Welcome to the series of Deploying On AWS Cloud Using Terraform 👨🏻💻. In this entire series we will focus on our core concepts of Terraform by launching important basic services from scratch which will take your infra-as-code journey from beginner to advanced. This series would start from beginner to advance with real life Usecases and Youtube Tutorials.
If you are a beginner for Terraform and want to start your journey towards infra-as-code developer as part of your devops role buckle up 🚴♂️ and lets get started and understand core Terraform concepts by implementing it…🎬
Why to Use Terraform As Infra-As-Code Tool ??? 🤔
Infrastructure as code (IaC) tools allow you to manage infrastructure with configuration files rather than through a graphical user interface. IaC allows you to build, change, and manage your infrastructure in a safe, consistent, and repeatable way by defining resource configurations that you can version, reuse, and share.
Terraform is HashiCorp’s infrastructure as code tool. It lets you define resources and infrastructure in human-readable, declarative configuration files, and manages your infrastructure’s lifecycle. Using Terraform has several advantages over manually managing your infrastructure:
✦ Terraform can manage infrastructure on multiple cloud platforms.
✦ The human-readable configuration language helps you write infrastructure code quickly.
✦ Terraform’s state allows you to track resource changes throughout your deployments.
✦ You can commit your configurations to version control to safely collaborate on infrastructure.
How to Install Terraform on Windows
Goto Terraform official download page to install at binary here and you will land on below page
