractors I contacted were on time, trained, and offered competitive quotes. This locality is a fantastic resource seeing that anyone needing reliable place repair services. Warmly recommended in search its simple interface and quality listings!
tor darknet https://github.com/tormarkets2025ukaz1/tormarkets2025 – darkmarkets
darknet drug store deep web drug store dark web links
darkmarket https://github.com/darknetdruglinksvojns/darknetdruglinks – darkmarket url
1win кликер http://mabc.com.kg/ .
mostbet регистрация mostbet регистрация .
мультики ххх http://www.multiki-rukoeb1.ru .
darkmarket link https://github.com/darkmarketlinkp22jr/darkmarketlink – deep web drug store
порно с мамкой порно с мамкой .
порно гинеколог порно гинеколог .
地方交付税法(昭和25年法律第211号)に定めるところによるほか、毎年度、制度として確立された年金、医療及び介護の社대구출장샵会保障給付並びに少子化に対処するための施策に要する経費に充てるものとすると定められている(第1条第2項)。 すっかり酔いつぶれた五郎を抱えて石の家にたどり着いた時、五郎の懐に固いものが入れられていることに純が気付く。
Nice post. I learn something totally new and challenging on blogs I stumbleupon every day. It’s always helpful to read articles from other writers and practice a little something from other sites.
1 вин официальный сайт http://mabc.com.kg .
мостбет букмекерская контора https://www.gtrtt.com.kg .
http://bonaslot.site/# Kasino di Jakarta memiliki berbagai pilihan permainan
порно мульт multiki-rukoeb1.ru .
Кружевной бюстгальтер https://www.wildberries.ru/catalog/117605496/detail.aspx без косточек с застежкой спереди — это идеальный выбор для тех, кто ценит комфорт и стиль. Изготовленный из мягкого и нежного кружева, он обеспечивает естественную поддержку, не ограничивая движения. Удобная застежка спереди позволяет легко надевать и снимать бюстгальтер, а его изысканный дизайн добавляет нотку романтики в ваш образ.
Trying https://www.nothingbuthemp.net/products/brez-5mg-thc-2200mg-lions-mane has been quite the journey. As someone keen on natural remedies, delving into the epoch of hemp has been eye-opening. From CBD lubricant to hemp seeds and protein capacity, I’ve explored a disparity of goods. Undeterred by the confusion bordering hemp, researching and consulting experts organize helped cruise this burgeoning field. Entire, my contact with hemp has been positive, present holistic well-being solutions and sustainable choices.
I recently used this locality to allot https://synergy3.com/hvac/heating/boilers/ , and I couldn’t be happier with the results. The search was straightforward, and I appreciated the comprehensive profiles and customer reviews on the side of each contractor. It made comparing options and reading wide other clients’ experiences easy. The contractors I contacted were prompt, professional, and offered competitive quotes. This position is a fantastic resource seeing that anyone needing reliable haven vamp services. Enthusiastically recommended in search its user-friendly interface and eminence listings!
?El paraiso del juego en Pin Up Casino https://ganar-apuestas-deportivas.com te espera! Echa un vistazo a nuestra coleccion de tragamonedas, juegos en vivo y juegos de mesa. Bonos rentables, torneos y un programa VIP te proporcionaran el maximo de emociones. ?Empieza a jugar ahora y gana!
секс милфы секс милфы .
Pemain bisa menikmati slot dari kenyamanan rumah: preman69 – preman69
Создайте идеальную атмосферу в вашем доме с программируемым электрокарнизом, совместим с любым интерьером.
Трансформируйте ваше жилище с помощью программируемого электрокарниза, помогает вам расслабиться и отдохнуть.
Сделайте вашу жизнь проще с программируемым электрокарнизом, поможет вам создать идеальный микроклимат.
Создайте идеальные условия для сна с помощью программируемого электрокарниза, создаст идеальную атмосферу для полноценного отдыха.
Регулируйте интенсивность света и тепла с помощью программируемого электрокарниза, который сделает вашу жизнь проще и комфортнее.
умный электрокарниз xiaomi https://elektrokarniz190.ru/ .
порно с гинекологом порно с гинекологом .
dark market deep web drug url dark web websites
darknet drugs deep web drug links darknet markets 2025
Pemain bisa menikmati slot dari kenyamanan rumah https://preman69.tech/# Banyak kasino memiliki promosi untuk slot
best darknet markets darkmarkets tor market
UID_25978847###
situs terbaik hanya di slot gacor agentotoplay
tor dark web https://github.com/darknetmarketlinks2025/darknetmarkets – dark markets 2022
deep web drug store https://github.com/darknetdruglinksvojns/darknetdruglinks – deep web markets
dark market onion https://github.com/darkmarketlinkp22jr/darkmarketlink – darkweb marketplace
tor market url tor markets links darkweb marketplace
darknet markets darkweb marketplace the dark internet
Каталог финансовых организаций https://srochno-zaym-online.ru в которых можно получить срочные онлайн займы и кредиты не выходя из дома через интернет.
Срочный онлайн займ srochno-zaym-online.ru современный способ быстро получить взаймы необходимую сумму на личные нужды на небольшой срок.
dark web markets darknet drug store bitcoin dark web
dark market 2025 darkmarket url dark web links
Каталог финансовых организаций https://srochno-zaym-online.ru в которых можно получить срочные онлайн займы и кредиты не выходя из дома.
перевозки грузоперевозки минск
dark web sites https://github.com/darknetwebsitesgflpx/darknetwebsites – dark web sites
darknet market lists darknet drug links dark markets
dark web market https://github.com/darknetmarketlinks2025/darknetmarkets – dark web sites links
новые лучшие аниме 2025 2025 hdrezka com
drug markets dark web https://github.com/darknetdruglinksvojns/darknetdruglinks – darkmarket url
dark market onion https://github.com/darkmarketlinkp22jr/darkmarketlink – dark market link
https://slot88.company/# Banyak pemain menikmati jackpot harian di slot
У этой фирмы есть разнообразные коллекции постельного белья на любой вкус и цвет, ознакомьтесь с предложениями здесь https://gitlab.com/Dreamsstore
dark web drug marketplace drug markets onion dark market onion
Slot dengan tema film terkenal menarik banyak perhatian http://preman69.tech/# Jackpot progresif menarik banyak pemain
UID_95859078###
Baru-baru ini, para pemain Mahjong Wins 3 dikejutkan dengan bocoran RTP yang diklaim bisa meningkatkan peluang kemenangan secara signifikan. Banyak yang percaya bahwa informasi ini membantu mereka mendapatkan hasil yang lebih konsisten dalam permainan. Jika Anda ingin tahu lebih lanjut, cek bocoran RTP Mahjong Wins 3 hari ini dan lihat apakah strategi ini benar-benar efektif.
Kasino sering mengadakan turnamen slot menarik: garuda888 slot – garuda888
UID_95859078###
Baru-baru ini, para pemain Mahjong Wins 3 dikejutkan dengan bocoran RTP yang diklaim bisa meningkatkan peluang kemenangan secara signifikan. Banyak yang percaya bahwa informasi ini membantu mereka mendapatkan hasil yang lebih konsisten dalam permainan. Jika Anda ingin tahu lebih lanjut, cek bocoran RTP Mahjong Wins 3 hari ini dan lihat apakah strategi ini benar-benar efektif.
deep web sites tor dark web darknet market lists
dark web search engine dark market onion darkmarket url
Annoying https://www.nothingbuthemp.net/collections/thc-tinctures has been absolutely the journey. As someone itching on idiot remedies, delving into the epoch of hemp has been eye-opening. From CBD lubricant to hemp seeds and protein potential, I’ve explored a diversification of goods. Despite the gallimaufry local hemp, researching and consulting experts acquire helped handle this burgeoning field. Entire, my contact with hemp has been confident, oblation holistic well-being solutions and sustainable choices.
перевозка детской коляски перевозка шкафа
dark markets 2022 https://github.com/tormarkets2025ukaz1/tormarkets2025 – dark market
tor markets 2022 https://github.com/darknetmarketlinks2025/darknetmarkets – darknet drug store
bitcoin dark web https://github.com/darknetdruglinksvojns/darknetdruglinks – darknet drug store
tor dark web https://github.com/darkmarketlinkp22jr/darkmarketlink – dark web sites links
tor dark web darkmarket url dark web access
I’m amazed, I must say. Rarely do I come across a blog that’s both equally educative and interesting, and let me tell you, you’ve hit the nail on the head. The problem is an issue that not enough people are speaking intelligently about. I’m very happy that I came across this during my hunt for something regarding this.
slot88.company slot88 Kasino menawarkan pengalaman bermain yang seru
best darknet markets dark market link tor markets
bitcoin dark web tor dark web how to access dark web
darknet markets dark web sites links free dark web
dark web site free dark web the dark internet
https://slot88.company/# Bermain slot bisa menjadi pengalaman sosial
Установка онлайн-касс с соблюдением законодательства в Санкт-Петербурге — Ознакомьтесь с деталями https://knowyourmeme.com/users/posbazarspb
Pemain harus memahami aturan masing-masing mesin https://slot88.company/# Mesin slot menawarkan berbagai tema menarik
darkweb marketplace https://github.com/darknetwebsitesgflpx/darknetwebsites – dark web market list
tor markets 2022 [url=https://github.com/darknetmarketlinks2025/darknetmarkets ]tor market links [/url]
tor dark web https://github.com/darknetdruglinksvojns/darknetdruglinks – deep web drug markets
darknet market https://github.com/darkmarketlinkp22jr/darkmarketlink – tor markets links
how to get on dark web dark web market dark web market list
п»їKasino di Indonesia sangat populer di kalangan wisatawan: preman69.tech – preman69 slot
darkmarket link tor darknet how to get on dark web
dark web search engine deep web markets darknet search engine
onion market bitcoin dark web darknet sites
dark market link https://github.com/darknetwebsitesgflpx/darknetwebsites – darknet drug store
darkmarkets https://github.com/darknetmarketlinks2025/darknetmarkets – tor market
dark markets 2022 https://github.com/darknetdruglinksvojns/darknetdruglinks – dark web market links
dark web links https://github.com/darkmarketlinkp22jr/darkmarketlink – darkmarket list
sex nhật hiếp dâm trẻ em ấu dâm buôn bán vũ khí ma túy bán súng sextoy chơi đĩ sex bạo lực sex học đường tội phạm tình dục chơi les đĩ đực người mẫu bán dâm
darknet market list darknet market lists free dark web
UID_95859078###
Baru-baru ini, para pemain Mahjong Wins 3 dikejutkan dengan bocoran RTP yang diklaim bisa meningkatkan peluang kemenangan secara signifikan. Banyak yang percaya bahwa informasi ini membantu mereka mendapatkan hasil yang lebih konsisten dalam permainan. Jika Anda ingin tahu lebih lanjut, cek bocoran RTP Mahjong Wins 3 hari ini dan lihat apakah strategi ini benar-benar efektif.
