Deploy AWS Cloudformation Templates Using AWS CLI | Create NACL, Inbound & Outbound Routes, Security Group & Associate With Subnet
Table of contents
- ❗️❗️❗️ Pre-Requisite ❗️❗️❗️
- 🌟Launch NACL, Inbound & Outbound Routes And Associate With Subnet🌟
- 👁🗨👁🗨 YouTube Tutorial 📽
- 🌟Deploy Security Group🌟
- 👁🗨👁🗨 YouTube Tutorial 📽
- ❗️❗️Important AWS Documentation To Be Viewed❗️❗️
- 🥁🥁 Conclusion 🥁🥁
- 💫Cloudformation Series Sequence💫
- ⌛️Realtime Usecases Cloudformation Templates⏳
- 👨🏻💻Cloudformation Github Repository👨🏻💻
Welcome back to the series of AWS Cloudformation For Beginners 👨🏻💻. In this blog we will be deploying AWS NACL, Inbound & Outbound Routes, Security Group & Associate With Subnet.
If you are a beginner and want to start your journey towards infra-as-code developer as part of your devops role buckle up 🚴♂️ and lets get started and understand core cloudformation concepts by implementing it...🎬
❗️❗️❗️ Pre-Requisite ❗️❗️❗️
1️⃣ Add visual studio code extension [Mandatory]
2️⃣ Adding VS Code Indentation Extension For Cloudformation Templates [Optional]
3️⃣ Deploy VPC, IGW & Associate [Mandatory]
4️⃣ Deploy only public subnet template from below blog [Mandatory]
🌟Launch NACL, Inbound & Outbound Routes And Associate With Subnet🌟
Create NACL, NACL Inbound & Outbound Routes And Associate Nacl With Subnet
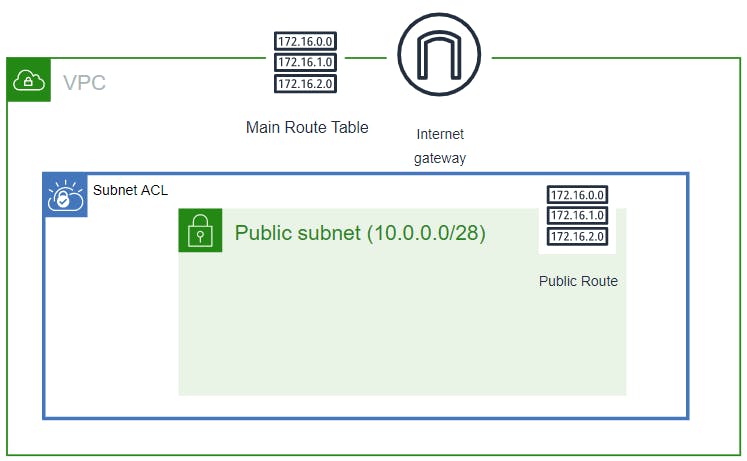 🔳 Parameters:-
🔳 Parameters:-
✦ CustomVPC :- Using this parameter for VPC "AWS::EC2::VPC::Id" we can list existing VPC list into the account and select anyone from them. Apart from this list we can also you default value if no value is selected in the parameter.
✦ PublicSubnet: Using this parameter for Subnet "AWS::EC2::Subnet::Id" we can list existing subnet list from the account and select anyone from them. Apart from this list we can also you default value if no value is selected in the parameter.
🔳 Resources
✦ MyNACL:- As part of this resource we use type "AWS::EC2::NetworkAcl".
✦ InboundRule & OutboundRule:-. Specifies an entry, known as a rule, in a network ACL with a rule number you specify. Each network ACL has a set of numbered ingress rules and a separate set of numbered egress rules.
✦ mySubnetNetworkAclAssociation:-Associates a subnet with a network ACL.
🔳 Outputs: Its always a best practice to print output for your resources.
✦ outputNACL: A reference to the created NACL.
✦ outputInboundRule: A reference to the created NACL Inbound Rule.
✦ outputEipforNatGateway: A reference to the created EipforNatGateway.
✦ outputNACLOutboundRule: A reference to the created NACL Outbound Rule.
✦ outputNACLSubnetNetworkAclAssociation: A reference to the created NACL Subnet NetworkAcl Association.