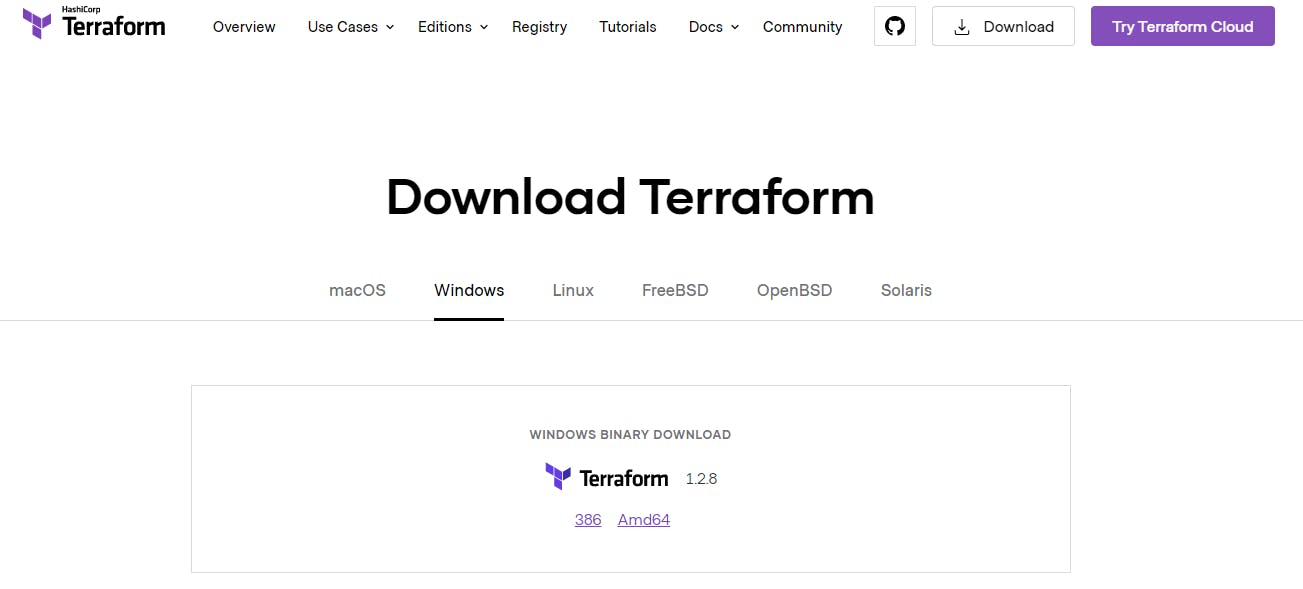
2. In this landing page select your binary 386/Amd64 based on your machine and it will download a zip file.
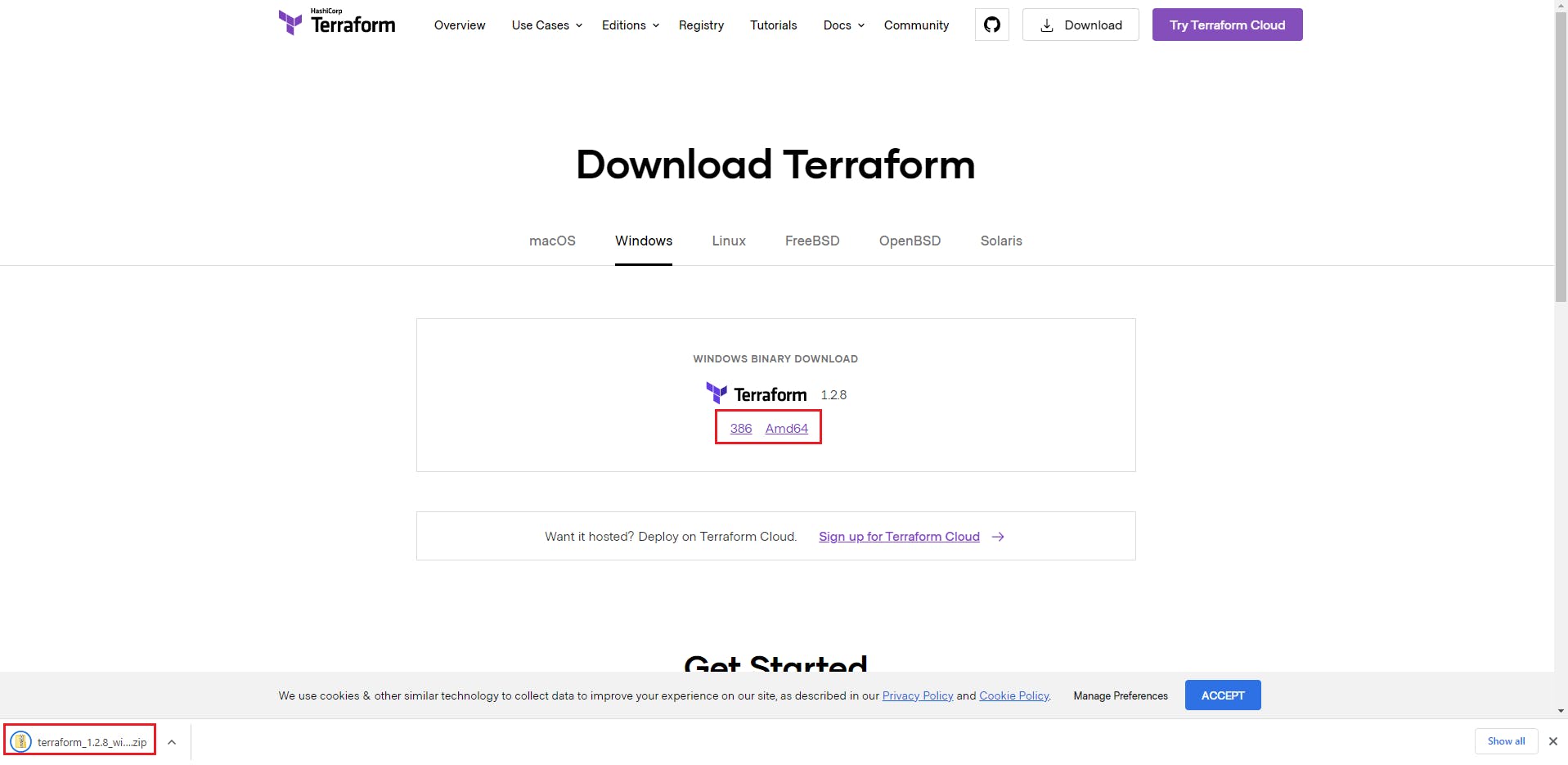
3. Now create a folder on the C/D whichever drive you want, I will go with D:\Software\Terraform. Download the zip file in this folder. Unzip the file to extract the .exe file
4. Now goto system environment variable and add path under environment variable.
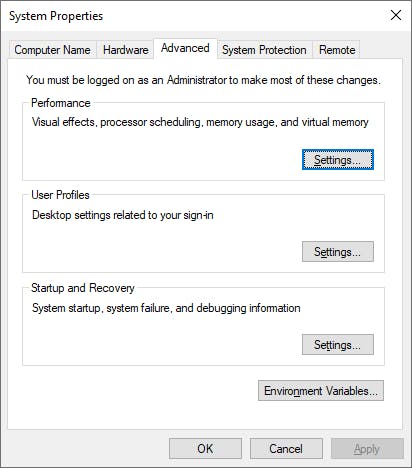
Now click on path and click edit
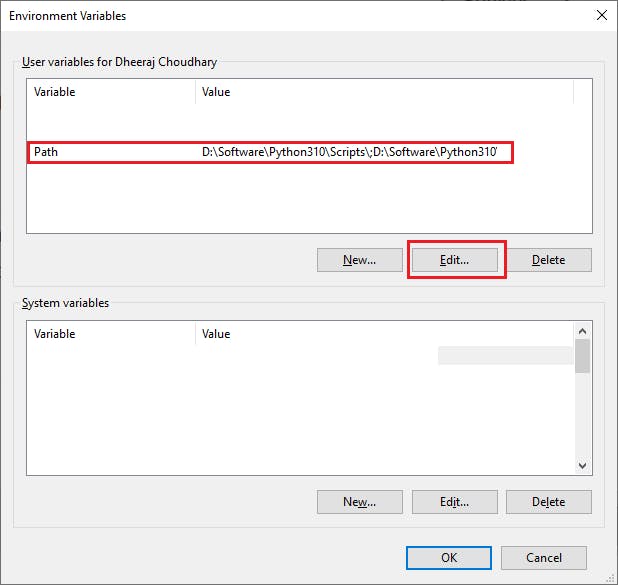
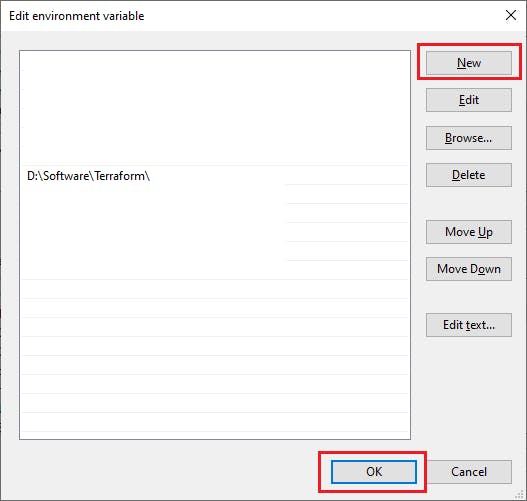
Click on new add the path where we unzipped the terraform binary and press OK
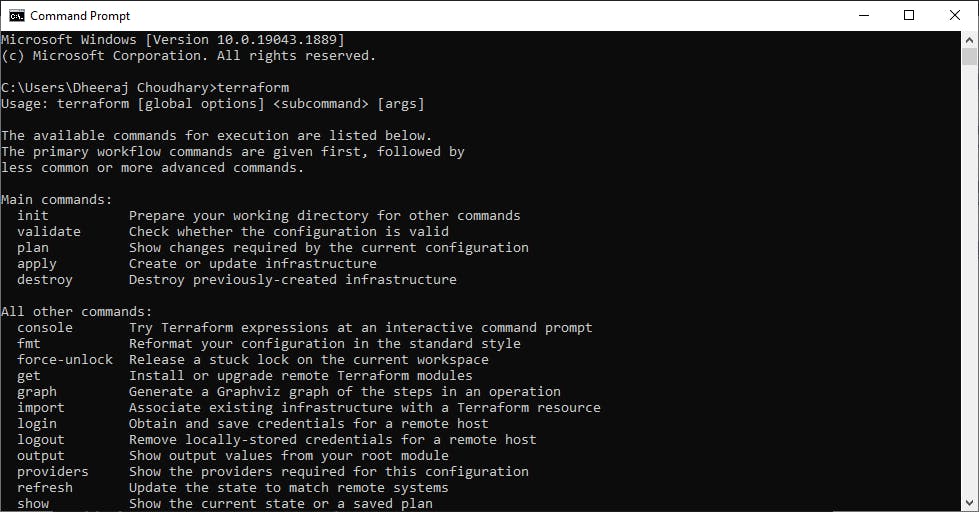
5. Open a Command prompt/Powershell and run this command to verify Terraform is installed successfully:
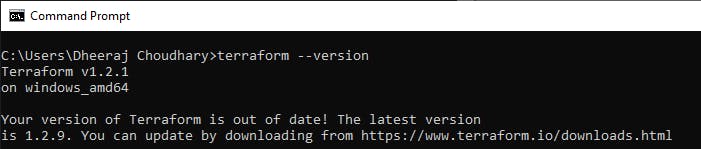
To check your terraform version use below command
Install Terraform extension in VS code
2. Goto extensions
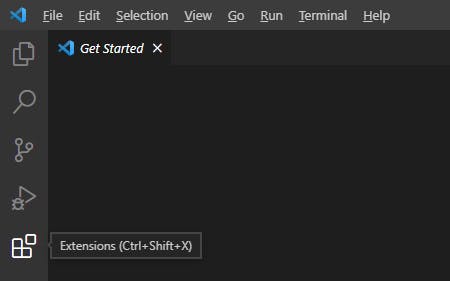
3. Install below two extensions from vs code market place
✦ Terraform Autocomplete
✦ HashiCorp Terraform
Download, Install & Configure AWS CLI on Windows 👁🗨👁🗨
❗️❗️Important Documentation To Be Viewed❗️❗️
⛔️ Hashicorp Terraform
⛔️ AWS CLI
⛔️ Hashicorp Terraform Extension Guide
⛔️ Terraform Autocomplete Extension Guide
🥁🥁 Conclusion 🥁🥁
In this blog, I have covered prerequisites that would be required as part of this series, to begin with VS Code Extensions.
📢 Stay tuned for my next blog…..
So, did you find my content helpful? If you did or like my other content, feel free to buy me a coffee. Thanks.

Author - Dheeraj Choudhary
RELATED ARTICLES
Automate S3 Data ETL Pipelines With AWS Glue Using Terraform
Discover how to automate your S3 data ETL pipelines using AWS Glue and Terraform in this step-by-step tutorial. Learn to efficiently manage and process your data, leveraging the power of AWS Glue for seamless data transformation. Follow along as we demonstrate how to set up Terraform scripts, configure AWS Glue, and automate data workflows.
Automating AWS Infrastructure with Terraform Functions
IntroductionManaging cloud infrastructure can be complex and time-consuming. Terraform, an open-source Infrastructure as Code (IaC) tool, si ...