Slot dengan fitur interaktif semakin banyak tersedia https://garuda888.top/# п»їKasino di Indonesia sangat populer di kalangan wisatawan
http://garuda888.top/# Slot menjadi bagian penting dari industri kasino
tor markets darkmarket tor darknet
tor market links black internet deep web sites
darknet site https://github.com/darknetwebsitesgflpx/darknetwebsites – dark websites
drug markets dark web https://github.com/tormarkets2025ukaz1/tormarkets2025 – tor darknet
deep web drug url https://github.com/darknetmarketlinks2025/darknetmarkets – dark web market links
Mesin slot baru selalu menarik minat: garuda888 – garuda888 slot
dark markets https://github.com/darknetdruglinksvojns/darknetdruglinks – darknet drug links
darknet drug store https://github.com/darkmarketlinkp22jr/darkmarketlink – tor darknet
tor market dark market url dark website
darknet site darknet drug links dark web search engine
dark web market list how to get on dark web deep web search
Каталог финансовых организаций srochno-zaym-online в которых можно получить срочные онлайн займы и кредиты не выходя из дома.
hd rezka драмы 1080p на айфоне резка детективы новинки hd
onion market https://github.com/tormarkets2025ukaz1/tormarkets2025 – tor marketplace
Permainan slot bisa dimainkan dengan berbagai taruhan https://garuda888.top/# Mesin slot dapat dimainkan dalam berbagai bahasa
vibracion de motor
Sistemas de ajuste: esencial para el rendimiento suave y eficiente de las máquinas.
En el entorno de la tecnología actual, donde la efectividad y la estabilidad del equipo son de máxima significancia, los dispositivos de ajuste juegan un papel crucial. Estos sistemas específicos están diseñados para balancear y asegurar elementos móviles, ya sea en herramientas manufacturera, vehículos de desplazamiento o incluso en electrodomésticos caseros.
Para los especialistas en conservación de sistemas y los ingenieros, manejar con dispositivos de equilibrado es importante para garantizar el operación fluido y estable de cualquier mecanismo dinámico. Gracias a estas opciones modernas sofisticadas, es posible limitar considerablemente las sacudidas, el zumbido y la esfuerzo sobre los rodamientos, aumentando la longevidad de piezas importantes.
Asimismo significativo es el rol que juegan los sistemas de balanceo en la servicio al cliente. El soporte especializado y el soporte constante empleando estos sistemas habilitan proporcionar soluciones de óptima estándar, aumentando la bienestar de los compradores.
Para los dueños de negocios, la contribución en estaciones de balanceo y medidores puede ser fundamental para optimizar la productividad y eficiencia de sus sistemas. Esto es principalmente relevante para los emprendedores que manejan reducidas y modestas negocios, donde cada elemento vale.
Asimismo, los sistemas de ajuste tienen una vasta aplicación en el ámbito de la seguridad y el gestión de calidad. Posibilitan detectar probables errores, impidiendo arreglos caras y problemas a los equipos. También, los datos generados de estos dispositivos pueden usarse para perfeccionar sistemas y incrementar la visibilidad en buscadores de consulta.
Las áreas de utilización de los equipos de equilibrado abarcan variadas ramas, desde la fabricación de bicicletas hasta el seguimiento ambiental. No interesa si se refiere de extensas manufacturas manufactureras o pequeños espacios de uso personal, los dispositivos de equilibrado son fundamentales para garantizar un desempeño óptimo y sin riesgo de paradas.
darknet drug market https://github.com/darknetmarketlinks2025/darknetmarkets – darkmarket 2022
eloncasino eloncasino .
elon bet elon bet .
tor darknet https://github.com/darknetdruglinksvojns/darknetdruglinks – darknet drug market
darknet market links https://github.com/darkmarketlinkp22jr/darkmarketlink – dark markets
onewin onewin .
preman69 slot preman69.tech Beberapa kasino memiliki area khusus untuk slot
elon online casino elon online casino .
https://slot88.company/# Kasino di Indonesia menyediakan hiburan yang beragam
elon bet elon bet .
darknet drug links blackweb official website dark web markets
1win вход 1win вход .
elon online casino [url=http://www.elonbangladeshbet.com]elon online casino[/url] .
deep web drug store dark market list dark market 2025
blackweb official website darkmarket list deep web sites
darknet market dark website darknet seiten
UID_57331425###
Skandal terbaru mengguncang komunitas pecinta game slot setelah seorang admin terkenal, Rachel, dikabarkan tertangkap membocorkan pola kemenangan Gate of Olympus. Banyak yang bertanya-tanya apakah informasi ini benar-benar akurat atau hanya sekadar rumor yang beredar di kalangan pemain. Simak lebih lanjut detailnya dalam artikel admin Rachel tertangkap bocorkan pola Gate of Olympus.
tor market https://github.com/darknetwebsitesgflpx/darknetwebsites – deep web drug markets
dark market link https://github.com/tormarkets2025ukaz1/tormarkets2025 – darknet marketplace
UID_57331425###
Skandal terbaru mengguncang komunitas pecinta game slot setelah seorang admin terkenal, Rachel, dikabarkan tertangkap membocorkan pola kemenangan Gate of Olympus. Banyak yang bertanya-tanya apakah informasi ini benar-benar akurat atau hanya sekadar rumor yang beredar di kalangan pemain. Simak lebih lanjut detailnya dalam artikel admin Rachel tertangkap bocorkan pola Gate of Olympus.
Banyak kasino menawarkan permainan langsung yang seru: slot88.company – slot88
bitcoin dark web https://github.com/darknetmarketlinks2025/darknetmarkets – darknet drug store
darkmarkets https://github.com/darknetdruglinksvojns/darknetdruglinks – dark web market links
bitcoin dark web https://github.com/darkmarketlinkp22jr/darkmarketlink – tor market url
Форум для кулинаров https://food-recipe.ru и рестораторов! Лучшие рецепты, тренды гастрономии, обсуждения ресторанного бизнеса. Общайтесь, делитесь опытом и вдохновляйтесь новыми идеями. Присоединяйтесь к нашему кулинарному сообществу!
I recently occupied this site to lay one’s hands on Heating Services , and I couldn’t be happier with the results. The search was straightforward, and I appreciated the detailed profiles and patron reviews on the side of each contractor. It made comparing options and reading wide other clients’ experiences easy. The contractors I contacted were coax, trained, and offered competitive quotes. This milieu is a unbelievable resource in behalf of anyone needing reliable territory renew services. Enthusiastically recommended as a replacement for its understandable interface and trait listings!
Beberapa kasino memiliki area khusus untuk slot https://garuda888.top/# Mesin slot sering diperbarui dengan game baru
dark net darknet marketplace dark web sites links
dark web sites links tor markets 2025 dark web drug marketplace
dark market onion how to get on dark web dark website
darknet market links darknet search engine dark websites
dark web market links dark web market links dark web access
http://garuda888.top/# Kasino selalu memperbarui mesin slotnya
Красивые поздравления https://photofile.ru/krasivye-hristianskie-otkrytki-s-dobrym-utrom-i-blagosloveniyami-140-kartinok в одном месте! Огромный выбор картинок и открыток для любого повода. День рождения, юбилей, профессиональные праздники – найдите идеальное поздравление!
tor market url https://github.com/darknetwebsitesgflpx/darknetwebsites – dark web links
Slot dengan tema film terkenal menarik banyak perhatian: slot demo pg gratis – slotdemo
Del Mar Energy Inc
darknet market list https://github.com/darkmarketlinkp22jr/darkmarketlink – dark web links
dark market 2022 https://github.com/tormarkets2025ukaz1/tormarkets2025 – dark web drug marketplace
tor marketplace https://github.com/darknetdruglinksvojns/darknetdruglinks – tor markets 2022
dark net dark web market links dark web access
darknet markets drug markets onion darknet seiten
black internet blackweb dark market link
Pemain harus menetapkan batas saat bermain http://slotdemo.auction/# Kasino di Indonesia menyediakan hiburan yang beragam
Trying gummies has been quite the journey. As someone keen on imbecile remedies, delving into the the human race of hemp has been eye-opening. From CBD oil to hemp seeds and protein potential, I’ve explored a variety of goods. Despite the mess local hemp, researching and consulting experts have helped nautical con this burgeoning field. Comprehensive, my meet with with hemp has been confident, gift holistic well-being solutions and sustainable choices.
Новый уникальный маркетплейс NOVA, есть все! Москва, Питер, всегда свежие клады!Акция для новых магазинов – продай на 1 млн, получи 100к!Приглашаем к сотрудничеству рекламодателей!
dark market link https://github.com/darknetmarketlinks2025/darknetmarkets – darkmarket list
I blog quite often and I really thank you for your content. This article has truly peaked my interest. I am going to take a note of your website and keep checking for new details about once per week. I subscribed to your Feed too.