Parameters:
CustomVPC:
Description: Select One VPC available in your existing account
Type: AWS::EC2::VPC::Id
Default: "<your default VPC ID>"
PublicSubnet:
Description: Select one public subnet available in your existing account
Type: AWS::EC2::Subnet::Id
Default: "your default public subnet id"
Resources:
MyNACL:
Type: AWS::EC2::NetworkAcl
Properties:
VpcId: !Ref CustomVPC
Tags:
- Key: Name
Value: Nacl
InboundRule:
Type: AWS::EC2::NetworkAclEntry
Properties:
NetworkAclId:
Ref: MyNACL
RuleNumber: 100
Protocol: 6
RuleAction: allow
CidrBlock: 172.16.0.0/24
PortRange:
From: 22
To: 22
OutboundRule:
Type: AWS::EC2::NetworkAclEntry
Properties:
NetworkAclId:
Ref: MyNACL
RuleNumber: 100
Protocol: -1
Egress: true
RuleAction: allow
CidrBlock: 0.0.0.0/0
mySubnetNetworkAclAssociation:
Type: AWS::EC2::SubnetNetworkAclAssociation
Properties:
SubnetId:
Ref: PublicSubnet
NetworkAclId:
Ref: MyNACL
Outputs:
outputNACL:
Description: A reference to the created NACL
Value: !Ref MyNACL
outputInboundRule:
Description: A reference to the created NACL Inbound Rule
Value: !Ref InboundRule
outputNACLOutboundRule:
Description: A reference to the created NACL Outbound Rule
Value: !Ref OutboundRule
outputNACLSubnetNetworkAclAssociation:
Description: A reference to the created NACL Subnet NetworkAcl Association
Value: !Ref mySubnetNetworkAclAssociation
🔊 To view entire github code click here
1️⃣ Lets validate our template 👨💻
aws cloudformation validate-template --template-body file://<file path>
2️⃣ After successfull template verification lets create stack using our template 👨💻
aws cloudformation create-stack --stack-name naclwithsubnetassociation --template-body file://<file path>
Note:- If you are not providing default vpc id in parameter then you will have to use below command
aws cloudformation create-stack --stack-name naclwithsubnetassociation --template-body file://<file path> --parameters ParameterKey=CustomVPC,ParameterValue=<VPC ID>
3️⃣ Check if the stack we created via template is completed successfully 👨💻
aws cloudformation list-stack-resources --stack-name naclwithsubnetassociation
4️⃣ Describe stack and its resources to view its properties 👨💻
aws cloudformation describe-stacks --stack-name naclwithsubnetassociation
aws cloudformation describe-stack-resources --stack-name naclwithsubnetassociation
5️⃣ Check events for stack formation 👨💻
aws cloudformation describe-stack-events --stack-name naclwithsubnetassociation
👁🗨👁🗨 YouTube Tutorial 📽
🌟Deploy Security Group🌟
🔳 Resources
✦ InstanceSecurityGroup:- As part of this resource we use type "AWS::EC2::SecurityGroup".Specifies a security group. To create a security group, use the VpcId property to specify the VPC for which to create the security group.
🔳 Outputs: Its always a best practice to print output for your resources.
✦ outputInstanceSecurityGroup: A reference to the created security group.
Resources:
InstanceSecurityGroup:
Type: AWS::EC2::SecurityGroup
Properties:
GroupDescription: Enable SSH access and HTTP access on the inbound port
GroupName: AllowAllTraffic
SecurityGroupIngress:
- IpProtocol: tcp
FromPort: 80
ToPort: 80
CidrIp: 0.0.0.0/0
- IpProtocol: tcp
FromPort: 22
ToPort: 22
CidrIp: 0.0.0.0/0
Outputs:
outputInstanceSecurityGroup:
Description: A reference to the created security group
Value: !Ref InstanceSecurityGroup
To view entire github code click here
1️⃣ Lets validate our template 👨💻
aws cloudformation validate-template --template-body file://<file path>
2️⃣ After successfull template verification lets create stack using our template 👨💻
aws cloudformation create-stack --stack-name launchsecuritygroup --template-body file://<file path>
3️⃣ Check if the stack we created via template is completed successfully 👨💻
aws cloudformation list-stack-resources --stack-name launchsecuritygroup
4️⃣ Describe stack and its resources to view its properties 👨💻
aws cloudformation describe-stacks --stack-name launchsecuritygroup
aws cloudformation describe-stack-resources --stack-name launchsecuritygroup
5️⃣ Check events for stack formation 👨💻
aws cloudformation describe-stack-events --stack-name launchsecuritygroup
👁🗨👁🗨 YouTube Tutorial 📽
❗️❗️Important AWS Documentation To Be Viewed❗️❗️
⛔️ AWS::EC2::VPC
⛔️ AWS::EC2::NetworkAcl
⛔️ AWS::EC2::Subnet
⛔️ AWS::EC2::NetworkAclEntry
⛔️ AWS::EC2::SubnetNetworkAclAssociation
⛔️ AWS::EC2::SecurityGroup
⛔️ Condition functions
🥁🥁 Conclusion 🥁🥁
In this blog I have covered 2 scenarios in which we will create
✦ AWS NACL, NACL Inbound & Outbound Routes And Associate Nacl With Subnet
✦ Security Group
I have used AWS CLI command to deploy these template and trust me AWS CLI is the realtime hero and I would suggest you to get acquainted towards it. Stay with me for the next release.
📢 Stay tuned for my next blog.....
🎊So, did you find my content helpful? If you did or like my other content, feel free to buy me a coffee. Thanks. 🎊
💫Cloudformation Series Sequence💫
🔰 Deploy VPC With Internet Gateway & Associate I
🔰 Public, Private Subnet & Route Table Creation & Association II
🔰 Private Subnet,Nat Gateway, Elastic Ip, Private Route Table & Associate III
🔰 NACL, Inbound & Outbound Routes, Security Group & Associate With Subnet IV
🔰 EC2 With Security Group & User Data & Mapping V
🔰 Target Group, Elastic Load Balancer & ELB Listener VI
🔰 Build Web Application Layer With AWS CloudFormation VII
⌛️Realtime Usecases Cloudformation Templates⏳
💨 Schedule Automatic Detection Of Unused AWS EBS Volumes & Notify
💨 Schedule Automatic Detection Of Non Associated AWS Elastic IP's In AWS Account On Weekly Basis And Notify
💨 Schedule Automatic Deregistration Of AWS AMI On Weekly Basis And Notify