Hi there are using WordPress for your site platform? I’m new to the blog world but I’m trying to get started and create my own. Do you require any html coding knowledge to make your own blog? Any help would be really appreciated!
Wyoming Valley Equipment LLC
darknet websites deep dark web tor markets
UID_17136916###
Kisah inspiratif datang dari seorang tukang ojek online asal Tangerang yang berhasil membawa pulang hadiah fantastis setelah bermain Mahjong Ways 2. Dengan modal kecil, ia sukses mengubah nasibnya dan meraih kemenangan besar senilai 200 juta rupiah. Penasaran bagaimana caranya? Simak kisah lengkapnya di artikel tukang ojek online menang 200 juta dari Mahjong Ways 2.
deep dark web https://github.com/darkmarketlinkp22jr/darkmarketlink – deep web drug markets
http://slot88.company/# Kasino di Indonesia menyediakan hiburan yang beragam
the dark internet darkweb marketplace tor market url
dark web search engines black internet dark web link
darknet links dark web links drug markets onion
slot 88 slot88.company Slot menjadi bagian penting dari industri kasino
deep web drug url https://github.com/darknetwebsitesgflpx/darknetwebsites – dark web markets
Slot menawarkan berbagai jenis permainan bonus: bonaslot.site – bonaslot.site
hd rezka сериалы комедии на планшете резка фильмы фэнтези full hd бесплатно
Slot menawarkan berbagai jenis permainan bonus http://preman69.tech/# Kasino di Jakarta memiliki berbagai pilihan permainan
бонус с выводом без депозита фриспины бонус за регистрацию
https://prikashel.ru/stati/bezopasnost-i-tochnost-endoskopii-kak-sovremennye-kliniki-moskvy-provodyat-proceduru-bez-riska.html
Маркетплейс нового поколения https://x-nova.live уникальный сервис для удобных покупок и продаж. Интеллектуальный поиск, персонализированные рекомендации и безопасность сделок – все для вашего комфорта!
dark internet blackweb darknet links
tor markets 2022 https://github.com/darkmarketlinkp22jr/darkmarketlink – onion market
dark market dark web access dark web market list
bitcoin dark web https://github.com/darknetdruglinksvojns/darknetdruglinks – darkmarkets
darkmarket list dark web websites tor market url
dark web search engines darkmarket 2025 darkmarkets
darknet market lists dark web websites blackweb official website
UID_17136916###
Kisah inspiratif datang dari seorang tukang ojek online asal Tangerang yang berhasil membawa pulang hadiah fantastis setelah bermain Mahjong Ways 2. Dengan modal kecil, ia sukses mengubah nasibnya dan meraih kemenangan besar senilai 200 juta rupiah. Penasaran bagaimana caranya? Simak kisah lengkapnya di artikel tukang ojek online menang 200 juta dari Mahjong Ways 2.
https://garuda888.top/# Slot dengan bonus putaran gratis sangat populer
onion market dark web drug marketplace tor market
I had issues trying to download Metamask, but https://metamaker.org/#metamask-download explained everything in an easy way. Their guide is very detailed and useful.
dark markets 2025 dark market dark web drug marketplace
tor darknet dark market onion darkmarket url
Mesin slot menawarkan pengalaman bermain yang cepat https://slot88.company/# Kasino menyediakan layanan pelanggan yang baik
dark web link dark market list darkmarket link
Kasino menawarkan pengalaman bermain yang seru: BonaSlot – bonaslot.site
darknet markets 2025 dark web sites deep web markets
https://karavantver.ru/bronhoskopija-podgotovka-pokazanija-i-protivopokazanija/
darkmarket drug markets dark web tor market links
https://preman69.tech/# Pemain bisa menikmati slot dari kenyamanan rumah
dark market url darknet markets 2025 free dark web
tor darknet tor darknet darknet drug links
https://www.quora.com/Is-Del-Mar-Energy-Inc-a-legitimate-company
sex nhật hiếp dâm trẻ em ấu dâm buôn bán vũ khí ma túy bán súng sextoy chơi đĩ sex bạo lực sex học đường tội phạm tình dục chơi les đĩ đực người mẫu bán dâm
Зерновые культуры по выгодным ценам, опытный поставщик, узнать больше https://www.wpanet.org/profile/tveragroprom/profile
Slot menawarkan kesenangan yang mudah diakses http://slotdemo.auction/# Banyak pemain berusaha untuk mendapatkan jackpot
UID_87427935###
Cek yuk! 🚍👮♂️Operasi Keselamatan 2025 Polres Ciamis Siapa tahu bus favoritmu jadi sasaran! 😱👍
tk999 app tk999 app .
UID_87427935###
Cek yuk! 🚍👮♂️Operasi Keselamatan 2025 Polres Ciamis Siapa tahu bus favoritmu jadi sasaran! 😱👍
KU 9 KU 9 .
электрокарниз купить в москве электрокарниз купить в москве .
darknet marketplace dark market 2025 deep dark web
darkmarket darknet market links darknet market list
Kasino sering mengadakan turnamen slot menarik: slot 88 – slot88
tk999 login tk999 login .
KU9 casino KU9 casino .
гибкий электрокарниз привод elektrokarnizy77.ru .
preman69 slot preman69 Slot dengan tema budaya lokal menarik perhatian
dark website dark market onion tor markets
dark web sites darknet websites deep web links
dark web site darkmarkets tor market links
http://slot88.company/# Mesin slot baru selalu menarik minat
darknet markets dark web market links dark web access
Mesin slot sering diperbarui dengan game baru http://slotdemo.auction/# Jackpot progresif menarik banyak pemain
sex nhật hiếp dâm trẻ em ấu dâm buôn bán vũ khí ma túy bán súng sextoy chơi đĩ sex bạo lực sex học đường tội phạm tình dục chơi les đĩ đực người mẫu bán dâm
Важна скорость получения медицинской лицензии? Гарантируем оформление от 14 дней под ключ, информация здесь https://www.mapleprimes.com/users/MDLicenzii
tor marketplace how to get on dark web darknet market links
darknet markets 2025 dark markets 2025 darkmarket
dark market https://github.com/darknetwebsitesgflpx/darknetwebsites – darknet market list
dark web market links https://github.com/tormarkets2025ukaz1/tormarkets2025 – darkmarkets
darknet sites https://github.com/darknetdruglinksvojns/darknetdruglinks – darkweb marketplace
dark websites https://github.com/darkmarketlinkp22jr/darkmarketlink – drug markets dark web
deep web drug links https://github.com/darknetmarketlinks2025/darknetmarkets – tor markets
the dark internet dark internet darknet markets 2025
Slot klasik tetap menjadi favorit banyak orang: slot88.company – slot88
dark web links darknet markets 2025 dark web search engines
dark web sites dark web websites darknet site
darknet marketplace darknet websites darknet markets url
https://slot88.company/# Kasino selalu memperbarui mesin slotnya
darknet market links tor drug market
dark web sites dark websites
dark web marketplaces darkmarkets
Banyak pemain berusaha untuk mendapatkan jackpot http://slot88.company/# Slot dengan pembayaran tinggi selalu diminati
dark market onion darknet market
vrachi-urologi.ru https://viagramsk4.ru/ .
dark web markets dark markets dark market link
darknet websites dark market link dark web market links
dark web link darknet markets url darknet site
виагра мск виагра мск .
dark web market list darknet drugs
Jackpot besar bisa mengubah hidup seseorang: preman69.tech – preman69
darknet markets 2025 best darknet markets darkmarket
dark websites darkmarket
dark market onion darknet marketplace
dark web sites onion dark website darknet markets url
darknet market links dark markets tor drug market
bonaslot.site bonaslot.site Banyak pemain mencari mesin dengan RTP tinggi
Banyak pemain menikmati jackpot harian di slot https://garuda888.top/# Kasino sering mengadakan turnamen slot menarik
Why visitors still make use of to read news papers when in this technological world the whole thing is presented on net?
Attractive component to content. I simply stumbled upon your web site and in accession capital to say that I get in fact loved account your weblog posts. Anyway I will be subscribing in your feeds and even I fulfillment you get right of entry to persistently fast.
Wyoming Valley Equipment LLC
UID_18563832###
Ini yang di ganti >>> Yuk, ketahui lebih lanjut tentang Syarat Gabung OECD dan Pentingnya Ratifikasi Konvensi Antisuap di sini! 🕵️♀️🔎📚.
http://slotdemo.auction/# Mesin slot menawarkan berbagai tema menarik
I’ve recently started using mushroom extract gummies , and they’ve exceeded my expectations. From Delta 8 products to HHC products, the benefits are undeniable. They boost modify emphasis, promote have a zizz, and unvaried opulence slight aches. What I weakness most is that they’re natural and don’t leave me intuition groggy or absent from of it. The rank of hemp products makes a monumental contrast, so I perpetually look looking for trusted brands. Whether you’re brand-new to hemp or au fait, these products are a game-changer pro whole wellness.
darkmarket 2025 dark market onion
darknet markets onion darknet market
darknet market links dark market link dark web marketplaces
dark market 2025 onion dark website bitcoin dark web
bitcoin dark web dark markets 2025
dark market 2025 dark web market links darknet links
darknet markets onion bitcoin dark web darkmarkets
dark market dark web market list dark market
смотреть ужасы онлайн в хорошем качестве онлайн подборки фильмов
Современный маркетплейс https://nova7.top для выгодных покупок! Огромный ассортимент, лучшие цены и удобные способы оплаты. Покупайте качественные товары и заказывайте с быстрой доставкой!
Новый формат маркетплейса https://nova4.top быстро, удобно, надежно! Лучшие предложения, современные технологии и простой интерфейс. Покупайте и продавайте легко, экономя время и деньги!
Slot dengan bonus putaran gratis sangat populer: bonaslot.site – bonaslot.site
dark market dark web market list dark web market links
darknet drugs dark websites darkmarket 2025
darknet market list darknet markets onion
darknet drug market darknet markets onion darknet market links
darknet markets 2025 darknet sites darknet marketplace
dark web market list darknet drug links
Slot menjadi bagian penting dari industri kasino http://preman69.tech/# Kasino menawarkan pengalaman bermain yang seru
UID_18563832###
Ini yang di ganti >>> Yuk, ketahui lebih lanjut tentang Syarat Gabung OECD dan Pentingnya Ratifikasi Konvensi Antisuap di sini! 🕵️♀️🔎📚.
darknet market lists bitcoin dark web darknet markets onion address
http://preman69.tech/# Slot menjadi bagian penting dari industri kasino
darkmarket url dark web markets
darknet drug store dark market
darkmarket darkmarket list darkmarket
dark market link dark web market links
darknet sites dark web markets darknet markets onion address
darkmarket link darknet market dark market link
darkmarket dark web markets dark markets
dark web market links dark websites darknet drug links
Kasino sering mengadakan turnamen slot menarik: slot88.company – slot 88
Pemain sering mencoba berbagai jenis slot http://preman69.tech/# Permainan slot mudah dipahami dan menyenangkan
darknet market list darknet marketplace
darknet markets 2025 dark websites
darknet markets onion address darknet links darknet market links
darknet markets dark web market
darknet market lists darknet markets links dark market 2025
darknet markets links darkmarkets
http://preman69.tech/# Slot klasik tetap menjadi favorit banyak orang
Banyak pemain mencari mesin dengan RTP tinggi https://slot88.company/# Slot dengan bonus putaran gratis sangat populer
slot demo rupiah slot demo Mesin slot dapat dimainkan dalam berbagai bahasa
darkmarkets tor drug market tor drug market
Hello there! This post could not be written any better! Looking at this post reminds me of my previous roommate! He always kept talking about this. I am going to send this article to him. Pretty sure he’s going to have a very good read. Thanks for sharing!
Портал с ответами https://online-otvet.site по всем школьным домашним предметам. Наши эксперты с легкостью ответят на любой вопрос, и дадут максимально быстрый ответ.
Сауна очищает организм https://sauna-broadway.ru выводя токсины через пот, укрепляет иммунитет благодаря перепадам температуры, снимает стресс, расслабляя мышцы и улучшая кровообращение. Она делает кожу более упругой, ускоряет восстановление после тренировок, улучшает сон и создаёт атмосферу для общения.
darkmarket url dark web sites bitcoin dark web
Руководство по настройке https://amnezia.dev VPN-сервера! Пошаговые инструкции для установки и конфигурации безопасного соединения. Узнайте, как защитить свои данные и обеспечить анонимность в интернете. Настройте VPN легко!
dark web sites dark web link dark web link
tor drug market onion dark website darknet market
UID_83003169###
Kenalan yuk! 🤝 Dengan guru inspiratif ini, Guru Dede Sulaeman yang mengajarkan cara merapikan pakaian di kelasnya. 👕👚🎓
Kasino di Bali menarik banyak pengunjung http://bonaslot.site/# Pemain harus menetapkan batas saat bermain
Mesin slot menawarkan pengalaman bermain yang cepat: slot88.company – slot88.company
darkmarket 2025 darknet markets dark web market
darkmarket url darkmarket list darknet markets links
UID_83003169###
Kenalan yuk! 🤝 Dengan guru inspiratif ini, Guru Dede Sulaeman yang mengajarkan cara merapikan pakaian di kelasnya. 👕👚🎓
Real great information can be found on blog. “I am not merry but I do beguile The thing I am, by seeming otherwise.” by William Shakespeare.
https://garuda888.top/# Slot menjadi daya tarik utama di kasino
Православный форум https://prihozhanka.ru для женщин! Общение о вере, молитве, семье, воспитании и роли женщины в православии. Делитесь мыслями, находите поддержку и вдохновение в теплой атмосфере!
Korean cosmetics https://istinastroitelstva.xyz/user/michaett0/ perfect skin without effort! Innovative formulas, Asian traditions and visible results. Try the best skin care products right now!
Slot menawarkan kesenangan yang mudah diakses https://slotdemo.auction/# Mesin slot menawarkan pengalaman bermain yang cepat
Banyak kasino memiliki program loyalitas untuk pemain http://bonaslot.site/# Mesin slot digital semakin banyak diminati
dark market list dark web marketplaces dark market onion
dark market link onion dark website
darknet market darknet drug store
darkmarket 2025 dark web market dark market list
darknet markets onion darkmarket link
Slot dengan tema budaya lokal menarik perhatian: slot88 – slot88.company
darknet websites dark market url darknet markets url
preman69.tech preman69.tech Kasino memiliki suasana yang energik dan menyenangkan
darknet drugs onion dark website
Slot menjadi bagian penting dari industri kasino http://preman69.tech/# Mesin slot dapat dimainkan dalam berbagai bahasa
https://mebmw.com/resurs-i-problemy-dvigatelja-bmw-n46-18-nadezhnost-i-chastye-polomki/
dark web drug marketplace darkmarkets
http://zithropharm.com/# zithromax 500 mg lowest price online
https://audi1909.com/audi-a6-c8-30-tdi-kljuchevye-harakteristiki-i-osobennosti/
darkmarket link dark markets dark web marketplaces
doxycycline 100g: DoxHealthPharm – doxycycline tablets buy online
dark web link best darknet markets
darknet drug store darknet markets 2025
darknet links darknet markets onion
dark web market darknet markets 2025 dark web marketplaces
zithromax tablets: zithromax price south africa – zithromax z-pak
электрокарнизы для штор цена электрокарнизы для штор цена .
карниз электро карниз электро .
купить электрокарниз купить электрокарниз .
xxx teacher or student xxx teacher or student .
Your point of view caught my eye and was very interesting. Thanks. I have a question for you.
amoxicillin 500 mg price: AmoHealthPharm – amoxicillin 500mg capsule cost
карнизы с электроприводом купить карнизы с электроприводом купить .
карнизы для штор с электроприводом карнизы для штор с электроприводом .
электрокарнизы москва электрокарнизы москва .
dark markets onion dark website
hot teacher sex xxx hot teacher sex xxx .
darknet site dark market url darknet market links
darknet drugs darknet market lists
dark web market list darknet websites
https://clmhealthpharm.shop/# order generic clomid prices
dark web sites darknet markets
UID_97211224###
Yuk, sehat bersama! 👨⚕️👩⚕️ Cek kondisi tubuh kamu di Program Cek Kesehatan Gratis sekarang juga! 💉🌡️ Selalu jaga kesehatan, ya! 🏥💖
where can i get generic clomid no prescription: where to buy cheap clomid tablets – clomid brand name
карнизы для штор с электроприводом карнизы для штор с электроприводом .
dark web sites dark markets 2025 darknet links
Хочешь купить ПАВ в Москве? Нова маркетплейс – ищи в Яндекс!
Хочешь купить ПАВ в СПБ? Нова маркетплейс – ищи в Яндекс!
dark web market list dark market
dark market list darknet markets
UID_97211224###
Yuk, sehat bersama! 👨⚕️👩⚕️ Cek kondisi tubuh kamu di Program Cek Kesehatan Gratis sekarang juga! 💉🌡️ Selalu jaga kesehatan, ya! 🏥💖
darkmarket url darknet markets onion address
производители электрокарнизов производители электрокарнизов .
darknet markets dark web marketplaces
where to get generic clomid online: ClmHealthPharm – can i get clomid pill
where buy generic clomid without a prescription: get cheap clomid without a prescription – can i buy generic clomid without insurance
darknet markets url darkmarkets dark market list
zithromax 250 mg pill zithromax generic cost buy zithromax
dark web link dark web market
darknet markets onion dark markets 2025
https://zithropharm.com/# buy zithromax online cheap
darkmarket darkmarket bitcoin dark web
dark web sites dark market link
Надежный интернет-магазин прицелов с гарантией, всё чётко, заказал без сомнений – https://opticheskie-pricely-i-binokli.ru/
cost clomid pills: ClmHealthPharm – where can i get clomid
buy doxycycline australia: Dox Health Pharm – doxycycline prescription cost
dark market list darkmarket
darkmarket 2025 darkmarket
darkmarket 2025 darknet marketplace darkmarket 2025
darknet markets onion dark markets 2025
tor drug market dark web marketplaces
Купил бинокль с большим полем зрения, легко следить за движущимися объектами – https://opticheskie-pricely-i-binokli.ru/
darknet market list darkmarkets
UID_40226211###
Berita Hangat! 📰🔥 Bimbel Gratis Bagi Siswa SMAN 7 Cirebon yang Gagal SNBP! 😲🎓👍.
average cost of generic zithromax: ZithroPharm – zithromax 500 price
dark websites darknet drug store darknet links
dark market link dark web sites
dark market dark market
darknet market list dark web markets
http://zithropharm.com/# where can i buy zithromax medicine
darknet markets links darknet marketplace
dark web market links darknet site best darknet markets
amoxicillin in india: AmoHealthPharm – amoxicillin 50 mg tablets
darkmarket darkmarket 2025 darkmarket url
clomid brand name: can i purchase cheap clomid no prescription – can i get generic clomid pills
таблетки супрастин инструкция по применению https://allergiano.ru/ .
darknet markets darkmarket 2025
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
darknet market dark web drug marketplace
dark web sites dark web market
dark web sites darknet site onion dark website
zithromax over the counter uk where can you buy zithromax zithromax for sale 500 mg
how much is zithromax 250 mg: ZithroPharm – generic zithromax over the counter
dark web link darkmarkets
darknet drug market dark web markets
Hyundai Palisade 2021 года — идеальный кроссовер для семьи
https://prohyundai.com/
street light controller street light controller
Сауна очищает организм https://sauna-broadway.ru выводя токсины через пот, укрепляет иммунитет благодаря перепадам температуры, снимает стресс, расслабляя мышцы и улучшая кровообращение. Она делает кожу более упругой, ускоряет восстановление после тренировок, улучшает сон и создаёт атмосферу для общения.
dark web link dark web drug marketplace
amoxicillin 1000 mg capsule: 875 mg amoxicillin cost – where can i buy amoxocillin
профессиональный лечебный массаж Ивантеевка расслабляющие техники для здоровья и красоты. Помогаем снять стресс, улучшить кровообращение и восстановить силы. Запишитесь прямо сейчас!
dark market darknet markets 2025 darknet markets links
darknet market links dark markets
https://clmhealthpharm.shop/# how can i get cheap clomid price
Мы возьмем на себя все заботы, чтобы вы могли проститься с близким достойно https://pohoronnoe-agentstvo.kz/
darkmarket list darknet drug market
darkmarket link darknet markets onion address darknet market lists
darknet links dark market onion
buy amoxicillin without prescription: AmoHealthPharm – where can i buy amoxicillin online
I’ve recently started using https://elevateright.com/product/500mg-peach-lemonade-amanita-mushroom-gummies/ , and they’ve exceeded my expectations. From Delta 8 products to HHC products, the benefits are undeniable. They help break down stress, promote slumber, and unvaried opulence minor aches. What I ardour most is that they’re natural and don’t commit me feeling numb or absent from of it. The rank of hemp products makes a tremendous contrast, so I perpetually look for trusted brands. Whether you’re new to hemp or savvy, these products are a game-changer for overall wellness.
dark web drug marketplace darkmarket link
https://mmitsibishi.com/
can i get cheap clomid no prescription: ClmHealthPharm – how can i get cheap clomid for sale
dark web market links darknet websites
https://mmitsibishi.com/
darknet drug store darknet drug links dark web markets
darknet drug market darknet drug links
where to buy amoxicillin pharmacy: Amo Health Pharm – antibiotic amoxicillin
I’ve recently started using mushroom gummies , and they’ve exceeded my expectations. From Delta 8 products to HHC products, the benefits are undeniable. They cure break down lay stress, recondition catnap, and despite that smooth opulence penny-ante aches. What I weakness most is that they’re non-chemical and don’t commit me feeling groggy or elsewhere of it. The dignity of hemp products makes a tremendous contrast, so I perpetually look looking for trusted brands. Whether you’re restored to hemp or au fait, these products are a game-changer for complete wellness.
электрокарнизы цена электрокарнизы цена .
карниз для штор электрический карниз для штор электрический .
карниз электро карниз электро .
darknet market lists darknet markets 2025
электрические гардины электрические гардины .
organic full spectrum cbd oil present a convenient and enjoyable route to experience the effects of this compound. These gummies fingers on in diverse flavors, potencies, and formulations, providing users with controlled dosing and long-lasting effects. Divers consumers rise them for moderation, stress relief. Degree, it’s prominent to consume them responsibly, as effects may take longer to kick in compared to smoking or vaping. Everlastingly check dosage guidelines and ensure compliance with nearby laws in the forefront purchasing or consuming.
игровые автоматы с бесплатным депозитом игровые автоматы промокод
карниз с электроприводом карниз с электроприводом .
прокарниз prokarniz34.ru .
http://zithropharm.com/# zithromax canadian pharmacy
darknet market list onion dark website dark market onion
Женский онлайн портал https://brjunetka.ru для вдохновения! Полезные советы по стилю, уходу за собой, здоровью и семейной жизни. Будьте в курсе трендов, находите мотивацию и делитесь опытом!
Портал с ответами https://online-otvet.site на все школьные предметы! Быстро находите решения по математике, русскому, физике, биологии и другим дисциплинам. Готовые ответы, разборы задач и помощь в учебе для всех классов
dark market url darknet markets url
Комплексное сопровождение похорон – от оформления документов до захоронения https://pohoronnoe-agentstvo.kz/
darknet drug store darknet market lists
can you buy zithromax over the counter: where can i get zithromax over the counter – generic zithromax over the counter
dark market url best darknet markets
can i purchase clomid price: can i get cheap clomid now – where to buy generic clomid
buy cheap doxycycline uk Dox Health Pharm how much is doxycycline in south africa
boost of subscribers without unsubscribes best smm panel
Элитный коттеджный поселок https://parkville-zhukovka-poselok.ru в Жуковке! Просторные дома, свежий воздух, развитая инфраструктура и удобная транспортная доступность. Создайте уютное пространство для жизни в живописном месте!
https://telegra.ph/HD-Kazino-Luchshie-igrovye-avtomaty-dlya-nezabyvaemyh-pobed-02-14 –
играть в автоматы в хорошем качестве
stehovani Ostrava stehovani maleho bytu
dark web market darknet markets 2025
dark web markets dark web market links
dark market onion darkmarket 2025
cheap doxycycline 100mg capsule: 10 mg doxycycline – doxycycline 100mg capsules buy
El codigo promocional 1xBet 2025: “1XBUM” brinda a los nuevos usuarios un bono del 100% hasta $130. Ademas, el codigo promocional 1xBet de hoy permite acceder a un atractivo bono de bienvenida en la seccion de casino, que ofrece hasta $2275 USD (o su equivalente en VES) junto con 150 giros gratis. Este codigo debe ser ingresado al momento de registrarse en la plataforma para poder disfrutar del bono de bienvenida, ya sea para apuestas deportivas o para el casino de 1xBet. Los nuevos clientes que se registren utilizando el codigo promocional tendran la oportunidad de beneficiarse de la bonificacion del 100% para sus apuestas deportivas.
Utiliza el codigo de bonificacion de 1xCasino: “1XBUM” para obtener un bono VIP de hasta €1950 mas 150 giros gratis en el casino y un 200% hasta €130 en apuestas deportivas. Introduce nuestro codigo promocional para 1x Casino 2025 en el formulario de registro y reclama bonos exclusivos para el casino y las apuestas deportivas. Bonificacion sin deposito de 1xCasino de $2420. Es necesario registrarse, confirmar tu correo electronico e ingresar el codigo promocional.
codigo promocional 1xCasino moz
darknet drug links dark web link
https://amohealthpharm.com/# where can you get amoxicillin
dark market onion darknet drugs
darknet market list dark web marketplaces
cost of generic clomid price: can you buy generic clomid pill – can you buy clomid without insurance
darknet markets darkmarket link
generic clomid without rx: where can i buy clomid pills – get generic clomid no prescription
darkmarket list dark market onion
dark web market dark market onion
darkmarkets dark websites
darknet markets links tor drug market
Your style is very unique in comparison to other people I’ve read stuff from.
Thank you for posting when you’ve got the opportunity, Guess
I’ll just book mark this web site. https://unlim-casinodynasty.lol/
Do you have a spam problem on this site; I also am a blogger, and I was wanting to know your situation; many of us have developed some nice procedures and we are looking to trade methods with other folks, be sure to shoot me an email if interested.
Check out my homepage :: https://penzu.com/p/b31b2681
boost of subscribers instagram boost of likes
Все о строительстве https://decor-kraski.com.ua и ремонте в одном месте! Подробные инструкции, идеи для дизайна, выбор материалов и советы мастеров. Сделайте свой дом удобным, стильным и долговечным!
dark market link darkmarkets
darknet markets links dark market list
Портал про строительство https://goodday.org.ua и ремонт! Полезные советы, обзоры материалов, технологии строительства, лайфхаки для дома. Узнайте, как сделать ремонт качественно и сэкономить на строительных работах!
cheapest doxycycline uk: buy doxycycline from canada – doxycycline hyclate
amoxicillin 500mg: amoxacillian without a percription – amoxicillin without prescription
https://clmhealthpharm.com/# order cheap clomid
шторы с электроприводом и дистанционным управлением шторы с электроприводом и дистанционным управлением .
best darknet markets darknet market links
dark web market darknet markets url
рулонные шторы на пластиковые окна с электроприводом рулонные шторы на пластиковые окна с электроприводом .
электрические шторы электрические шторы .
darknet site dark market url
рулонные шторы с электроприводом купить https://www.prokarniz13.ru .
buy amoxicillin online mexico amoxicillin 500 mg amoxicillin canada price
dark market list dark market onion
amoxicillin 825 mg: Amo Health Pharm – amoxicillin 500mg tablets price in india
darknet markets onion address darknet sites
https://xn--2i0bm4pssb87h9pkd4y3jb.mystrikingly.com/blog/3731e9afa8a
darknet drug links darknet links
Ремонт и строительство https://inbound.com.ua без хлопот! Полезные лайфхаки, новинки в дизайне, технологии строительства и подбор лучших материалов. Создайте комфортное жилье легко и выгодно!
Портал для строителей https://hotel.kr.ua и домашних мастеров! Полезные статьи, новинки рынка, лайфхаки по ремонту и рекомендации по выбору качественных материалов.
Ваш надежный помощник https://insurancecarhum.org в ремонте! Практичные советы, инструкции и секреты профессионалов. Узнайте, как сделать качественный ремонт и выбрать лучшие строительные материалы!
buy amoxicillin 500mg capsules uk: AmoHealthPharm – buy amoxicillin 500mg usa
dark market link dark market url
darkmarket list darkmarket
электрические римские шторы электрические римские шторы .
электрокарниз somfy электрокарниз somfy .
darknet market links onion dark website
автоматические римские шторы автоматические римские шторы .
https://clmhealthpharm.shop/# where can i buy generic clomid pill
where to get generic clomid without prescription: order clomid price – get cheap clomid without rx
somfy shop http://www.prokarniz25.ru .
Инструкции по ремонту https://makprestig.in.ua подбор материалов, планирование, дизайн и советы экспертов. Станьте мастером своего дома!
Лучший портал по строительству https://itstore.dp.ua и ремонту! Гайды по отделке, рекомендации экспертов, новинки дизайна и проверенные решения. Все для вашего комфорта!
tor drug market darknet site
Как сделать ремонт https://oo.zt.ua правильно? Наш портал поможет выбрать материалы, спланировать бюджет и создать уютный интерьер. Простые решения для сложных задач!
darkmarkets dark markets 2025
https://hallbook.com.br/blogs/313001/%EB%84%A4%EC%9D%B4%EB%B2%84-%EC%95%84%EC%9D%B4%EB%94%94-%EA%B5%AC%EB%A7%A4-%EC%9D%B4%EB%9F%B4-%EB%95%90-%EC%A3%BC%EC%9D%98%ED%95%98%EC%84%B8%EC%9A%94
dark web market links dark web drug marketplace
amoxicillin 500mg without prescription: Amo Health Pharm – amoxicillin 500 capsule
doxycycline over the counter nz: doxy 100 – doxycycline canada
darknet links dark web link
https://naveridbuy.blogspot.com/2024/09/blog-post_8.html
Irwin casino промокод
Irwin casino промокод
Регулярные акции и турниры позволяют оставаться в курсе всех новинок. Для этого достаточно отсканировать QR-код на сайте или скачать файл напрямую? Существует множество акций, позволяя им исследовать возможности казино и начать свои игровые приключения без первоначальных финансовых вложений. Благодаря интуитивно понятному интерфейсу, релоады. Владелец online проекта предоставляет услуги на основании лицензии, в целях обхода блокировки казино online создаются домены-копии. Эти уникальные предложения делают игровой процесс не только более интересным, подходящий для любых экранов Быстрый доступ к играм и функциям Поддержка всех популярных операционных систем.
irwin casino промокод
Процесс пополнения счета очень прост и быстр. Также оно позволяет вернуться в клуб в случае перегрузки серверов или проведения работ по улучшению и обновлению софта. Телефонная линия для тех, игровая площадка является одной из лидеров в сфере азартных игр в России.
ирвин казино официальный сайт
Каждый новый клиент Ирвин Казино получит беездепозитный бонус по промокоду с бесплатными вращениями. После этого уже крутите барабаны на деньги с выводом, и предлагает гостям протестировать новинки одними из первых, что гарантирует безопасность и стабильность работы, поможет вам наглядно спланировать свою игровую стратегию, подтверждающие честность и прозрачность предлагаемых продуктов. Регистрация и активация бонуса проходят быстро и легко, что эти ответы помогли вам лучше понять.
darknet markets onion dark website
Профессиональные советы https://ukk.kiev.ua по ремонту и строительству! Пошаговые инструкции, актуальные тренды и лучшие решения для обустройства вашего жилья.
Идеи для дома https://ucmo.com.ua ремонта и строительства! Полезные советы, лайфхаки и современные технологии, которые помогут сделать ремонт качественно и доступно.
Ремонт без стресса https://panorama.zt.ua Готовые решения, полезные лайфхаки, выбор материалов и идеи для дома. Делаем ремонт комфортным и доступным!
купить межкомнатные двери в москве
darknet markets onion darkmarket
darknet drugs bitcoin dark web
https://clmhealthpharm.shop/# where can i get cheap clomid without insurance
dark markets darknet sites
generic zithromax 500mg [url=https://zithropharm.shop/#]Zithro Pharm[/url] zithromax capsules 250mg
Идеи для дома https://ucmo.com.ua ремонта и строительства! Полезные советы, лайфхаки и современные технологии, которые помогут сделать ремонт качественно и доступно.
doxycycline 2014: doxycycline 75 mg cost – doxycycline 100mg without prescription
Делаем ремонт правильно https://zarechany.zt.ua Разбираем все этапы – от выбора материалов до дизайна интерьера. Подробные инструкции и лайфхаки от специалистов!
https://xn--w6-o02ik82a9kav54aokmxvc.mystrikingly.com/blog/23a370b4a45
Автомобильный портал https://nerjalivingspace.com для автолюбителей! Новости автоиндустрии, обзоры автомобилей, тест-драйвы, полезные советы по ремонту и тюнингу. Будьте в курсе последних трендов и находите ответы на все авто-вопросы!
darkmarket link dark market 2025
price for amoxicillin 875 mg: can i buy amoxicillin online – amoxicillin 500mg for sale uk
darkmarket url dark market 2025
tor drug market darknet drugs
where can i buy generic clomid without insurance: how to buy generic clomid – cheap clomid now
darkmarket dark market link
dark market darkmarket url
darknet marketplace darknet sites
dark market onion dark market onion
Все для женщин https://elegance.kyiv.ua в одном месте! Секреты красоты, советы по стилю, отношениям, психологии, здоровью и кулинарии. Будьте вдохновленными и уверенными каждый день!
Женский портал https://beautyadvice.kyiv.ua для современной женщины! Мода, красота, здоровье, отношения, кулинария и карьера. Полезные советы, тренды и вдохновение для тех, кто хочет быть в курсе новинок и заботиться о себе!
Онлайн мир женщины https://gracefullady.kyiv.ua красота, здоровье, успех! Полезные лайфхаки, тренды моды, секреты счастья и гармонии. Портал для тех, кто хочет быть лучшей версией себя!
darknet market links dark market link
https://clmhealthpharm.com/# where can i get cheap clomid without prescription
darknet drugs dark web marketplaces
1вин кг http://1win3.com.kg .
Хотите https://https://telegra.ph/Tajnye-tropy-darkneta-kak-ya-kupil-yad-dlya-cheloveka-02-13/ – купить цианистый калий недорого?
doxycycline brand name canada: Dox Health Pharm – doxycycline 100mg cap price
1win вход официальный сайт https://1win3.com.kg .
dark web drug marketplace darknet markets links
dark web market dark market onion
Портал для современной https://femaleguide.kyiv.ua женщины! Открой для себя новые идеи в моде, красоте, отношениях и саморазвитии. Полезные статьи и советы для комфортной и счастливой жизни
Мир женщины https://fashionadvice.kyiv.ua красота, здоровье, успех! Полезные лайфхаки, тренды моды, секреты счастья и гармонии. Портал для тех, кто хочет быть лучшей версией себя!
Твой гид в мире https://happywoman.kyiv.ua женственности и гармонии! Узнай больше о моде, косметике, фитнесе, отношениях и мотивации. Все, что нужно для яркой и счастливой жизни!
zithromax 1000 mg pills: Zithro Pharm – cost of generic zithromax
amoxicillin 500 mg brand name: Amo Health Pharm – amoxicillin 500 mg capsule
dark markets darknet market lists
dark web drug marketplace darknet markets onion address
https://naveridbuy.blogspot.com/2024/09/blog-post_19.html
Ko66 là một trong những nền tảng nổi bật nhất năm 2025, thu hút sự quan tâm của hàng triệu người chơi nhờ hệ thống hiện đại và dịch vụ chất lượng.
dark markets 2025 dark web drug marketplace
https://naveridbuy.exblog.jp/35891786/
https://gajweor.pixnet.net/blog/post/162874615
https://169.ru/mezhkomnatnye-dveri/
buy cheap generic zithromax where can i buy zithromax uk where can i buy zithromax uk
1вин кг https://1win4.com.kg/ .
1win pro http://www.1win5.com.kg .
http://clmhealthpharm.com/# can you get clomid no prescription
1vin kg https://www.1win4.com.kg .
buy doxycycline 200 mg: DoxHealthPharm – doxycycline 100mg without prescription
sex nhật hiếp dâm trẻ em ấu dâm buôn bán vũ khí ma túy bán súng sextoy chơi đĩ sex bạo lực sex học đường tội phạm tình dục chơi les đĩ đực người mẫu bán dâm
order doxycycline online: doxycycline 100g – how can i get doxycycline
price of amoxicillin without insurance: can i buy amoxicillin over the counter – amoxicillin 500mg capsule cost
1 вин официальный сайт вход https://www.1win6.com.kg .
mostbet kg mostbet kg .
Актуальные зеркала BlackSprut https://kra26.cat Заходите без проблем, обходите блокировки и пользуйтесь сайтом без VPN. Мы следим за обновлениями и всегда предоставляем свежие ссылки.
Безопасный доступ к сайту https://bsme-at.at без ограничений. Рабочие зеркала позволяют обходить блокировки без VPN, обеспечивая стабильную связь и удобный интерфейс. Следите за обновлениями, чтобы всегда оставаться в сети.
Всегда актуальные ссылки https://bs2bet.at для входа. Обходите блокировки легко и быстро, используя надёжные зеркала. Свежие обновления позволяют заходить без VPN и сохранять полную анонимность.
Проблемы с входом https://bs2best.or.at Найдите актуальные зеркала и заходите без ограничений. Мы обновляем ссылки ежедневно, обеспечивая быстрый и безопасный доступ без необходимости использования VPN.
1win официальный сайт вход с компьютера https://www.1win6.com.kg .
mostbet скачать на андроид http://www.mostbet1.com.kg .
http://amohealthpharm.com/# amoxicillin 500mg capsules antibiotic
discount doxycycline: doxcyclene – antibiotics doxycycline
BlackSprut это инновационный https://bs2best.cat маркетплейс с расширенным функционалом и полной анонимностью пользователей. Современные технологии защиты данных, удобный интерфейс и высокая скорость обработки заказов делают покупки безопасными и простыми. Покупайте без риска и продавайте с максимальной выгодой на BlackSprut!
BlackSprut крупнейший маркетплейс https://bb2best.at где можно найти всё, что вам нужно. Надёжная система безопасности, удобная навигация, широкий ассортимент товаров. Анонимные покупки, моментальные сделки и выгодные условия для продавцов.
BlackSprut передовой маркетплейс https://m-bsme.at с высокими стандартами безопасности и удобной системой поиска. Анонимность, быстрая оплата и честные продавцы – всё, что нужно для комфортных покупок. Мы гарантируем защиту ваших данных и качественное обслуживание. Присоединяйтесь к BlackSprut и открывайте новые возможности!
Professional painting services https://www.seattlesbestpainters.com for offices and industrial facilities. We will update the interior of your office or perform high-quality painting of production facilities, warehouses, hangars.
0mgq7i
darknet markets links dark market url
darkmarket list dark web market list
pharmacie en ligne pas cher: Pharmacies en ligne certifiees – Pharmacie en ligne livraison Europe
проверенный маркетплейс https://bsme.cat предлагающий товары на любой вкус. Простая регистрация, быстрая оплата и защита сделок. Убедитесь в качестве сервиса сами!
pharmacie en ligne france livraison internationale kamagra oral jelly pharmacie en ligne france livraison internationale
Blacksprut – современная площадка https://bs-bsme.at для безопасных покупок. Большой выбор категорий, продуманная система рейтингов и отзывов. Заходите и находите нужное легко!
acheter mГ©dicament en ligne sans ordonnance: pharmacie en ligne france – п»їpharmacie en ligne france
Blacksprut – онлайн-маркетплейс https://bsmc.at с лучшими предложениями. Надёжные продавцы, защищённые сделки, удобный поиск. Оцените удобство покупок уже сегодня!
Ищете актуальные бонусы без отыгрыша? Мы собираем лучшие предложения: фриспины, бонусы за депозит, бездепозитные акции и кэшбэк. Получите максимум выгоды от игры!
https://pharmaciemeilleurprix.shop/# vente de mГ©dicament en ligne
pharmacies en ligne certifiГ©es
dark web link darknet market lists
darknet market lists dark market 2025
darkmarket darkmarkets
pharmacie en ligne sans ordonnance http://tadalafilmeilleurprix.com/# Pharmacie en ligne livraison Europe
darknet drug store dark markets 2025
Replica Uhren https://www.imailen.com in Deutschland schnell und sicher per DHL Nachnahme bestellen. Nur geprufte Qualitat in EU hergestellt.
купить сферы возвышения poe 2 купить divine пое 2
Журнал об автомобилях https://setbook.com.ua всё для автолюбителей! Последние автоновости, обзоры моделей, тест-драйвы, советы по ремонту, тюнингу и обслуживанию. Узнайте всё о мире автомобилей!
Главный авто-журнал https://myauto.kyiv.ua для водителей! Новости, обзоры, сравнения, тюнинг, автоспорт и технологии. Будьте в курсе последних трендов автомобильного мира!
darknet markets url dark websites
dark market link darknet markets onion address
pharmacie en ligne livraison europe: pharmacie en ligne france – acheter mГ©dicament en ligne sans ordonnance
dark web market links dark websites
best darknet markets dark markets
darknet drugs darkmarket 2025
Viagra 100 mg sans ordonnance: acheter du viagra – Viagra homme prix en pharmacie sans ordonnance
Все об автомобилях https://allauto.kyiv.ua в одном журнале! Новости автопрома, тест-драйвы, обзоры моделей, советы по ремонту и тюнингу, страхование и ПДД.
Журнал для автолюбителей https://myauto.kyiv.ua и профессионалов! Всё о новых моделях, технологии, автоспорт, лайфхаки по уходу за авто и экспертные рекомендации.
Журнал об авто https://auto-club.pl.ua для тех, кто за рулем! Новости автопрома, тест-драйвы, рекомендации по выбору авто, советы по ремонту и эксклюзивные интервью с экспертами.
https://kamagrameilleurprix.shop/# pharmacie en ligne pas cher
pharmacie en ligne france pas cher
pharmacie en ligne pas cher https://viagrameilleurprix.shop/# Viagra en france livraison rapide
darknet site dark websites
darkmarket url darknet market
dark market 2025 best darknet markets
darknet drug market darknet markets url
pharmacie en ligne france pas cher Acheter Cialis trouver un mГ©dicament en pharmacie
pharmacie en ligne: kamagra livraison 24h – pharmacie en ligne sans ordonnance
dark web market urls dark market link
dark market onion darknet markets onion
dark market 2025 darknet websites
pharmacie en ligne fiable: kamagra oral jelly – acheter mГ©dicament en ligne sans ordonnance
dark markets 2025 dark web market urls
https://pharmaciemeilleurprix.com/# pharmacie en ligne pas cher
pharmacie en ligne france livraison internationale
pharmacie en ligne sans ordonnance http://tadalafilmeilleurprix.com/# pharmacie en ligne livraison europe
pharmacie en ligne: Pharmacies en ligne certifiees – pharmacie en ligne fiable
darknet markets links dark market onion
dark market url darknet markets
мос бет мос бет .
мосьет мосьет .
darknet markets dark web marketplaces
dark web link onion dark website
vjcn,tn vjcn,tn .
https://kind-seal-dc4vlj.mystrikingly.com/blog/df23e8badcf
мост бет букмекерская контора мост бет букмекерская контора .
darknet markets url darknet site
dark web link dark web sites
sex nhật hiếp dâm trẻ em ấu dâm buôn bán vũ khí ma túy bán súng sextoy chơi đĩ sex bạo lực sex học đường tội phạm tình dục chơi les đĩ đực người mẫu bán dâm
onion dark website dark web market list
pharmacie en ligne: pharmacie en ligne – pharmacies en ligne certifiГ©es
darknet drug store dark web sites
Все о машинах https://autoinfo.kyiv.ua в одном журнале! Свежие автоновости, сравнения моделей, экспертные рекомендации, автоспорт и полезные советы для автомобилистов.
Журнал для автолюбителей https://avtoshans.in.ua и профессионалов! Узнайте все о новых авто, электрокарах, страховании, тюнинге и современных технологиях в автомобилях.
Автомобильный мир https://diesel.kyiv.ua в одном журнале! Разбираем новинки автопрома, анализируем технические характеристики, тестируем авто и делимся советами по ремонту.
Viagra prix pharmacie paris: Acheter Viagra Cialis sans ordonnance – Viagra sans ordonnance 24h suisse
http://pharmaciemeilleurprix.com/# trouver un mГ©dicament en pharmacie
pharmacie en ligne france pas cher
Pharmacie Internationale en ligne https://viagrameilleurprix.shop/# Viagra sans ordonnance pharmacie France
dark market darknet drug store
dark markets dark web link
darkmarket list darknet markets 2025
darknet drug market dark market url
pharmacie en ligne france livraison internationale Pharmacie Internationale en ligne pharmacie en ligne fiable
https://medium.com/@dqvchristopherwhite824/%EB%84%A4%EC%9D%B4%EB%B2%84-%EC%95%84%EC%9D%B4%EB%94%94-%EB%B3%80%EA%B2%BD-%EB%B0%8F-%EC%97%85%EB%8D%B0%EC%9D%B4%ED%8A%B8-%EB%B0%A9%EB%B2%95-ce084c6a8429
bitcoin dark web darknet market links
Современный автомобильный https://k-moto.com.ua журнал! Читайте о трендах в автоиндустрии, новейших моделях, электромобилях, тюнинге и умных технологиях.
Автомобильный журнал https://orion-auto.com.ua только важные новости! Все о популярных марках, топовые авто 2024 года, электрокары, автономное вождение и тенденции рынка.
Журнал о машинах https://reuth911.com для настоящих ценителей авто! Обзоры, рейтинги, полезные статьи о ремонте, тюнинге и современных автомобильных технологиях.
Автомобильный мир https://prestige-avto.com.ua в одном журнале! Разбираем новинки автопрома, анализируем технические характеристики, тестируем авто и делимся советами по ремонту.
мостбет зеркало http://mostbet2.com.kg/ .
darknet site darknet market lists
dark web market list dark web market urls
pharmacie en ligne: pharmacie en ligne france – pharmacie en ligne pas cher
darkmarket link darknet markets onion
dark market url dark web drug marketplace
мостбет ком мостбет ком .
I’ve been using orange gummies thc for a while instantly, and they’ve creditably been a game-changer against stress and sleep. The excellent part? No grogginess in the morning honourable a cool off, pacific feeling in the vanguard bed. Supplementary, they bit extraordinary, unlike some other supplements I’ve tried. I was skeptical at elementary, but after devotedly using them, I can indubitably bruit about they help with unwinding after a sustained day. If you’re looking on a reasonable means to iciness without any weird side effects, CBD gummies are advantage trying. Honest get sure you get a grade trade name with third-party testing!
dark web drug marketplace onion dark website
Viagra homme prix en pharmacie: Viagra pas cher inde – Viagra 100 mg sans ordonnance
pharmacie en ligne avec ordonnance https://tadalafilmeilleurprix.shop/# pharmacie en ligne livraison europe
http://pharmaciemeilleurprix.com/# Pharmacie Internationale en ligne
vente de mГ©dicament en ligne
darknet websites darknet websites
dark market url darkmarket link
darkmarkets dark web markets
darknet markets onion address tor drug market
sp5der hoodie website sp5der hoodie website .
darknet market lists dark web sites
brown sp5der hoodie spiderhoodie-us.com/spider-hoodies .
Pharmacie sans ordonnance: pharmacie en ligne sans ordonnance – acheter mГ©dicament en ligne sans ordonnance
Твой авто-гид https://troeshka.com.ua в мире машин! Обзоры новых моделей, тест-драйвы, советы по ремонту и тюнингу, автоновости и технологии будущего. Все, что нужно автолюбителю!
Все об автомобилях https://tvk-avto.com.ua на одном портале! Новинки мирового автопрома, тест-драйвы, автострахование, электрокары и полезные статьи для каждого водителя.
Журнал про автолюбители https://tuning-kh.com.ua новости, тесты, обзоры! Узнайте все о лучших авто, их характеристиках, стоимости владения, экономии топлива и новинках автопрома.
Твой идеальный женский https://family-site.com.ua журнал! Секреты ухода, стильные образы, рецепты, психология и лайфхаки для яркой и успешной жизни. Вдохновение каждый день!
darknet markets darknet marketplace
darknet market darknet market lists
darkmarket link dark websites
Нужен сантехник в Минске? Мы осуществляем замену и установку с гарантией результата. Наши квалифицированные мастера готовы провести качественный ремонт. Получите подробности на сантехник недорого минск.
dark market link bitcoin dark web
pharmacie en ligne: kamagra oral jelly – pharmacie en ligne pas cher
dark market list https://github.com/darknetdruglinksvojns/darknetdruglinks
pharmacie en ligne france livraison belgique https://viagrameilleurprix.shop/# Viagra sans ordonnance 24h Amazon
Achat mГ©dicament en ligne fiable Acheter Cialis pharmacie en ligne france livraison belgique
Актуальные новости https://www.moscow.regnews.info Московского региона! Все главные события, политика, экономика, транспорт, ЖКХ, происшествия и культурные события. Будьте в курсе того, что происходит в вашем городе!
Prix du Viagra 100mg en France: Viagra pharmacie – Viagra homme prix en pharmacie sans ordonnance
Главный женский журнал https://amideya.com.ua о стиле и успехе! Полезные статьи о моде, косметике, питании, спорте, семейных ценностях и личностном росте. Читай и развивайся вместе с нами!
Твой идеальный женский https://femalesecret.kyiv.ua журнал! Секреты ухода, стильные образы, рецепты, психология и лайфхаки для яркой и успешной жизни. Вдохновение каждый день!
https://kamagrameilleurprix.shop/# Pharmacie Internationale en ligne
п»їpharmacie en ligne france
Портал для женщин https://feminine.kyiv.ua твой путеводитель в мире стиля и успеха! Узнай секреты красоты, лайфхаки по уходу, новинки моды, советы по психологии, карьере и семье.
darknet markets https://github.com/darknetmarketlinks2025/darknetmarkets
darknet markets onion address https://github.com/darknetwebsitesgflpx/darknetwebsites
darkmarket url https://github.com/darkmarketlinkp22jr/darkmarketlink
dark web markets https://github.com/tormarkets2025ukaz1/tormarkets2025
dark market https://github.com/darknetdruglinksvojns/darknetdruglinks
Нужны финансы срочно? Получите онлайн-заем на дебетовую карту за короткий срок. https://zaym-bez-proverok.ru/ Оформите онлайн-заявку без подтверждений и получите апробацию уже сегодня!
https://maps.google.com.ai/url?q=https://lineage4free.ru –
слоты в hd качестве
Твой женский портал https://girl.kyiv.ua о стиле и гармонии! Узнай секреты ухода, тренды в моде, лайфхаки для красоты, советы по отношениям и карьерному росту.
купить меф тольятти детское порно ххх
Главный женский портал https://horoscope-web.com будь в центре трендов! Читай актуальные статьи о моде, косметике, личных финансах, женском здоровье, семье и личностном росте.
Портал для женщин https://lolitaquieretemucho.com которые ценят себя! Полезные статьи о здоровье, семье, саморазвитии, психологии, фитнесе и рецептах. Будь уверенной, счастливой и успешной!
dark market link https://github.com/darknetmarketlinks2025/darknetmarkets
darknet markets links https://github.com/darknetwebsitesgflpx/darknetwebsites
darkmarket list https://github.com/darkmarketlinkp22jr/darkmarketlink
dark market 2025 https://github.com/tormarkets2025ukaz1/tormarkets2025
Pharmacie Internationale en ligne: kamagra livraison 24h – pharmacie en ligne pas cher
Viagra homme prix en pharmacie sans ordonnance: Acheter Viagra Cialis sans ordonnance – Viagra femme sans ordonnance 24h
pharmacie en ligne avec ordonnance https://pharmaciemeilleurprix.com/# vente de mГ©dicament en ligne
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
https://viagrameilleurprix.shop/# Viagra 100mg prix
pharmacie en ligne france livraison belgique
Viagra gГ©nГ©rique sans ordonnance en pharmacie: viagra sans ordonnance – Viagra sans ordonnance 24h suisse
Как заменить турбину на машине и не переплатить втрое больше. Типичная схема развода на замену турбины. Будьте осторожны. Подробности тут Как заменить турбину на машине и не переплатить втрое больше. Типичная схема развода на замену турбины. Будьте осторожны. Подробности тут .
проведение соут москва проведение соут москва .
Логические задачи для детей http://www.raskraska1.ru .
Как заменить турбину на машине и не переплатить втрое больше. Типичная схема развода на замену турбины. Будьте осторожны. Подробности тут Как заменить турбину на машине и не переплатить втрое больше. Типичная схема развода на замену турбины. Будьте осторожны. Подробности тут .
дистанционная специальная оценка условий труда дистанционная специальная оценка условий труда .
Пословицы и поговорки для детей Пословицы и поговорки для детей .
Портал для женщин https://nicegirl.kyiv.ua которые любят себя! Стиль, здоровье, отношения, психология и полезные советы для тех, кто хочет оставаться красивой и успешной.
Твой путеводитель https://mirlady.kyiv.ua в мире женских секретов! Советы по стилю, кулинарии, фитнесу, материнству, личному росту и здоровью. Всё, что нужно для счастливой жизни!
Современный женский портал https://presslook.com.ua Все о красоте, моде, женском здоровье, отношениях, саморазвитии и карьере. Читай, вдохновляйся и меняй свою жизнь к лучшему!
Твой идеальный https://prettywoman.kyiv.ua женский портал! Секреты красоты, тренды моды, лайфхаки по уходу за собой, психология отношений, советы по материнству и карьерному росту.
Pharmacie Internationale en ligne kamagra livraison 24h п»їpharmacie en ligne france
pharmacie en ligne sans ordonnance: cialis prix – trouver un mГ©dicament en pharmacie
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
п»їpharmacie en ligne france https://pharmaciemeilleurprix.shop/# п»їpharmacie en ligne france
pharmacie en ligne livraison europe: Tadalafil sans ordonnance en ligne – trouver un mГ©dicament en pharmacie
Wi88 là nhà cái thể thao uy tín, gây ấn tượng mạnh trong cộng đồng game thủ Việt Nam nhờ vào hệ thống cá cược hiện đại, đa dạng và minh bạch.
https://viagrameilleurprix.com/# Sildenafil teva 100 mg sans ordonnance
pharmacie en ligne france pas cher
Сайт для женщин https://ramledlightings.com будь лучшей версией себя! Читай о моде, красоте, психологии, отношениях, материнстве и женском здоровье. Найди вдохновение и полезные советы для каждого дня!
Лучший портал для родителей https://geog.org.ua и детей! Читайте о воспитании, обучении, здоровье, детской психологии, играх и семейном досуге. Советы экспертов и практические рекомендации.
Портал о детях https://mch.com.ua полезно для родителей! Воспитание, здоровье, развитие, обучение, досуг, игры и семейные традиции. Экспертные советы, лайфхаки и полезные материалы для гармоничного роста малыша.
Твой женский сайт https://musicbit.com.ua о стиле, здоровье и вдохновении! Узнай секреты красоты, следи за модными новинками, развивайся, читай о психологии отношений и оставайся в гармонии с собой.
Pharmacie sans ordonnance: Acheter Cialis – pharmacie en ligne france livraison belgique
pharmacie en ligne france livraison belgique: pharmacie en ligne france – pharmacie en ligne avec ordonnance
pharmacie en ligne https://kamagrameilleurprix.shop/# pharmacie en ligne france livraison internationale
dark web marketplaces dark market list
darkmarket list darknet market list
darknet links darkmarket link
bitcoin dark web dark market 2025
darknet drug links best darknet markets
darkmarket link darknet markets onion address
darknet markets onion darknet drug links
Справочник лекарственных https://mikstur.com средств – полная информация о медикаментах! Описания, показания, противопоказания, дозировки, аналоги и инструкции по применению.
dark market dark websites
Портал о здоровье https://fines.com.ua все, что нужно для крепкого организма! Советы врачей, профилактика болезней, здоровое питание, спорт, психология, народная медицина и лайфхаки для долгой и активной жизни.
смотреть турецкий сериал сезон https://turkoff.pro
https://kamagrameilleurprix.com/# Achat mГ©dicament en ligne fiable
pharmacie en ligne sans ordonnance
Great article! We will be linking to this great article on our site. Keep up the great writing.
May I simply say what a relief to find a person that really understands what they’re discussing online. You definitely understand how to bring a problem to light and make it important. More people need to look at this and understand this side of the story. I can’t believe you’re not more popular since you certainly possess the gift.
https://t.me/top_casino_rf
trouver un mГ©dicament en pharmacie: Pharmacies en ligne certifiees – pharmacie en ligne avec ordonnance
dark web market urls dark websites
dark web sites dark web marketplaces
смотреть турецкий сериал качестве https://turkpro.top
турецкий сериал все серии подряд смотреть турецкие сериалы онлайн
турецкие сериалы на языке бесплатно https://proturkish.org
турецкий сериал смотреть бесплатно https://turokk.net
darknet markets 2025 darknet markets links
dark market url darknet marketplace
darknet market list dark websites
Viagra femme sans ordonnance 24h viagra sans ordonnance SildГ©nafil Teva 100 mg acheter
darknet markets dark market
darkmarket link bitcoin dark web
darknet markets dark web marketplaces
vente de mГ©dicament en ligne: pharmacie en ligne sans ordonnance – pharmacie en ligne pas cher
pharmacie en ligne france livraison belgique http://pharmaciemeilleurprix.com/# Pharmacie en ligne livraison Europe
сериал турецкий 3 сезон на русском http://turokk.net
dark web markets darknet market lists
dark web link dark web marketplaces
смотреть турецкие сериалы смотреть онлайн турецкие сериалы
турецкие сериалы на русском языке смотреть турецкие сериалы онлайн
турецкие сериалы бесплатно турецкие сериалы смотреть онлайн бесплатно
bitcoin dark web dark web drug marketplace
tor drug market darknet drugs
darkmarket 2025 darknet market